When phishing attacks occur, time to identify and remediate is measured in precious seconds. Reports of suspicious emails must be analyzed quickly and accurately. The entire attack surface must be discovered rapidly. Moreover, every email in the phishing campaign must be quarantined.
The stakes are high. Enterprises invest heavily in security solutions and secure email gateways (SEGs) to keep systems free of email-borne cyber threats. But how do you know if you’re getting a return on investment or reducing your overall risk?
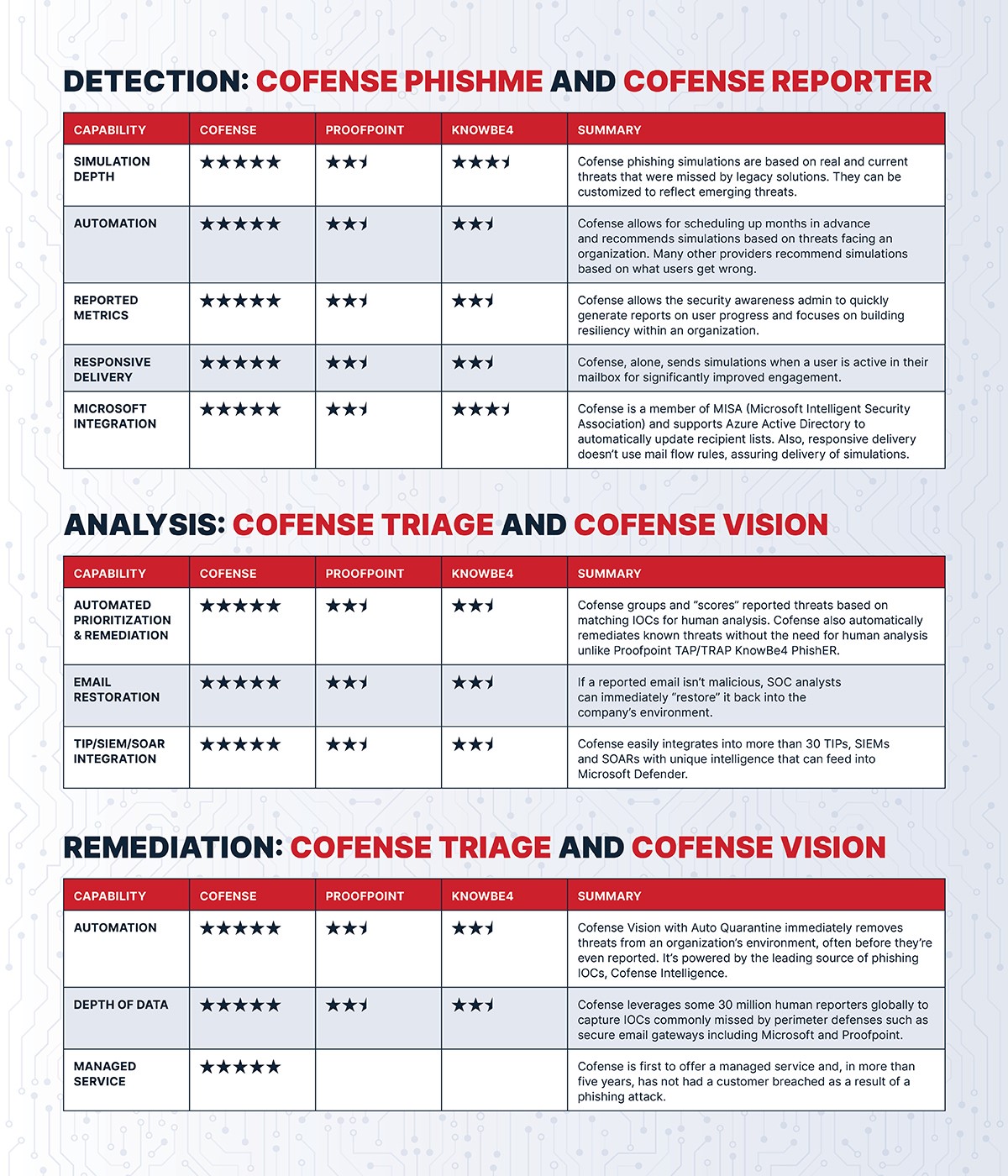
Why Choose Cofense Over Alternatives?
It’s a fact: SEGs can’t catch every phish. That’s particularly problematic when phishing has become the sweet spot for constantly innovating threat actors. Effective simulations and advanced technology must be based on the latest threats known to bypass SEGs. Your phishing countermeasures must also be comprehensive, boosted by crowdsourced intelligence. Take a look at just a few ways Cofense compares favorably to Proofpoint.
Threat hunting: Cofense affords unlimited custom categorization of threats with automatic tagging by thousands of unbiased intelligence-driven rules. Cofense also clusters attacks on payloads and offers Ask-an-Expert analysis via the Phishing Defense Center. Additional capability is provided through integration with Cofense Vision for Auto Quarantine, as well as with top SIEMs and SOARs. Proofpoint, by comparison, limits categorization to a few broad categories, and its other key capabilities are dated.
Phishing analysis: Cofense offers extensive search criteria (subject, sender, domain, SMTP header, etc.) and unlimited search scope. Proofpoint confines search criteria to little more than subject and sender. Its search scope is highly limited.
Quarantine and restore: Cofense provides search and quarantine from a single interface in minutes with the ability to automatically quarantine future attacks. Restore is transparent with no visible change to the restored item. Proofpoint search and quarantine is disconnected and time consuming. Restore is disruptive compared to Cofense.
Crowdsourced intelligence: Cofense provides a unique source of crowdsourced data identifying and reporting phish found behind all email security. Actionable intelligence is packaged into relevant IOCs that can instantly remediate known phish. Proofpoint gathers information from users. However, it isn’t email-phishing specific or instantly actionable.
But that’s not all.
Unlike Proofpoint, Cofense combines advanced automation with a global network of 32 million people reporting phish to stop phishing attacks fast. Cofense, alone in the industry, provides this level of phishing detection and response. That’s why more than half of the Fortune 500, and thousands of other organizations, trust us.
Take a closer look at Cofense vs. the competition.
Bottomline: We’re Cofense. We Stop Phish.
Many businesses try to build email security solutions with slow-to-deploy and ineffective SEGs and other systems from multiple vendors. These combinations are expensive, built on last-generation technology and don’t deliver the capabilities required to reliably and consistently stop phishing attacks. As enterprises worldwide have seen, Cofense’s cloud-native Phishing Detection and Response platform reduces vendors, risk, and costs by $100,000 or more. Learn how Cofense can help you with choosing an email security solution that does everything your enterprise requires.
We encourage close scrutiny against alternatives. Call us. Challenge us to convince you that we deliver above and beyond the competition.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.








