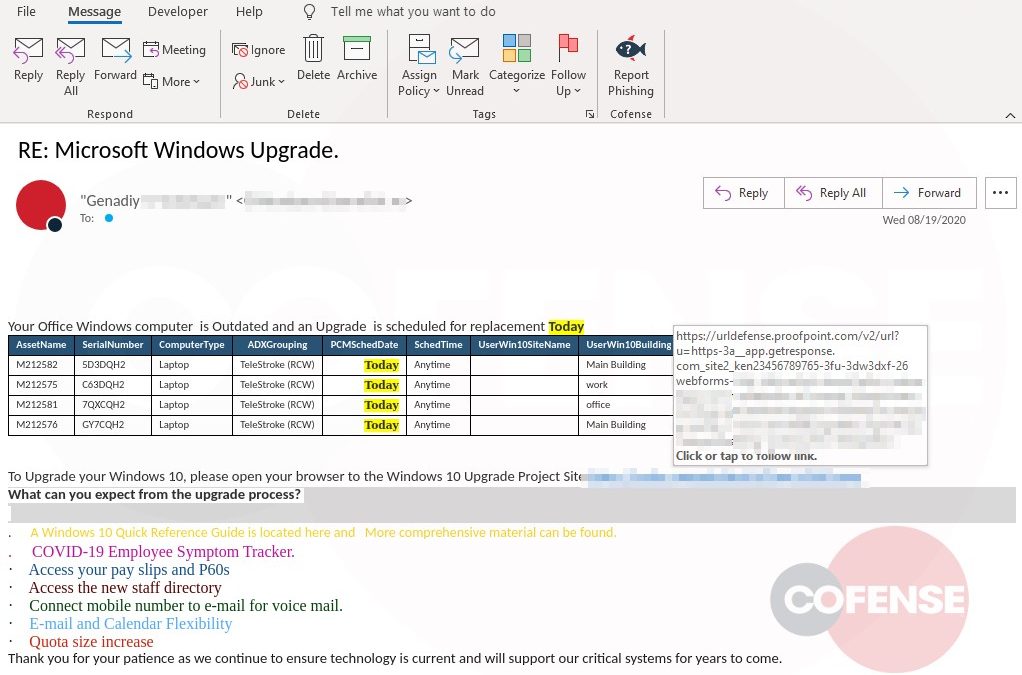
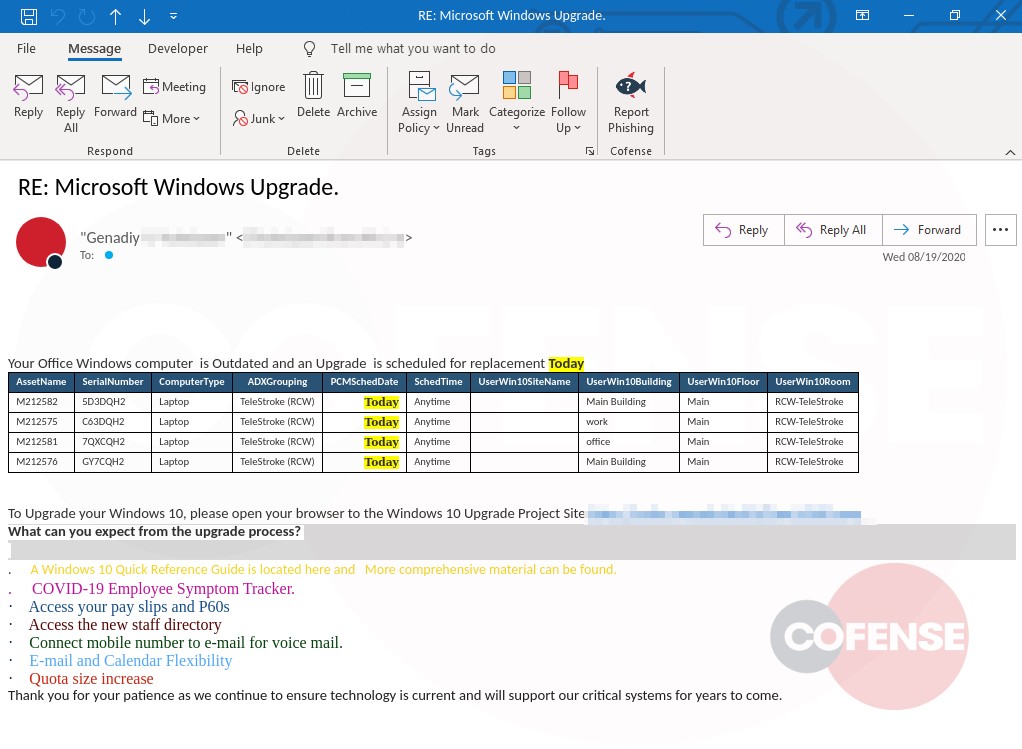
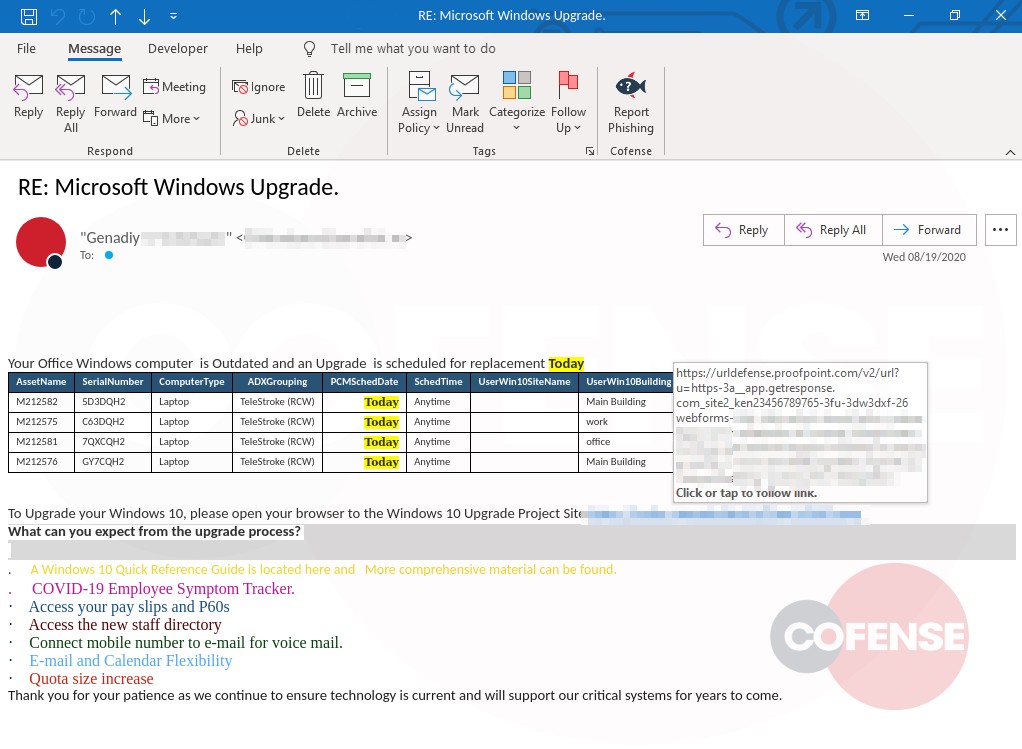
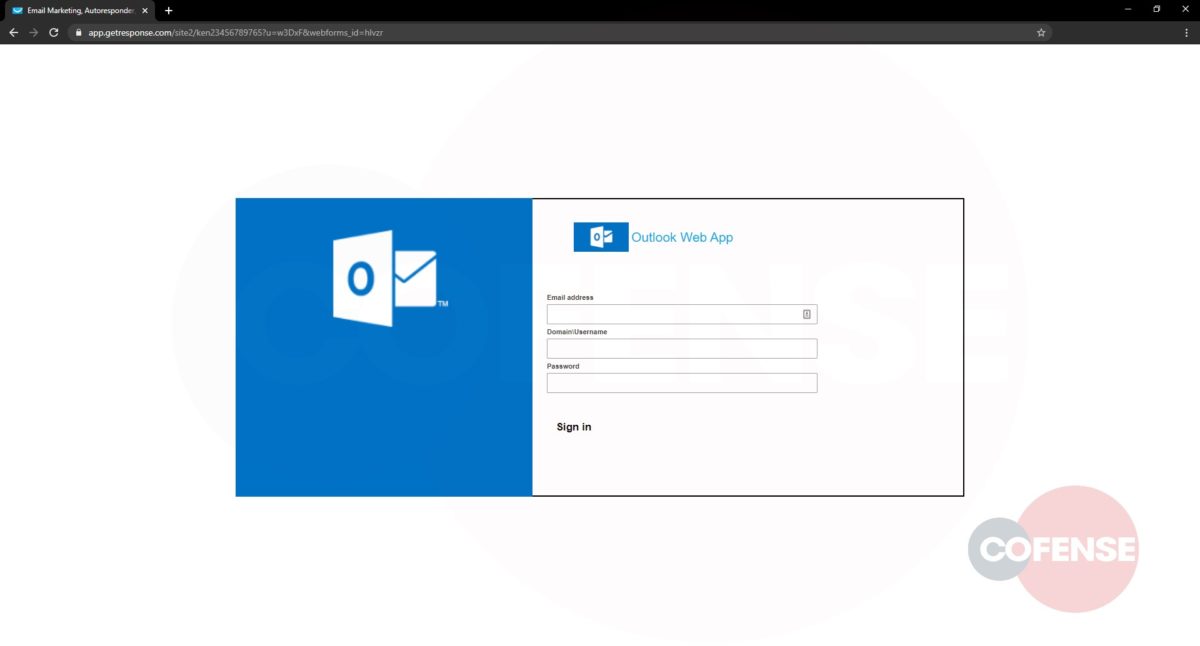
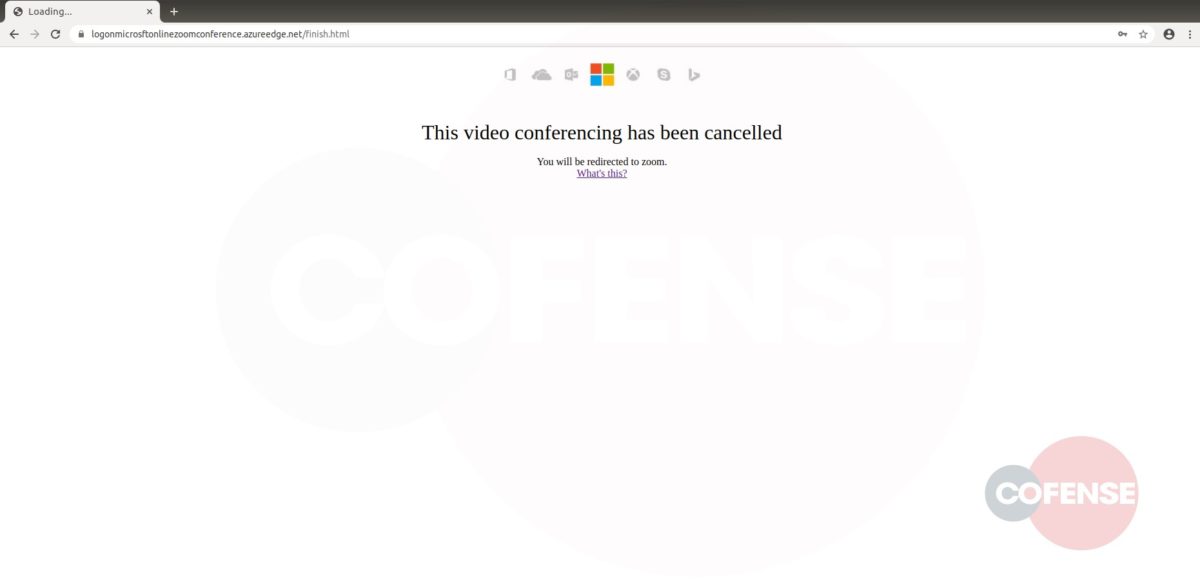
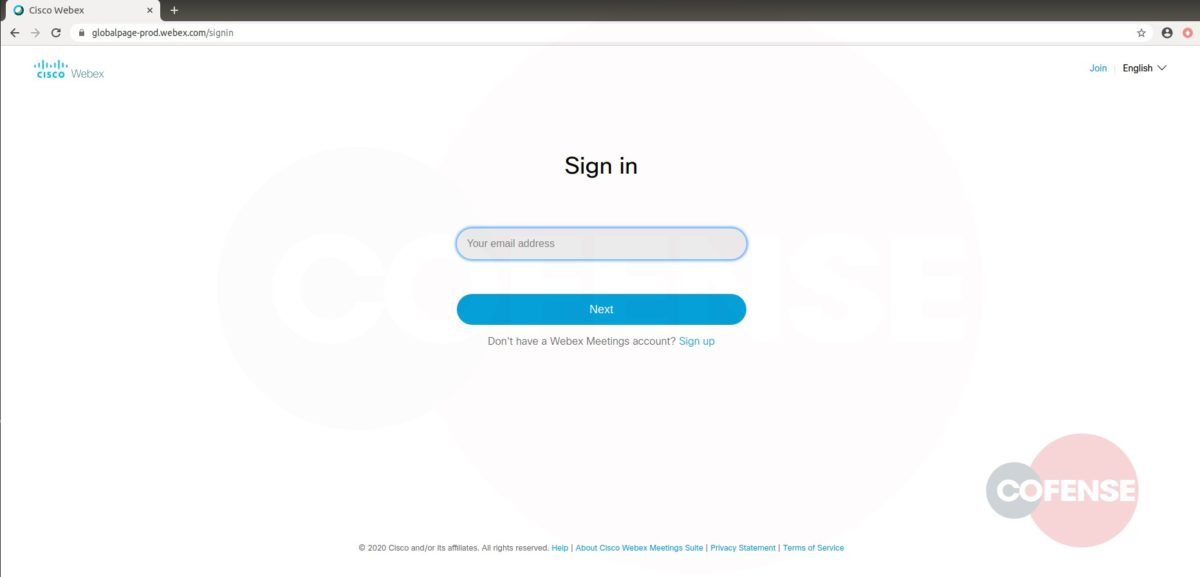
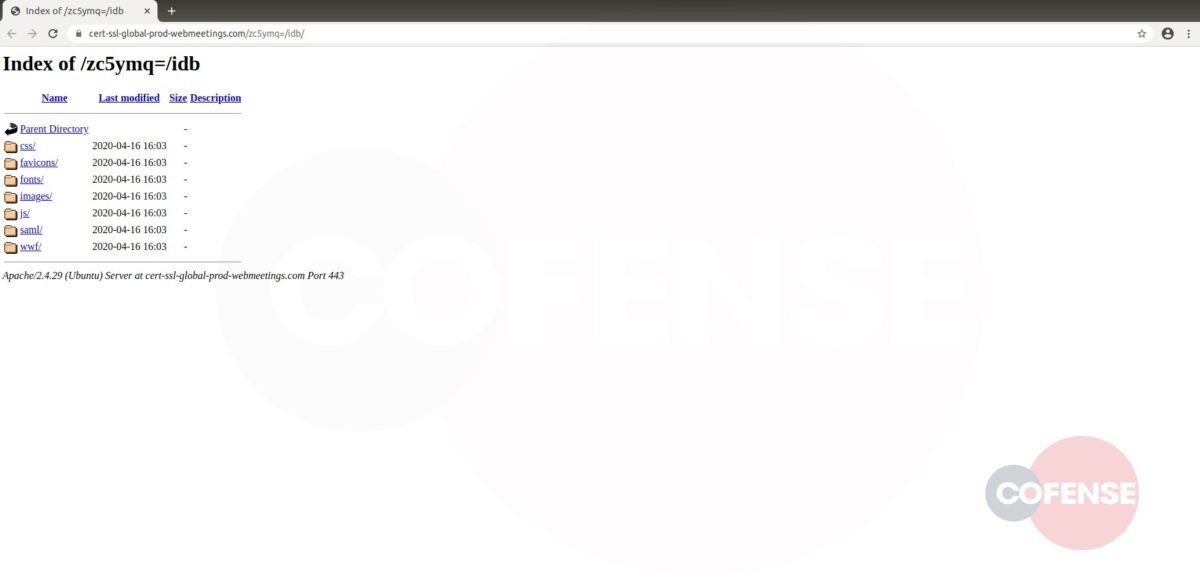
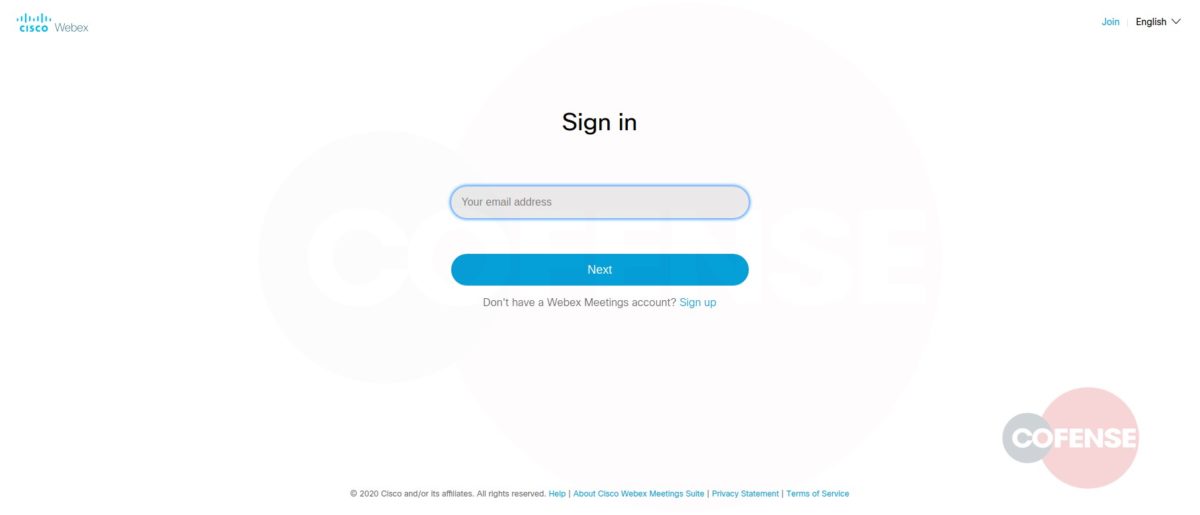
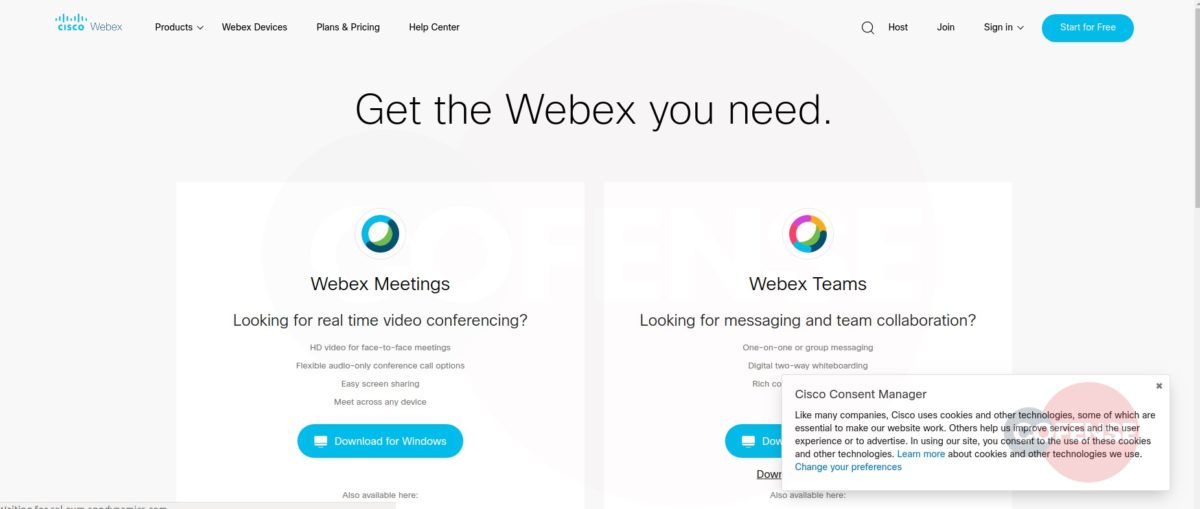
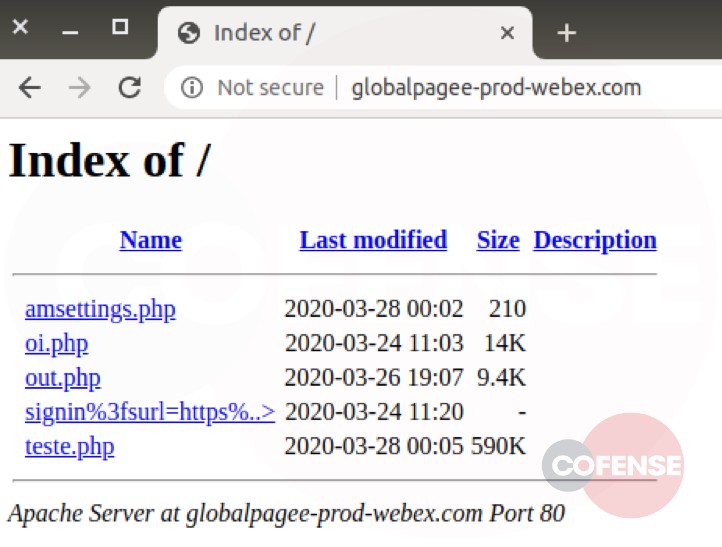
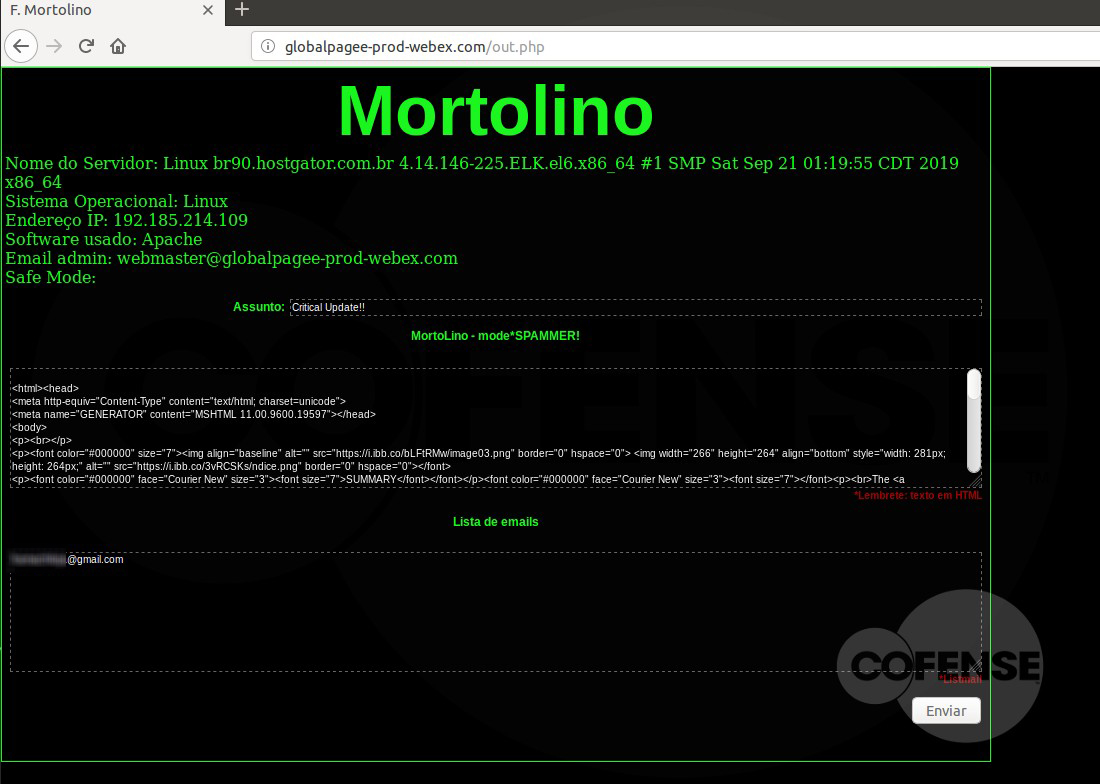
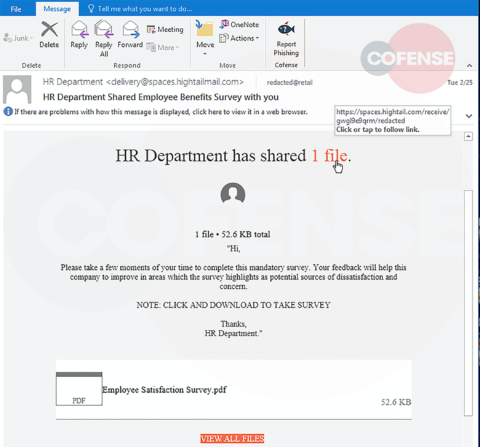
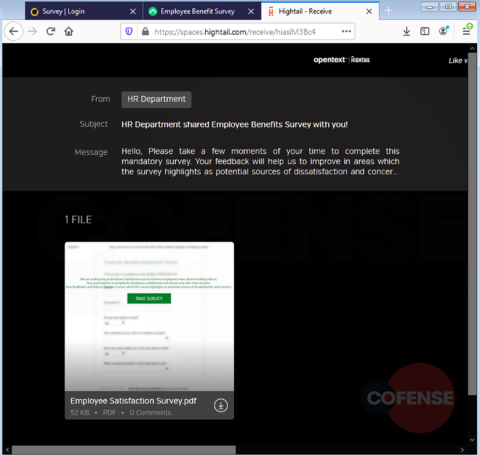
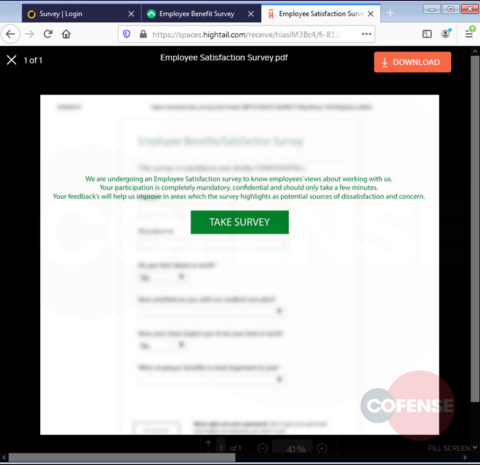
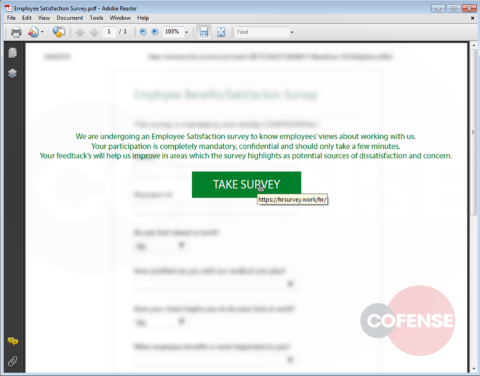
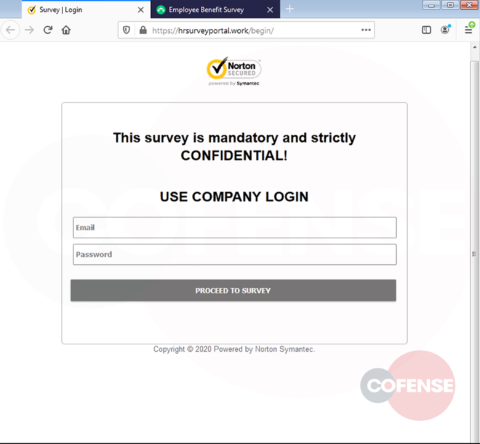
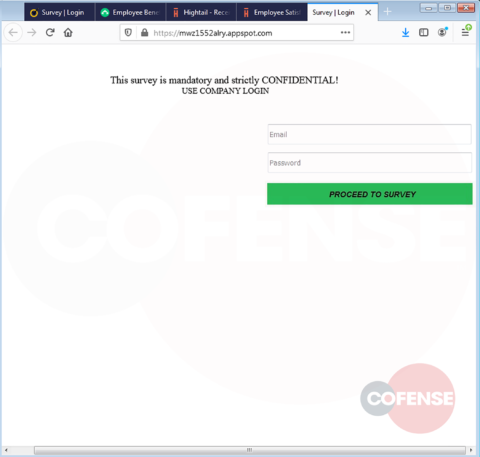
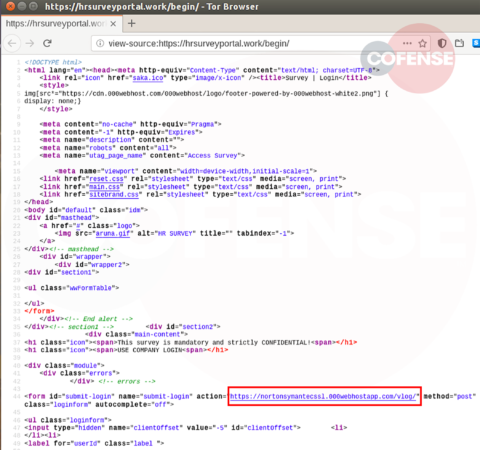
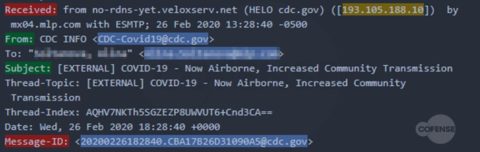
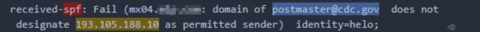
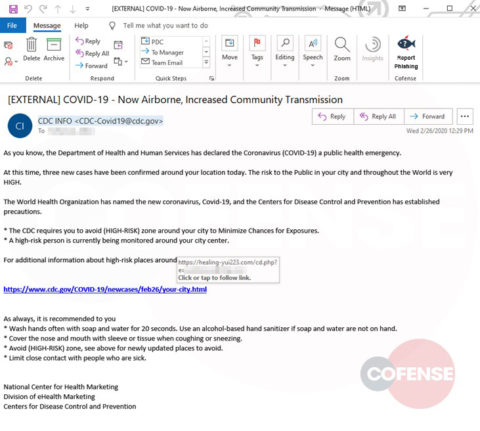
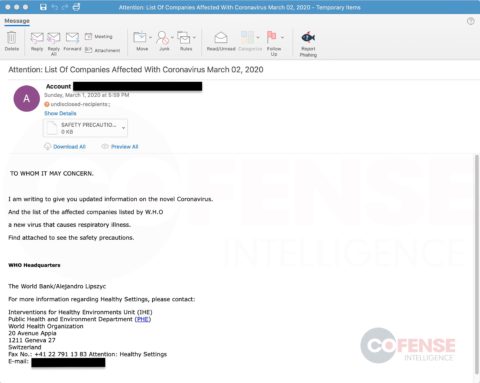
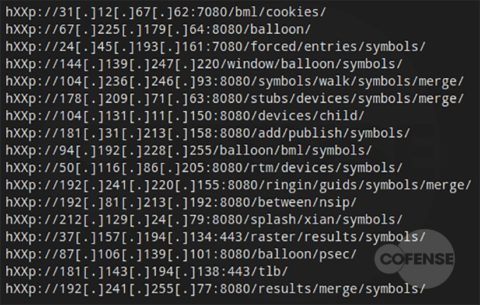
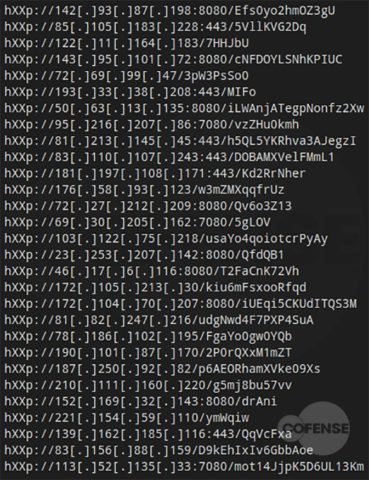
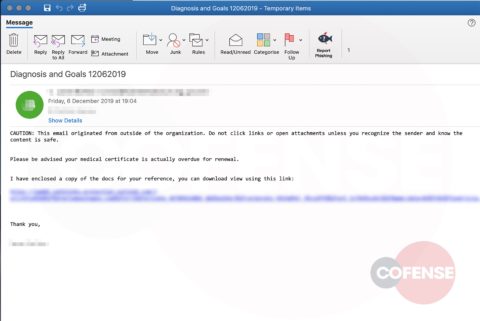
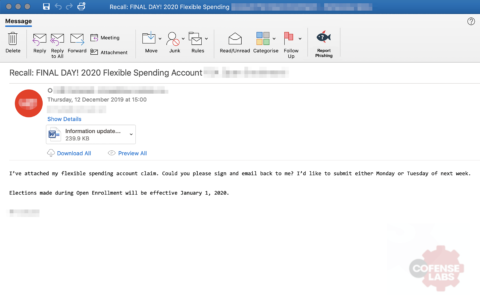
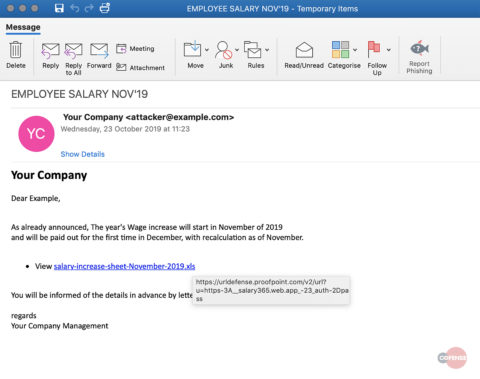
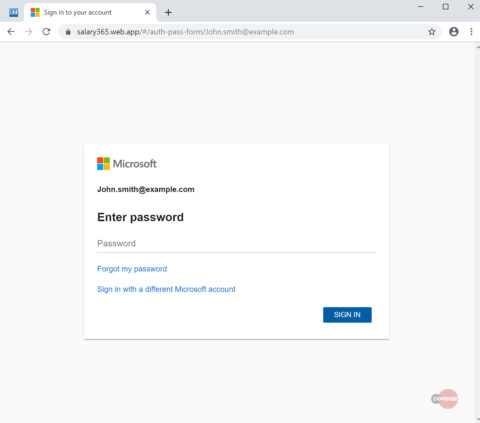
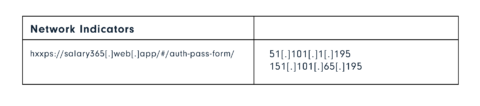hXXp://3mbapparel[.]com/ce8p4mw/Scan/23sr2r3h-227136449-4100-o7f3aukln-5ek9w7yx/
hXXp://abbasghanbari[.]com/cgi-bin/m2gx-j9l-2674/
hXXp://abis[.]abis-dom[.]ru/wp-content/multifunctional-zone/external-portal/XKnI9c95VXtO-2koeL1odjG8e45/
hXXp://adrianoogushi[.]com[.]br/blogs/available-resource/test-forum/CO37HIcUG-4KiqqruHlj9/
hXXp://agramarket[.]com/wp-admin/554841538461/9igxpru22w-3404-624501945-dtenc-cvona7/
hXXp://agramarket[.]com/wp-admin/images/Document/
hXXp://aijiuli[.]com/wp-content/common-3644746801311-F61eGi6VrRfSERpV/guarded-722116w-9jx99j5uyog/2b51q65tivz3f97-3vw70xy142675/
hXXp://alfaem[.]by/wp-includes/wcevu12a6j/ui13miem-1842496-647941-b1maguvyl7-0wm1/
hXXp://allgamers[.]ir/wp-content/6270900376591-TrHEgUBtm-sector/verified-portal/3rw-x42z0/
hXXp://aminulnakla[.]com/test/5mpub-u9jdh-1356/
hXXp://amoutleather[.]com/a/multifunctional_9313571_Y9mwVe/additional_forum/EAvHHxYA2_z07m8sM36w72/
hXXp://anantasquare[.]com/wp-content/Documentation/1yzenuu55v/zdx0oqd5mp-79785-92241-lqk84aode-i65yma2m1/
hXXp://andishkademedia[.]com/wp-includes/8vcppv-4l1-885316/
hXXp://anhjenda[.]net/wp-content/vmpyh5c3pi/
hXXp://anjumpackages[.]com/nrri/private_44709616882_WQZDa1KAyj/corporate_V6tkmPmj_jRcx2PfQ/on3_1v7649ys6t1/
hXXp://aquimero[.]net/wp-includes/8gdm6-y4kj-461/
hXXp://archinnovatedesigns[.]com/wp-includes/464728-V0rjOQkXZi4SSiW-disk/580333-3VP9JZcfWI6-cloud/028eeth-vu553tyw/
hXXp://arielcarter[.]com/j7foqo2/DOC/iqrh6hczo0cw/
hXXp://arttoliveby[.]com/yyrye/private_86192_eZoBMjbfcDvuPq/test_cloud/ws3uh67ha1tup_5128t108/
hXXp://auliskicamp[.]in/wp-admin/common_resource/verified_vZUVdO8ppY_CWfMSl2yMCEH/bgJEju1jvH_3iNK6o4Ii4G/
hXXp://awooddashacabka[.]com/yt46/open-box/individual-area/yNmy5HQif-8o8tG738h2/
hXXp://babdigital[.]com[.]br/wp-content/esp/6v5nej75l/
hXXp://bakeacake[.]com/wp-admin/available-disk/security-warehouse/z1XGaZ-NemjMNrc3a/
hXXp://bassigarments[.]com/wp-content/personal-592742204-WBrGGz/4469690-7SOBhN7gbB7s-area/b90h417-wtxsw/
hXXp://batdongsanhathanh[.]net/wp-admin/open-resource/568A8V-ILYyxINK-profile/jdux7bsdp-twyu179678t1/
hXXp://beiramarsushi[.]com[.]br/1g3ld9f/closed_n941_aUn1fAfrvX8Bhu/test_warehouse/6N1JhlV_M8oi1aM9Gyw/
hXXp://best-fences[.]ru/css/4ey-6v7y0-5856/
hXXp://betaoptimexfreze[.]com/bebkat/Reporting/9zooeodt/x827ofzp-289202990-87262-q99cri9-xr06/
hXXp://bgctexas[.]com/quietnightcompany/xb1k2g9/personal_zone/test_WlYEqat2Ie_OgiyQ9W40qCyP/bw54a4lhlrx_9636w4uu0xsxt1/
hXXp://bilgigazetesi[.]net/a6lwm1m/open_sector/special_forum/Ej4oMEQf3AN_Gudt5tx97J/
hXXp://bimattien[.]com/wp-admin/eTrac/ld6u234c3/ga438o-5744266-474284-eejhd-5ctewz/
hXXp://blicher[.]info/wp-includes/KPrV/
hXXp://blog[.]inkentikaburlu[.]com/70jjm53klo/sites/2yd7bvuh-505209-64670737-fr4vs-t7zp3cjl0/
hXXp://blog[.]sawanadruki[.]pl/wp-content/uilb8dz6_hwpeyvx_sector/security_warehouse/0gKrzfjYpvFO_3yLM891Meliz/
hXXp://blogkolorsillas[.]kolorsillas[.]com/wordpress/xnq1k-rkkl-803/
hXXp://bluemedgroup[.]com/wp-admin/mnfd8_nbij_436575782_UQEO1IVCs4LqadTV/security_profile/XODmvThQGR7_H7vrzccMec5/
hXXp://bmrvengineering[.]com/wp-admin/FILE/
hXXp://bookitcarrental[.]com/wordpress/INC/iddp2ggtm/eccvup8c-3843-818470-69yg4b28wh-w1kxriyo/
hXXp://bupaari[.]com[.]pk/RoyalAdventureClub[.]com/eTrac/ncevpoamvlp0/
hXXp://buyrealdocumentonline[.]com/wp/Documentation/d7mz-688402499-7314933257-fkwggnu-t4ybrvaf7/
hXXp://cabosanlorenzo[.]com/wp-load/protected-resource/verifiable-tk2c-3kfk3g9iz/ebub24rmzo8-9u88717yx935/
hXXp://cacimbanoronha[.]com[.]br/wp-content/Scan/
hXXp://caotruongthanh[.]com/wp-admin/qeku-4ys4-83891/
hXXp://carolscloud[.]com/media/public/
hXXp://carolzerbini[.]com[.]br/6ttp7t0/Overview/qoawf12j0jbp/
hXXp://carvalhopagnoncelli[.]com[.]br/lvqhz/Overview/0rrnguk8z/lg4qyh7-338411-43458560-pp7dts1ba-3msz/
hXXp://cas[.]biscast[.]edu[.]ph/updates/personal_sector/verifiable_warehouse/D3buvGg_1yyMJGrM6gp/
hXXp://casaquintaletcetal[.]com[.]br/e6viur/04383245_xZw1ZKxX_41063_29gQlRhcVl5eGs/additional_area/4004h_s035tt6461/
hXXp://casinovegas[.]in/cgi-bin/protected_module/additional_warehouse/NzQU7EbxmY_mLobpJqHn8Lh8/
hXXp://catchraccoons[.]com/wp-admin/open_9135304_x3VG052S9vjEZN/external_warehouse/AgnasV_o0M4JIrNt67j/
hXXp://caughtonthestreet[.]com/sh5bne/available_sector/test_mhc3xk01u_if5a3isqhztj4/fwpqcd9admvnur_yuu17s15/
hXXp://cetpro[.]harvar[.]edu[.]pe/dup-installer/2i5i_r76gl3x5v6vge_disk/individual_profile/NrWPp5_3Hj0zszymw/
hXXp://championretrievers[.]com/wp-admin/paclm/mdjx-81327-4043-zujiz-uoi7hp59w4/
hXXp://charger-battery[.]co[.]uk/chargerimages/Reporting/
hXXp://chatnwax[.]com/dir/RRETX2MC9ZE7/syc01o4x/
hXXp://cheappigeontraps[.]com/wp-admin/personal-resource/guarded-gueidxaiga-544/a4hko1sshe-6530yx62/
hXXp://cheapraccoontraps[.]com/wp-admin/parts_service/zn6iszxroew/0vqf-97169-6342681145-z9iyge-xws5/
hXXp://cherrypointanimalhospital[.]com/new/parts_service/po53iyxo22m/
hXXp://chintamuktwelfare[.]com/wuvke31kdk/open-array/open-space/j2hg7S-Mseglc5d/
hXXp://chongthamhoanglinh[.]com/cgi-bin/Reporting/
hXXp://chooseyourtable[.]sapian[.]co[.]in/wp-includes/x3qc-azmz9-340871/
hXXp://clurit[.]com/matematika/images/content/open-array/additional-portal/open-array/additional-portal/3qZqx-tb7HH2KcNhHi82/
hXXp://collegebolo[.]in/wp-content/OCT/i91smxgw72t/iayid-933690-003423-pxhqzu7z4-e9fxqjnvn/
hXXp://collegiatevideoscout[.]com/piq88y/multifunctional-zone/verifiable-portal/vzwsusvfoq2kbmt-y496uwt7xz68uy/
hXXp://compworldinc[.]com/browse/4ni6zf2fq/
hXXp://contestshub[.]xyz/wp-content/evfch-p40-368725/
hXXp://cosmeticsurgeoninkolkata[.]in/wp-content/multifunctional-zone/security-space/oG7v7CkLAl-jz0rugqbjvi73/
hXXp://cosmicconsultancy[.]in/custom-icons/Reporting/
hXXp://cp[.]3rdeyehosting[.]com/wp-includes/esp/
hXXp://crazyroger[.]com/cgi-bin/1710496674006_01bd6Zeef0mCJ_disk/external_forum/4dwy_zxz36x4/
hXXp://creatitif[.]com/wp-admin/Reporting/
hXXp://croptool[.]com/theblackjackmob/Documentation/
hXXp://crownedbynature[.]com/jtaa6jtb/LLC/
hXXp://csa[.]cries[.]ro/ckjca7/11206-JdwhXBh41Cj8irAC-resource/individual-warehouse/ay7fc9ll3dnke7e-4yw99s2t6w/
hXXp://csrngo[.]in/alfacgiapi/15vu8s-c85u1-9139/
hXXp://daisybucketdesigns[.]com/pocketframes/images/aci32rk/eTrac/5w4kiwqito3r/
hXXp://dalao5188[.]top/wp-content/open-sector/test-forum/f0pqn-5328/
hXXp://dastsaz[.]shop/wordpress/private_array/verifiable_forum/BpajlMaeH_297iwG6jj7pGc/
hXXp://datrienterprise[.]com/wp-content/eTrac/7qzoqzrkjyuc/
hXXp://demo[.]bragma[.]com/site/pt48-pk3089b-682065491-ZkL2pS9yz/open-warehouse/LXWiJKrI-62Hui1o9a/
hXXp://demo[.]podamibenepal[.]com/superior/t2c-jpip6-22/
hXXp://demo[.]tanralili[.]com/apehhpf/INC/
hXXp://designers-platform[.]com/binzbc/FILE/a69zlr8/
hXXp://dev[.]consolidationexpress[.]co[.]uk/wp-admin/closed_sector/924553_1wSxAW2z_portal/2EI6ej9js5j_15M1p7xI9Gov/
hXXp://diamondbreeze[.]com/wp-content/docs/ig220w-64348062-050708-0o2ix-nk0skuh0/
hXXp://diecinuevebn[.]com/cgi-bin/protected-disk/verified-forum/ah7hwmjvvuuy84mx-t467s/
hXXp://diegojmachado[.]com/cgi-bin/open_sector/CLp2Etz_eUR1Q6uDDBgHkI_area/bDuOHXDda_cgI6sNcjl1gK/
hXXp://dishekimieroluzun[.]com/wp-content/DOC/
hXXp://dreammotokolkata[.]com/cqye/iaft92-6lplx-826/
hXXp://drsudhirhebbar[.]com/minds/private-sector/open-portal/rb2vj1kuwjbb-swuys/
hXXp://dubit[.]pl/site2/pxre-ns-297/
hXXp://dumann[.]com[.]br/z3gy5lb/sites/7bg1i8n2/jvsjhn3j-868085891-343651-sgosfko-20u4kmz2cb/
hXXp://elitexpressdiplomats[.]com/cgi-bin/available-array/guarded-5UJi7-pIM1v1g3Q6k6/whf6zxh-txsts2/
hXXp://empowerlearning[.]online/wp-admin/ruh006-rgkj-590/
hXXp://especialistassm[.]com[.]mx/inoxl28kgldf/docs/l5rbj6g/iibea-032709148-341719111-6r6auusna-6j9m/
hXXp://euonymus[.]info/twxppk/Document/7uo0t4osm95p/
hXXp://evokativit[.]com/TEST777/YHErlTl/
hXXp://evolvedself[.]com/dir/azpdj41_sugzd3yhwwsy_3709679_Rvta29FrYib/special_QDPYSSWZ1L_PJAv0ICNK1P/2Edulb_98mGeuzy3ty2Lz/
hXXp://extend[.]stijlgenoten-interactief[.]nl/test/Pages/w6014u-84395-6469-hthslxcbne-8vj2et4/
hXXp://finndonfinance[.]com/wp-content/Document/wjswrn1s/qgltg-85747767-49820504-2gz892-ydp6o4o4e/
hXXp://fooladshahr[.]simamanzar[.]ir/dup-installer/closed_box/interior_portal/0f6j5b5bga_06zs0/
hXXp://fozet[.]in/wp-content/eTrac/hb6yb86ei36/yrqsf32-172576671-4195092231-c97ty6f-5cu2q8hj8/
hXXp://freestyle[.]hk/picture_library/eTrac/s9shv2eo/
hXXp://frezydermusa[.]com/wp-content/parts_service/fisq814goap0/fhyl68-5565-326796-rr55j9spg-ug9mfyg/
hXXp://galeriariera[.]cat/assets/lm/g9zkvryjwq-0524005005-0333576-k58dqx5-326yx/
hXXp://gameonline11[.]com/wordpress/pqOAPS/
hXXp://gargchaat[.]com/phpmailo/lm/538skcfoe/7vps0iy-66657310-44075-q2gbc4-2vhp2c/
hXXp://gayweddingsarasota[.]com/cgi-bin/esp/68f6yd4ehwdr/
hXXp://gayweddingtampabay[.]com/cgi-bin/private-2828581710383-rNH3ETP8sT2ggXrt/additional-forum/DEsne0OE5vz-KmmglLMf/
hXXp://geekmonks[.]com/cgi-bin/common_sector/special_forum/9cfuf_ts9y4twzx0709/
hXXp://germxit[.]mu/calendar/4rxl-2932-78/
hXXp://gestto[.]com[.]br/wp-lindge/Scan/
hXXp://getabat[.]in/wp-content/closed_module/test_88i6oai_sjwnuscqjjl/abgyQKwZhv6i_inKjGl8hG98/
hXXp://globalstudymaterial[.]com/pdf/available-zone/individual-warehouse/vWOq8gdCRu0-ra1nf24iHayat/
hXXp://goldinnaija[.]com/wp-admin/sites/xaz6-030261-0911995608-sm9u-99rd1/
hXXp://gomaui[.]co/wp-includes/personal-resource/test-area/a9kj-wsuyvw59t/
hXXp://grace2hk[.]com/b6vg89hb/common_sector/security_forum/4tx_uu501xxxs/
hXXp://grahaksatria[.]com/towed/private_box/additional_forum/x1T0kdo_q89uLjatbqJ8/
hXXp://greatercanaan[.]org/wp-admin/Document/kqfz63hy/
hXXp://grocery2door[.]com/nkpk/97_dwi59_03276182_sJsjrqR/corporate_warehouse/13wrnaGqqET_lIy0l5eJsNdIc/
hXXp://groovy-server[.]com/masjid/backend/web/assets/rhhl/
hXXp://group8[.]metropolitanculture[.]net/wp-admin/multifunctional-sector/verifiable-cloud/l0q-4vww/
hXXp://haoyun33[.]com/wordpress/browse/9kmt2hi/
hXXp://hasung[.]vn/wp-includes/1bvxk7fvre5_lnci6bcnim_resource/special_forum/5BZ0CZ_p4052N871e/
hXXp://hfn-inc[.]com/mail/available-box/security-PgUqz6ktI-GY00tgjAgbFSr5/zy5escaf56fzw5y-y78s2tzu60v7z4/
hXXp://homecarehvac[.]com/wp-includes/open_resource/guarded_profile/eshftvv0ht_61x297v2/
hXXp://indusautotec[.]com/n8l7suy/open-xNFfQ20VO-FjqtokyzbQ6HGF/security-jdEM-dDzAJO2Ccnx/G3P8qq-MmI2GLf3JdK/
hXXp://jgx[.]xhk[.]mybluehost[.]me/scarcelli/multifunctional_098152347732_CYNEZ9DFQ/guarded_space/2qq1r_29xuz/
hXXp://jurness2shop[.]com/cgi-bin/private_disk/individual_ufyGUNB_QRlHjxmYMMbuaY/30lpuw22llwzm_vx60vx4s/
hXXp://kallinsgate[.]com/cw6vmaj/common-2561851-hLdPAOsBNVrNeE/open-space/5irmsa8-8x82zv7t2zw2x/
hXXp://kanntours[.]com/wp-security/Overview/yprr0k8-808004671-920995225-dc1d7q7-trbbwtd/
hXXp://kayzer[.]yenfikir[.]com/quadra[.]goldeyestheme[.]com/lm/
hXXp://kelurahanraya[.]ulvitravel[.]com/tmp/eTrac/wpag9c-3294986-0565941971-rbtkv0yr0p-rs604o/
hXXp://kpu[.]dinkeskabminsel[.]com/wp-admin/available_229278636_TO7LG1kXBWax3/847166_Zm9B3oXaP_portal/ZcAtrKAnB_nJGzswNc/
hXXp://kyrmedia[.]com/whnh/closed_zone/test_warehouse/o1yvycunyw222_tz6z71svs35/
hXXp://lalletera[.]cat/bootstrap/closed-array/test-warehouse/9y3rm68-7251/
hXXp://lastminuteminicab[.]com/l56mcv/Scan/qrg67fldazss/cd38ot-8952552-5429276851-63g720il-z2uwrr/
hXXp://lindamarstontherapy[.]com/psqlud/common_1810413_gc4qCpSFYbBM/additional_forum/4kmyjjijspz85_tt20x6w/
hXXp://liveleshow[.]com/cgi-bin/open-sEVbZ-kyyyJcjMY/verified-area/n7tk0nygk2up7j-7824vz2y/
hXXp://lsperennial[.]com/tnnfxu/545533028378/ofzt2ll4a-4754801-8569215-64d2t-rbtsi5ylgq/
hXXp://masspaths[.]org/transcyclist/open-array/69537295-LwrlRuR-portal/riy-u5984475/
hXXp://mistyvillage[.]com/inoxl28kgldf/open-sector/individual-forum/TC1AThq8D-H4iKcw9erMc8a7/
hXXp://monoclepetes[.]com/disneyworldclassroom/browse/
hXXp://mosaiclabel[.]com/4f9xnykaf/common-box/corporate-a30njr6-34dhllfehbjex6/14rm3hr6k358-x32zy5/
hXXp://myclarkcounty[.]com/wp-includes/open-resource/open-forum/o6a3exwvzfo-4wwxx8uts7/
hXXp://myfamilyresearch[.]org/dir/paclm/
hXXp://nisanurkayseri[.]com/fhiq04sgna7/a683w-an3x-4946/
hXXp://norikkon[.]com/administrator/16542-fBTLcdbEyJr-sector/VFCLsV-bAwgBBBeBqaJ-forum/fft2z7gdyzqee-8z80w6z68vs/
hXXp://nunes[.]ca/s59nlj/DOC/
hXXp://pascalterjanian[.]com/logs/multifunctional-2519534-Fs87CEgtQY82H6/verifiable-forum/2iFKNGyl-Ksmyn3gyI/
hXXp://plaestudio[.]com/wp-admin/multifunctional-zone/verified-space/zftkjoaw-xzuwtu1228/
hXXp://pmnmusic[.]com/backup-1540795171-wp-includes/Document/
hXXp://productorad10[.]cl/cdn-cgi/lm/6bwolkvw/
hXXp://radigio[.]com/qcloid/Pages/aveebb8ri/
hXXp://rememberingcelia[.]com/cgi-bin/private-box/additional-cloud/WoMAYyGYPic-ejGtLw5zKk9132/
hXXp://richardciccarone[.]com/watixl/Pages/iwq2bcuhtc/fpl5dh7-1085-7485017905-7upoox-mmwh5rr/
hXXp://rkpd[.]ulvitravel[.]com/cgi-bin/s0pgy-yg3-606/
hXXp://rozziebikes[.]com/tshirts/7XOEME6DSPI/l6bpob8m-8104-0278018-y6o222jln-fsxji7gy9l/
hXXp://safiryapi[.]net/mainto/private-zone/9977527-TGAtxV-space/noliIDq-ffuwzjN5H8zj/
hXXp://sakuralabs[.]com/4gubn/personal-zone/interior-forum/rye8idbdwx6uiw9-vtw0y35413/
hXXp://scottproink[.]com/wp-includes/LLC/3nm06yz1og/
hXXp://sigepromo[.]com/fonts/multifunctional-sector/security-kojbhnhsfxht47-4qgj/xznv8-35sz95t0t7/
hXXp://sofiarebecca[.]com/ybfm/multifunctional-XhmwQuIS-uBXA6FSMcoaXT2/7427993-1AJW4cmy-profile/P0jkvy-gwgs3qvm/
hXXp://southeasternamateurchampionships[.]com/0ng1en8p/common-57GaJ-JU2y57Cw9wWp/test-area/1CP3gWMySaac-iixIpxfJ216/
hXXp://southernlights[.]org/wp-includes/attachments/13iqe8n/
hXXp://stlaurentpro[.]com/25bd/Overview/qnrlmvj/
hXXp://stluketupelo[.]net/sermon/Document/
hXXp://technosolarenergy[.]com/wpk0/esp/xcggf7f/l41sd6-372903-111521309-pe7nqblm-rnbcyph7/
hXXp://thebeaversinstitute[.]org/m6zxne/open_sector/verifiable_grIwVfcE_JNkyS1ABG7O/JOr8Y2_c0N5pfizn8tqv/
hXXp://thecityglobal[.]com/creative/DOC/tmi48tldo/8fcpm52kxc-1823-224157721-0k5g3-2ntwz3u/
hXXp://theconsciouslivingguide[.]com/w63gh/NQOOE7ZE6E/
hXXp://theordeal[.]org/2hqr15/71028031_i0jDg_array/verified_profile/M17xNfJi_afcjbJ9y2/
hXXp://tinystudiocollective[.]com/tvtepc/parts_service/c5hlpnbm/04yte-92982998-989677-xuln504d-wj8wr99a0r/
hXXp://trinituscollective[.]com/wp-admin/DOC/3k2yxczqa-017872-15130767-6fcy299dtf-5p8y1zk/
hXXp://turbinetoyz[.]com/inc/available_sector/open_cloud/7gDaxLdZntQO_f54w1mdqt/
hXXp://vektra-grude[.]com/components/sites/xyj3oy2f/
hXXp://wolvesinstitute[.]org/wp-admin/INC/muosryq6917p/uozxo9-82202-738575-fbm4hisdv-0q5dy3ciz/
hXXp://www[.]africanswoo[.]com/wp-includes/IOG/
hXXp://www[.]bonfireholidays[.]in/efqog/Documentation/
hXXp://www[.]demarplus[.]com/19sn7/Overview/
hXXp://www[.]southwayhomes[.]co[.]uk/wp-admin/lm/5x8c1xywx2h/
hXXp://xhd[.]qhv[.]mybluehost[.]me/Maidentiffany/a4wnq/INC/be5oryde748n/877iw8k2-5677720-10188-kjqm-al3ax20hth/
hXXp://xn--3jsp48bswaq48h[.]com/binzbc/protected_disk/WsgEuoVh6_GLg1uIsNZxocly_tdagf_sb0hy87m9gi/jWdMxTd9_a73ophNx/
hXXp://yourdirectory[.]website/Mccracken/eTrac/rpiglgay-1418052884-1524951880-uuys-0fxj/
hXXps://bipinvideolab[.]com/wp-admin/51917864823222027/b0n0hcp4sl83/
hXXps://crossworldltd[.]com/wp-includes/48p5-o3ih-71/
hXXps://flexwebsolution[.]com/assets/multifunctional_disk/external_forum/7aa8z9os32iqygd_3gp4h/
hXXps://gurukool[.]tech/assets/t85vawx7s2xbi3q-1mvazihmr-module/interior-forum/gEwMX8-s0pLx8jJMLhGN/
hXXps://keshavalur[.]com/css/WRssOm/
hXXps://makmursuksesmandiri[.]com/wp-content/e3tpt3cph1wncut-ika4etq8sml6-sector/interior-htMCj-UR5CVYGd/bnb5oaopu0ptx-0wyytzw7u5/
hXXps://misterglobe[.]org/generall/Overview/i9y202-334800485-67760472-jj04w2e19-xppp1/
hXXps://mountainstory[.]pk/qoaij52hfs1d/common_FOQqDSi_Q50ORC3MzecY/guarded_9ode8j8xa3q9fa_3a14tqqj/x1e_418t92/
hXXps://murraysautoworks[.]com/contact/6VE37Q01O/50v2q5af8tv/y27daizl9-678276-439755027-2i7xojwpjd-ryyu/
hXXps://nhakhoachoban[.]vn/wp-includes/paclm/
hXXps://power-charger[.]co[.]uk/faq/Reporting/g30g4b8wvh/0w5c-2857976-135390-1dg1e-bjus2/
hXXps://risefoundations[.]in/rise/8448397_cee81q_jftx3_eseQqSx/corporate_pfmWWf_7uk8kfJTJvUrTR/OvdwZPUQy_ntycKI1ipM2/
hXXps://sharefoundation[.]in/wp-admin/multifunctional_module/test_cloud/oJuKHM3ik_Mee0ttbGc/
hXXps://summit2018[.]techsauce[.]co/startup/sYHAteT/
hXXps://timestampindia[.]com/citech/Document/
hXXps://twincitiesfrugalmom[.]com/wp-admin/eTrac/9porgmi/ul99a0-5568735694-75056-vt6wk395a-yymz6f/
hXXps://www[.]jadegardenmm[.]com/engl/docs/h85me2-45331562-6525577-0c62dwu3hl-mk47l/
hXXps://www[.]u4web[.]com/bnkddo/open_disk/guarded_kzfciuyy_v4gqdp/1dOq8z5_ILk0gJmw/