Business Email Compromise
Learn about BEC and protect your organization with resources from Cofense
#1
Number one cybercrime for financial losses for 7 consecutive years
177
There are BEC victims in 177 of 195 countries around the world
$400B
BEC has resulted in over $400 billion stolen from victims globally
BEC Corner

Ronnie Tokazowski
If someone whispers the letters “B”, “E”, and “C” somewhere on the internet, chances are that Ronnie’s name comes up. Stemming from the days before APT was a buzzword, Ronnie has spent the last 6 years fighting and advocating for all things Business Email Compromise. He likes pointing to big numbers, says we need to start caring about each other to fix this problem, and can frequently be found posting memes on why the financial losses of BEC are worse than ransomware. (Aside from it being a cold fact, of course.)
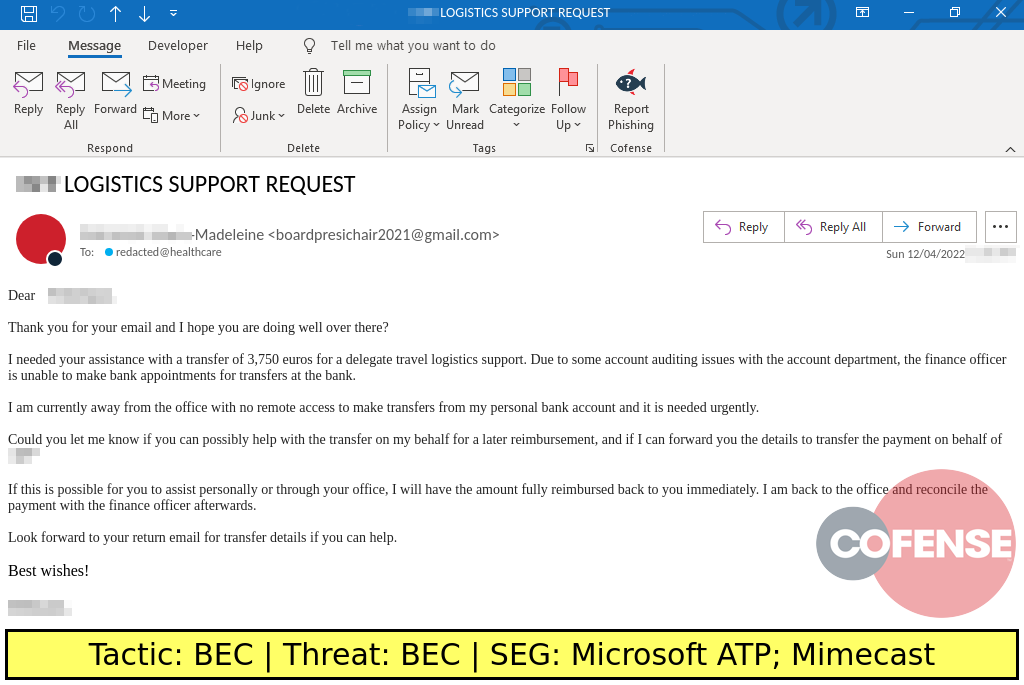
Real BEC Threats Secure Email Gateways Missed
Each week our analysts share a selection of real threats discovered in environments protected by Proofpoint and other SEGs. Here are some of the most recent BEC attacks we’ve found.
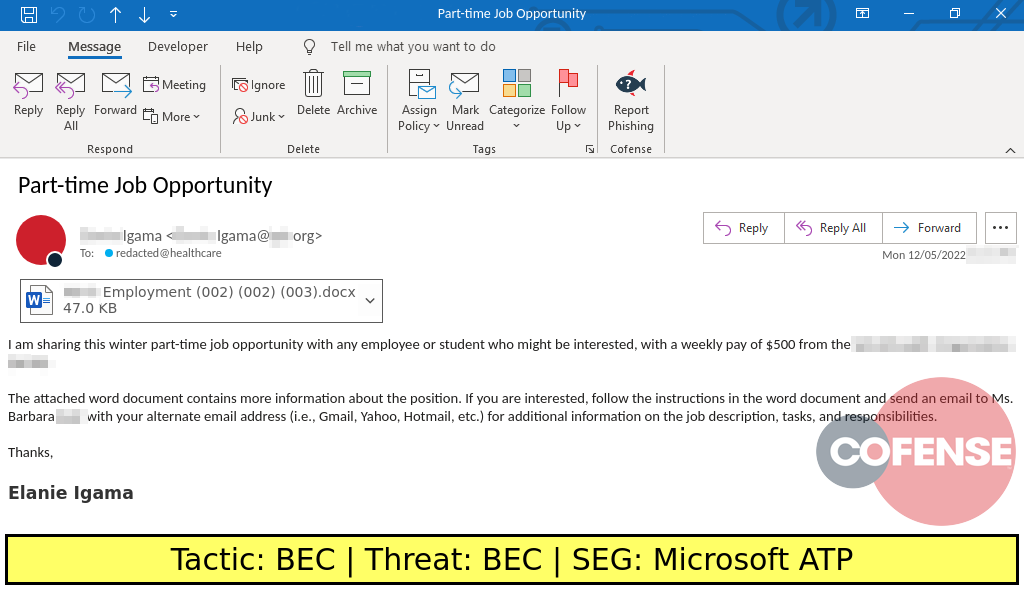
ENVIRONMENTS: Microsoft Defender for O365
TYPE: BEC
POSTED ON: 12/06/2022
TACTIC: BEC
THEME: Part time job-themed email
PHISHING EXAMPLE DESCRIPTION: Part time job-themed emails found in environments protected by Microsoft ATP deliver BEC. Specifically, the emails are likely seeking collaborators for a reshipping scam.
Business Email Compromise Overview
Business email compromise amounts to an estimated $500 billion-plus annually that’s lost to fraud. That’s billions lost to unemployment fraud. Billions lost to romance scams, real estate cons, advanced-fee fraud and dozens of other crimes affecting hundreds of thousands of victims. No single company can solve BEC, but awareness can help.
Spoofing
Something as simple as a “spoofed” email, where the display name in the email is modified to appear as an individual within an organization, when in reality, the return address is actually that of the attacker. The email format allows for a “display name” that doesn’t have to be related to the actual sender’s email address. This kind of format is less difficult to fraudulently use the name of a trusted individual. The message often appears to be sent from a senior staff member to someone at a lower level in the company, and the body of the email will imply a sense of urgency. Spoofing is the most common mechanism for payroll diversion attacks because it simply identifies an individual within an organization and sends an email to the payroll department asking for their bank account details to be updated.
What’s worse, suppliers and customers can be attacked using your organization’s email domain, which greatly impacts relationships, your organization’s reputation, and stakeholder trust.
Other BEC Methods
Then there’s the business email compromise where a legitimate user’s email account is compromised. Attacks can obtain user account details and then use those credentials to log into a user’s account. Sneaky attackers will sometimes set up forwarding rules to monitor a victim’s email conversations following the initial message. That gives the attacker the opportunity to step in at their leisure with urgent messages that appear authentic, making the attack even more convincing.
BEC is Big Money
These attacks pose a significant risk. According to the annual 2020 FBI Internet Crime Report, this phishing tactic has raked in nearly $2B this past year alone. But the damage caused by these attacks reaches well beyond financial losses. Fraudulent invoices, which are the most common of BEC attacks, the recipient gets what appears to be a legitimate invoice from an organization.
According to HelpNet Security, there was a 200% increase in business email compromise attacks focused on invoice or payment fraud from April to May 2020, posing an internal risk to organizations; and a reputation risk. As stated above, if a supplier or customer falls for a BEC attack that claims to come from a known organization, it can harm the established trust in the existing relationship as well.
How to Combat BEC
There are actions you can take to inform your employees to avert this threat. Educate your executive leadership team about this type of threat and discuss business email compromise with your organization at-large — especially those employees responsible for payments/payroll AND suppliers, customers, and clients. Training should include preventative strategies and reactive measures in case they are victimized. See our full checklist for details.
There is no single technology solution to BEC, rather it’s a combination of technology, process and user awareness.
What are the most common BEC scams?
In no particular order the four most common business email compromise scams include:
-
Fake invoicing, in which the hacker requests funds as a familiar supplier or service provider.
-
Wire fraud requests, in which the hacker pretender to be a senior executive handling urgent or confidential information.
-
Impersonating a lawyer, who like the wire fraud scam pretends to be handling confidential or time sensitive information.
-
Impersonating human resources, where the attacker is attempting to collect personally identifiable information (pii).
-
Knowing what to watch out for is the best defense any organization has. If something doesn’t feel right, it is always best to verify and authenticate the request before doing anything that might compromise you or your organization.
Protect Your Organization from BEC Attacks
Follow our checklist to ensure your organization stays protected.