By Aaron Riley
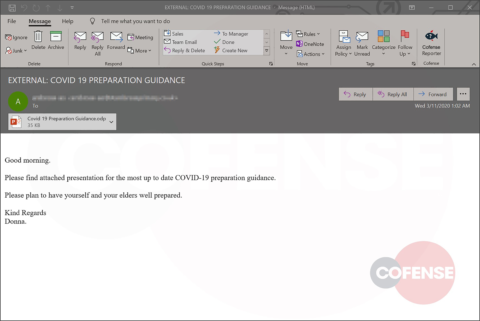
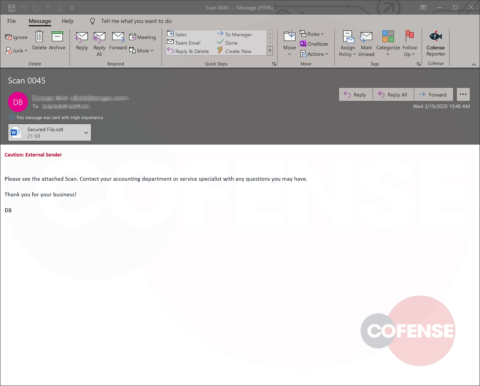
Cofense Intelligence has seen a stark increase in phishing email campaigns relating to the COVID-19 pandemic that spoof trusted health services to deliver credential phishing or malware. Credential phishing makes up the majority of the campaigns analyzed, with the minority ranging from simple to complex delivery chain and malware samples. With some companies quickly adopting work-from-home (WFH) policies, threat actors are poised to take advantage of the newly created security gaps by playing on pandemic fears. The potential impact of these phishing campaigns, along with the current economic uncertainty, can be devastating to an organization.
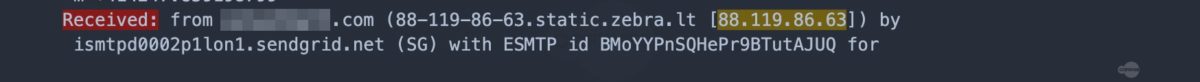
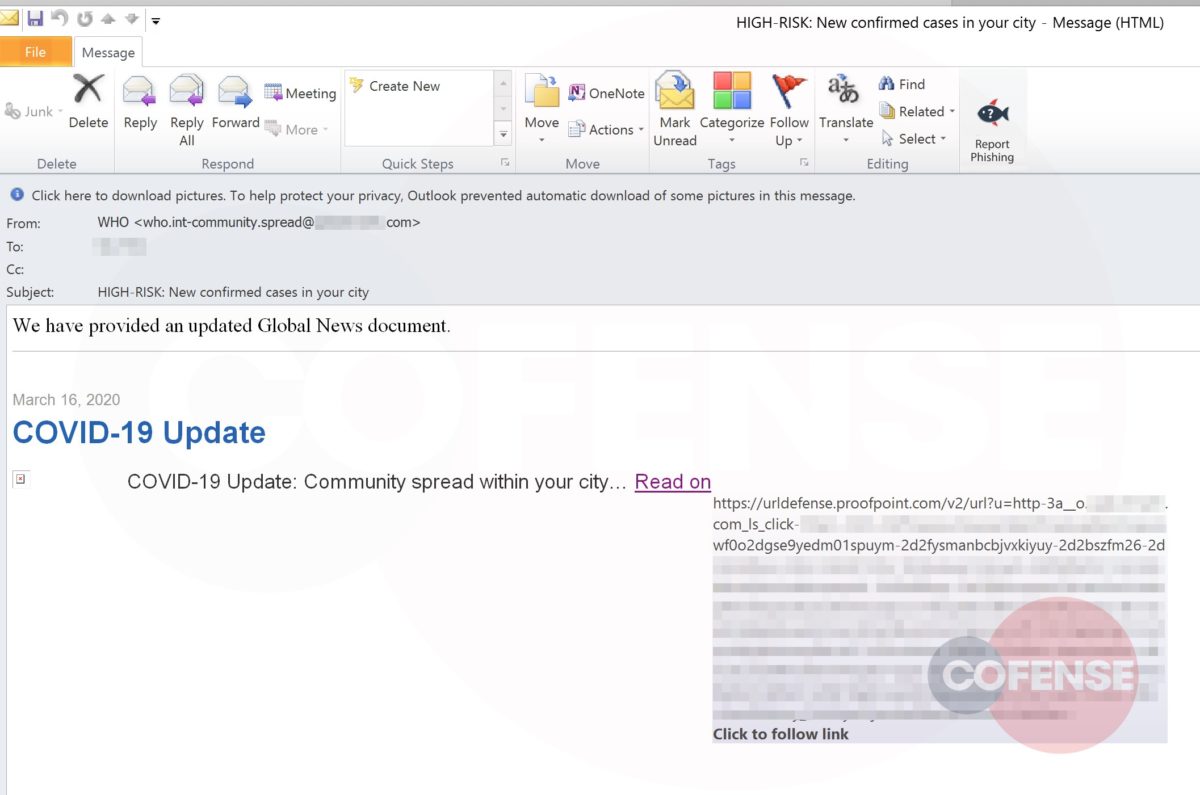
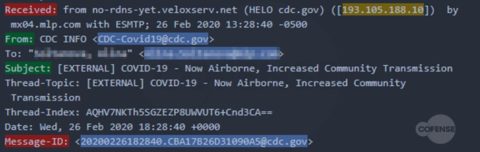
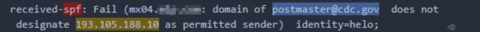
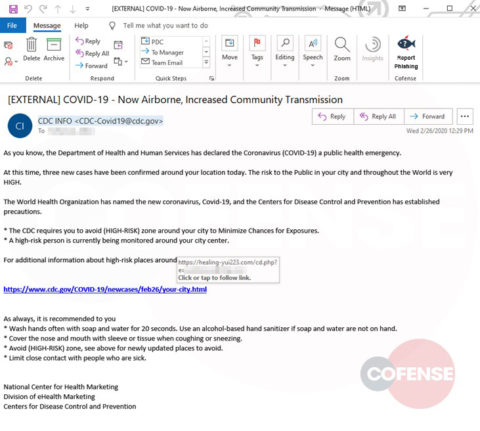
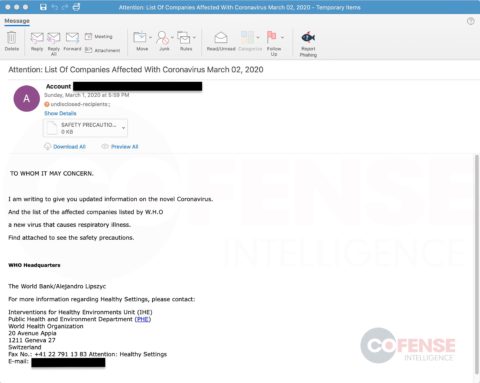
As soon as threat actors began weaponizing this crisis in phishing emails, Cofense Intelligence published a Flash Alert reporting that the Centers for Disease Control and Prevention (CDC) and World Health Organization (WHO) were spoofed in a Coronavirus-themed phishing campaign to deliver the Agent Tesla keylogger. Since that alert, we have seen an increase in phishing campaigns that spoof organizations in aviation and other transportation industries.
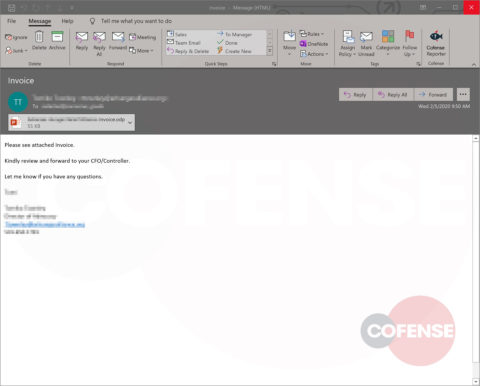
Coronavirus-themed campaigns that deliver malware are starting to evolve in complexity as well. For example, the Agent Tesla keylogger campaign mentioned above was delivered via an email attachment, which would have been blocked by sandbox analysis. In comparison, the most recent campaign used a Microsoft Office Word document with the CVE-2017-11882 exploit, which delivered an AutoIT dropper that placed five different malware family samples onto the endpoint: Remcos RAT, Black RAT, Ave_Maria Stealer, Lime RAT, and Sality Bot. All five of these payloads are designed to steal information and provide persistent control to a threat operator, and only one needs to be successful in its attempts to compromise the machine.
Most organizations are not set up to have all employees work from home. As these organizations attempt to quickly develop their WFH business requirements, they might overlook security. An organization’s most reliable and hardened security features are typically within its physical facility and do not extend much beyond that domain. These security features include, but are not limited to, Network Access Control (NAC), content filtering, Data Loss Prevention (DLP), eavesdropping / Machine In The Middle (MITM) prevention, and update/patch management. With some of these security features effectively “bypassed” for the attacker in a WFH situation, organizations face an increased risk that a phishing campaign will impact them. A malicious incident or event could go unnoticed by overburdened IT administration and security teams for longer than normal periods.
Most of the newly created risk can be mitigated. Network Access Control can be done with a software agent on each endpoint attempting to connect to the organization. The agent communicates to an authoritative entity to prove the machine has the organization’s trusted certificate to connect to the internal network, is up to date with antivirus definitions, and is fully patched to the organization’s requirements. Mandatory network tunneling for the endpoint can mitigate the lack of content filtering, network DLP, and MITM security measures. A Virtual Private Network (VPN) connection to the enterprise network, which forces the network traffic through its egress and ingress points, will help cover the risk created by WFH employees—as long as employees do not reintroduce the vulnerability by turning off the VPN. These measures are effective but require resources and time to implement, which some organizations might find challenging while rapidly rolling out WFH.
Organizations need to educate their employees about the risk of Coronavirus-themed phishing attacks and, at the same time, ensure that employees do not dismiss legitimate information. Creating phishing simulation templates around the Coronavirus theme is not advised. Doing so could cause undue panic or add unnecessary noise. Instead, organizations should describe what to look for in Coronavirus phishing attempts and then explain how legitimate information will be communicated.
Cofense Intelligence anticipates the volume of Coronavirus-themed phishing campaigns will continue to increase in the near future and will target specific industry sectors such as healthcare, energy, and public services. These campaigns will make increased use of malware and will spoof a larger number of legitimate businesses. Security teams will need to act quickly to determine new WFH risks and the proper mitigations. Clear, concise communication and education, coupled with secure technology and the right implementation strategies, is the best way to secure the target base of these phishing attacks.
How Cofense Can Help
Visit Cofense’s Coronavirus Phishing Infocenter to stay up to date as threats evolves. Our site is updated with screenshots and YARA rules as we continue to track campaigns.
For Cofense Intelligence customers who would like to keep up with the Active Threat Reports and indicators being published, all COVID-19 campaigns are tagged with the “Pandemic” search tag.
Cofense Intelligence customers can also search up to date reports in ThreatHQ using the “Search Tags” field in the Search Form.
Indicators of Compromise
To view the full list of IOCs, click on the menu below to expand further.
| 36802, 36908, 36937, 36938, 36939, 36940, 36941, 36942, 36943, 36957, 37146, 37148, 37149, 37151, 37152, 37226, 37227, 37228, 37230 |
PM_Intel_Nemty_37230
PM_Intel_AgentTesla_37227
PM_Intel_AgentTesla_37226
PM_Intel_TrickBot_37151
PM_Intel_AgentTesla_37152
PM_Intel_Loki_37149
PM_Intel_Hawkeye_37148
PM_Intel_Hawkeye_37146
PM_Intel_AgentTesla_36802
PM_Intel_CredPhish_36943
PM_Intel_CredPhish_36942
PM_Intel_CredPhish_36940
PM_Intel_CredPhish_36939
PM_Intel_CredPhish_36938
PM_Intel_CredPhish_36937
PM_Intel_CredPhish_36941
PM_Intel_BlackRAT_36957
PM_Intel_Loki_36908
hxxp://euromopy[.]tech/etty/black/download/fre[.]php
hxxps://drive[.]google[.]com/uc?export=download&id=1V8530tZ-SNHELlaVL4BMQpJrRU2DBPSL
hxxps://gocycle[.]com[.]au/cdcgov/files/
hxxps://urbanandruraldesign[.]com[.]au/cdcgov/files/
hxxps://healing-yui223[.]com/cd[.]php
hxxps://onthefx[.]com/cd[.]php
hxxps://www[.]schooluniformtrading[.]com[.]au/cdcgov/files/
hxxp://my[.]pcloud[.]com/publink/show?code=XZO5BWkZjc6l5EBCtnkTYqw2DHqzEBT4LAay
hxxps://takemorilaw[.]com/wp-content/micro-update-1-2/
hxxp://www[.]dogogiaphat[.]com/ecdc[.]php
hxxps://www[.]scholarcave[.]com/owa/owa[.]php
hxxps://jetluxinc396[.]sharepoint[.]com/:b:/g/ERt-r1ZM6PRGhKdxb6bfZSIBcOX2b0y8snN4fg8f7z22rA
hxxps://southhillspros[.]com/citrix/Ward/broward[.]php
hxxps://southhillspros[.]com/Rovince/Jelink[.]html
hxxps://southhillspros[.]com/citrix/Ward/broward[.]htm
hxxps://wusameetings[.]tk/boding/Jelink[.]html
hxxps://noithatgoocchoav[.]com/cd[.]php
hxxps://www[.]brightparcel[.]com/corona/owa[.]php
hxxps://toyswithpizzazz[.]com[.]au/service/coronavirus/
hxxps://notmsg[.]smvm[.]xyz/
hxxp://sevgikresi[.]net/logof[.]gif
hxxp://datalinksol[.]com/logo[.]gif
hxxp://autocarsalonmobil[.]com/wp-content/uploads/Internetsonline[.]txt
hxxp://nlcfoundation[.]org/images/xs[.]jpg
hxxps://pastebin[.]com/raw/vnPLhhBH
hxxp://snsoft[.]host-ed[.]me/images/logos[.]gif
hxxp://edirneli[.]net/tr/logo[.]gif
hxxp://185[.]244[.]30[.]4:6669
hxxp://68[.]168[.]222[.]206/logos[.]gif
hxxp://babystophouse[.]com/images/logo[.]gif
hxxp://glamfromeast[.]com/image/logo[.]gif
hxxp://bit[.]ly/2TpOpNS
hxxp://natufarma[.]net/imagens/logof[.]gif
hxxp://mabdesign[.]unlugar[.]com/button[.]gif
hxxp://gardapalace[.]it/logo[.]gif
hxxp://hidroservbistrita[.]ro/images/logo[.]gif
hxxp://krupoonsak[.]com/logo[.]gif
hxxp://emrahkucukkapdan[.]com/img/button[.]gif
hxxp://onlinepreneur[.]id/license/love[.]exe
hxxp://onlinepreneur[.]id/manager/brain[.]exe
hxxps://site-inspection[.]com/[.]well-known/acme-challenge/w[.]php/9SG2m697HN
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=6350FGwOB6MQS5d7ZcXy
hxxps://114[.]8[.]133[.]71:449/red5/
hxxps://181[.]129[.]104[.]139:449/red5/
hxxps://51[.]89[.]73[.]158:443/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=lcasCwk4Qjbk8sBCAE8g
hxxps://194[.]5[.]250[.]150:443/red5/
hxxps://186[.]71[.]150[.]23:449/red5/
hxxps://107[.]172[.]191[.]12:443/lib698/
hxxps://46[.]17[.]107[.]65:443/lib698/
hxxps://64[.]44[.]51[.]113:447/red5/
hxxps://181[.]112[.]157[.]42:449/red5/
hxxps://212[.]80[.]217[.]220:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=WjL3jrVFwBBnlQp3xn8K
hxxps://185[.]14[.]31[.]252:443/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=PzKFqjTUgsVxfN2OL347
hxxps://46[.]4[.]167[.]250:447/lib698/
hxxps://172[.]245[.]156[.]138:443/lib698/
hxxps://180[.]180[.]216[.]177:449/lib698/
hxxps://203[.]176[.]135[.]102:8082/red5/
hxxps://146[.]185[.]253[.]122:447/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=hNRuyY0glKhPxpDGkhRh
hxxps://146[.]185[.]253[.]178:443/lib698/
hxxps://181[.]140[.]173[.]186:449/red5/
hxxps://36[.]89[.]85[.]103:449/red5/
hxxps://51[.]254[.]164[.]244:443/red5/
hxxps://194[.]5[.]250[.]150:443/lib698/
hxxps://185[.]244[.]39[.]65:447/red5/
hxxps://172[.]245[.]157[.]135:443/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=Yagk0Foy3wjdzOq6nQcP
hxxps://5[.]2[.]79[.]66:443/lib698/
hxxps://193[.]37[.]213[.]128:443/red5/
hxxps://185[.]99[.]2[.]221:443/lib698/
hxxps://146[.]185[.]253[.]179:447/red5/
hxxps://96[.]9[.]73[.]73:80/lib698/
hxxps://121[.]100[.]19[.]18:449/red5/
hxxps://185[.]99[.]2[.]140:447/lib698/
hxxps://195[.]123[.]239[.]67:443/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=bpj5AXSdClkWLG84Xv02
hxxps://185[.]62[.]188[.]159:443/lib698/
hxxps://181[.]140[.]173[.]186:449/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=xhyi95QEt2sH7ZGSl5FV
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=rOE8Tr0FuFXfSSUaDO6M
hxxps://146[.]185[.]253[.]122:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=rtvUCSO49CMSm2QTlDcH
hxxps://85[.]204[.]116[.]253:443/lib698/
hxxps://46[.]174[.]235[.]36:449/lib698/
hxxps://119[.]252[.]165[.]75:449/red5/
hxxps://146[.]185[.]253[.]176:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=YJZHjkZ5qSUBheGScz5O
hxxps://178[.]156[.]202[.]157:447/red5/
hxxps://194[.]5[.]250[.]69:443/lib698/
hxxps://146[.]185[.]253[.]178:443/red5/
hxxps://36[.]89[.]85[.]103:449/lib698/
hxxps://185[.]203[.]118[.]37:443/red5/
hxxps://119[.]252[.]165[.]75:449/lib698/
hxxps://4cao4pyxbarkxf4n[.]onion:448/red5/
hxxps://185[.]142[.]99[.]89:443/red5/
hxxps://180[.]180[.]216[.]177:449/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=GmZr9Sd6TdL9g237BJFd
hxxps://195[.]123[.]239[.]29:447/red5/
hxxps://104[.]168[.]96[.]122:447/red5/
hxxps://46[.]4[.]167[.]250:447/red5/
hxxps://46[.]174[.]235[.]36:449/red5/
hxxps://185[.]14[.]31[.]98:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=MXtg3z4uEXlCKNSMW10E
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1547738007155673&id=pTCpS2vUujsK8z3zXJ0L
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=nZLf5Zn5ckDvobxOozo2
hxxps://5[.]255[.]96[.]187:447/red5/
hxxps://190[.]119[.]180[.]226:8082/red5/
hxxps://185[.]99[.]2[.]221:443/red5/
hxxps://5[.]182[.]210[.]226:443/red5/
hxxps://192[.]210[.]226[.]106:443/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=1eufomiZKmEvZe8AXaZK
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=SgRoybJA35wuTbDNCEs7
hxxps://5[.]2[.]76[.]29:447/red5/
hxxps://96[.]9[.]77[.]142:80/red5/
hxxps://194[.]5[.]250[.]69:443/red5/
hxxps://85[.]143[.]221[.]183:447/lib698/
hxxps://96[.]9[.]73[.]73:80/red5/
hxxps://195[.]123[.]239[.]67:443/red5/
hxxps://202[.]29[.]215[.]114:449/red5/
hxxps://45[.]135[.]164[.]193:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=HJb3L1X7FaO9MFRM2xJW
hxxps://146[.]185[.]253[.]18:447/lib698/
hxxps://45[.]135[.]164[.]193:447/red5/
hxxps://103[.]94[.]122[.]254:8082/red5/
hxxps://186[.]232[.]91[.]240:449/lib698/
hxxps://96[.]9[.]77[.]142:80/lib698/
hxxps://64[.]44[.]51[.]124:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=UqKF7TJ4pK6nu55Nq5SR
hxxps://51[.]254[.]164[.]244:443/lib698/
hxxps://51[.]89[.]73[.]158:443/red5/
hxxps://23[.]94[.]185[.]27:446/response/rcrd[.]php?s=1584097681876834
hxxps://46[.]17[.]107[.]65:443/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=YNsg198eIe2CENiLH2Q6
hxxps://103[.]94[.]122[.]254:8082/lib698/
hxxps://85[.]204[.]116[.]253:443/red5/
hxxps://185[.]62[.]188[.]159:443/red5/
hxxps://217[.]12[.]209[.]200:443/red5/
hxxps://192[.]210[.]226[.]106:443/red5/
hxxps://146[.]185[.]219[.]63:443/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=uOggu83wFMsZgJy2gYXR
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=KTjaFGA6rzAIRhzYpxsn
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=7aybmyzTyxjVkmAgca3q
hxxps://181[.]129[.]134[.]18:449/lib698/
hxxps://103[.]84[.]238[.]3:80/red5/
hxxps://36[.]89[.]106[.]69:80/red5/
hxxps://64[.]44[.]51[.]113:447/lib698/
hxxps://5[.]255[.]96[.]187:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=f2hUQzGxBwEot8ExHJ1m
hxxps://185[.]20[.]185[.]76:443/red5/
hxxps://198[.]23[.]252[.]127:447/lib698/
hxxps://185[.]216[.]35[.]10/3/L2KSUN[.]php
hxxps://146[.]185[.]253[.]18:447/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=Vs9fOJw0UArIH5NRL2Fi
hxxps://172[.]245[.]156[.]138:443/red5/
hxxps://114[.]8[.]133[.]71:449/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=LcVEiKUW9394wikl1RmW
hxxps://170[.]238[.]117[.]187:8082/lib698/
hxxps://185[.]14[.]31[.]97:443/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=YCZPUzOj6gGO3b0oxZXp
hxxps://193[.]111[.]62[.]50:447/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=eVMWyxkROwNbwzrByPGK
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=qVO7FmnWdv3CqlwU53XE
hxxps://5[.]182[.]210[.]226:443/lib698/
hxxps://195[.]123[.]239[.]29:447/lib698/
hxxps://202[.]29[.]215[.]114:449/lib698/
hxxps://181[.]196[.]207[.]202:449/red5/
hxxps://188[.]120[.]242[.]75:447/lib698/
hxxps://85[.]143[.]221[.]183:447/red5/
hxxps://121[.]100[.]19[.]18:449/lib698/
hxxps://186[.]232[.]91[.]240:449/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=gKmNNEREiPRIKGQp2dmg
hxxps://170[.]238[.]117[.]187:8082/red5/
hxxps://46[.]4[.]167[.]242:447/red5/
hxxps://62[.]109[.]11[.]248:447/lib698/
hxxps://190[.]214[.]13[.]2:449/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=tN8O8VDbWyHtPRydtWy0
hxxps://198[.]15[.]82[.]162:443/red5/
hxxps://170[.]84[.]78[.]224:449/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=NlWlLA26RToHt8mTsgOI
hxxps://198[.]23[.]252[.]127:447/red5/
hxxps://185[.]99[.]2[.]140:447/red5/
hxxps://200[.]21[.]51[.]38:449/lib698/
hxxps://104[.]168[.]96[.]122:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=eMimeUZPy76ZHmG1apBW
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=nN2EWQAMeD3cg32aDQtJ
hxxps://188[.]209[.]52[.]162:443/red5/
hxxps://181[.]112[.]157[.]42:449/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=j3x1pd2ADExKICKojgcV
hxxps://186[.]71[.]150[.]23:449/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=IqS9Lp3Qs0uILRwyvocO
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=8ldKgFEC3ev2pLmqqKYu
hxxps://31[.]131[.]21[.]168:447/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=qAfHjNJAMHs8TCAv8VAY
hxxp://142[.]93[.]22[.]0:80/
hxxps://200[.]21[.]51[.]38:449/red5/
hxxps://5[.]255[.]96[.]186:447/red5/
hxxps://200[.]127[.]121[.]99:449/red5/
hxxps://5[.]2[.]79[.]66:443/red5/
hxxps://185[.]99[.]2[.]137:443/lib698/
hxxps://51[.]254[.]164[.]245:443/red5/
hxxps://185[.]99[.]2[.]137:443/red5/
hxxps://64[.]44[.]51[.]124:447/red5/
hxxps://177[.]74[.]232[.]124:80/red5/
hxxps://200[.]127[.]121[.]99:449/lib698/
hxxps://171[.]100[.]142[.]238:449/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=juhyLxqVBnei6qmSsjZ7
hxxps://178[.]156[.]202[.]157:447/lib698/
hxxps://172[.]245[.]157[.]135:443/lib698/
hxxps://185[.]99[.]2[.]115:443/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=HMucklYySnPDh9NWPo2h
hxxps://217[.]12[.]209[.]200:443/lib698/
hxxps://185[.]244[.]39[.]65:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=gjBKrgh9ZivFEv6OnkVg
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=QKf1HHY4dLUK3t2czTR3
hxxps://31[.]131[.]21[.]168:447/lib698/
hxxps://103[.]84[.]238[.]3:80/lib698/
hxxps://177[.]74[.]232[.]124:80/lib698/
hxxps://203[.]176[.]135[.]102:8082/lib698/
hxxps://181[.]129[.]104[.]139:449/lib698/
hxxps://131[.]161[.]253[.]190:449/lib698/
hxxps://188[.]120[.]242[.]75:447/red5/
hxxps://181[.]196[.]207[.]202:449/lib698/
hxxps://62[.]109[.]11[.]248:447/red5/
hxxps://36[.]89[.]106[.]69:80/lib698/
hxxps://198[.]15[.]82[.]162:443/lib698/
hxxps://181[.]113[.]28[.]146:449/lib698/
hxxps://185[.]14[.]31[.]98:447/red5/
hxxps://185[.]142[.]99[.]89:443/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=93vdwyq6sh9oBUrUmnzS
hxxps://107[.]172[.]191[.]12:443/red5/
hxxps://185[.]203[.]118[.]37:443/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=IJgYwiMilRq9dmvYXx5O
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=oViUuJw2ydNIx3h3QEYd
hxxps://46[.]4[.]167[.]242:447/lib698/
hxxps://5[.]2[.]76[.]29:447/lib698/
hxxps://146[.]185[.]219[.]63:443/lib698/
hxxps://190[.]100[.]16[.]210:8082/lib698/
hxxps://23[.]94[.]185[.]27:446/response/rcrd[.]php?s=1547738007155673
hxxps://4cao4pyxbarkxf4n[.]onion:448/lib698/
hxxps://112[.]78[.]164[.]34:8082/lib698/
hxxps://185[.]99[.]2[.]115:443/lib698/
hxxps://45[.]148[.]120[.]153:443/lib698/
hxxps://193[.]37[.]213[.]128:443/lib698/
hxxps://45[.]148[.]120[.]153:443/red5/
hxxps://190[.]214[.]13[.]2:449/lib698/
hxxps://185[.]20[.]185[.]76:443/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=d4wYKmoNAL4jbXsWnwNP
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=uCQHZmGWTLLlfhfR94Wj
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=kpmcigmW4tIXJAliL5SP
hxxps://5[.]255[.]96[.]186:447/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=9kgyvNnUnLXBHKxfhR76
hxxps://131[.]161[.]253[.]190:449/red5/
hxxps://185[.]14[.]31[.]97:443/lib698/
hxxps://188[.]209[.]52[.]162:443/lib698/
hxxps://185[.]14[.]31[.]252:443/lib698/
hxxps://212[.]80[.]217[.]220:447/red5/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=hhHR67XuY9k7vxRMdwoh
hxxps://193[.]111[.]62[.]50:447/lib698/
hxxps://170[.]84[.]78[.]224:449/lib698/
hxxps://112[.]78[.]164[.]34:8082/red5/
hxxps://181[.]129[.]134[.]18:449/red5/
hxxps://146[.]185[.]253[.]179:447/lib698/
hxxps://190[.]100[.]16[.]210:8082/red5/
hxxps://146[.]185[.]253[.]176:447/red5/
hxxps://190[.]119[.]180[.]226:8082/lib698/
hxxps://171[.]100[.]142[.]238:449/lib698/
hxxps://181[.]113[.]28[.]146:449/red5/
hxxps://51[.]254[.]164[.]245:443/lib698/
hxxps://23[.]94[.]185[.]27:446/response[.]php?s=1584097681876834&id=O6D4aGfNwIxDT5OfEo9d
hxxp://uzoclouds[.]eu/dutchz/dutchz[.]exe
hxxp://bibpap[.]com/1g7/pin[.]php
hxxp://posqit[.]net/TT/50590113[.]exe
hxxp://bitly[.]ws/83FN
hxxp://nemty[.]top/public/pay[.]php
hxxp://nemty10[.]biz/public/gate[.]php
hxxps://marsdefenseandscience[.]com/reports[.]zip
hxxp://zjoxyw5mkacojk5ptn2iprkivg5clow72mjkyk5ttubzxprjjnwapkad[.]onion/public/pay[.]php
euromopy[.]tech
wusameetings[.]tk
emrahkucukkapdan[.]com
gardapalace[.]it
snsoft[.]host-ed[.]me
cornerload[.]dynu[.]net
seasonsnonaco[.]ddnsking[.]com
datalinksol[.]com
nlcfoundation[.]org
sevgikresi[.]net
autocarsalonmobil[.]com
seasons444[.]ddns[.]net
krupoonsak[.]com
natufarma[.]net
edirneli[.]net
mabdesign[.]unlugar[.]com
babystophouse[.]com
glamfromeast[.]com
hidroservbistrita[.]ro
onlinepreneur[.]id
onlinepreneur[.]id
site-inspection[.]com
uzoclouds[.]eu
bibpap[.]com
posqit[.]net
zjoxyw5mkacojk5ptn2iprkivg5clow72mjkyk5ttubzxprjjnwapkad[.]onion
nemty10[.]biz
marsdefenseandscience[.]com
nemty[.]top
45[.]64[.]97[.]178
185[.]216[.]35[.]10
ef07feae7c00a550f97ed4824862c459
05adf4a08f16776ee0b1c271713a7880
29e8800ebaa43e3c9a8b9c8a2fcf0689
970bc68378526981f7b470b014e4a61d
648a2da84b857520830981af55bbd4f2
e36b292de6db73e78f77ea2fed092848
dca53f253066ff1736d9735e0e4f861b
ecdcf6e29f917239ecd9f3c4cd4bd4b4
4ad1b0398bc3a371a82923383de2d0a4
54fb481530500d781d0aa282e8524016
0c6fa100c0fd612d9f55a87017989621
457d4329b66efcbd6bcba521502df6a8
6053a2d672f9f9bd5cd0725d4b106493
c1ab6a9a559d54c071eb110235f77fe2
be950f0aaa6654c30532168a3f82d4e6
33498c2e5ce532fdbcabfc2caa882e04
ca0951249ef447ca0443ebf519b7ec7e
24cabc6a0a02674fc6a1e778cd265ecc
d6557715b015a2ff634e4ffd5d53ffba
2858a05f4ec255cb383db26019720959
4e9aa334811b6a4fa6542483a34fc9c5
caf133755a01fea99b323e3fa1965705
c6f8278ee29471ce84b4f6bb148161de
1f7ff50f672288616ef80220ab41cddc
ef991e614208324eecb10831f0b6990d
93109ef58dc7fa86e2cb186e8d8cfc8a
8f9c95b359a574f16801184b095a027d
ba0b4e05e3b26e26f2e0793b9190ba2c
f4d2bdeeb7c5c3eac0afe845b988b31a
a39694b7311fc2d0991d6f7aa4d22460
d9822e032bb6f0d39aba533ba5b50dca
ba6a13ad9f673e365580b389a7297611
64574f1a3b4d554322279a238c7943f1
8aa849595f1065dce6488dcff4caa043
34b9244ead7f1d1d4a94e04a05d8f474
222d2f0dcae9889174e500fea7655b9a
811e21aadc64bbbedaa2d616bd258f58
4ed0cbc8dc2c3208bf760976d854b276
1cd9c1348db93cd674066f566740d697
3a7d8ab97cc7cacdc6b613632f79ae36
777250fb412071ab4b655883de6b888b
fa1ed07a84d0f6db0560edffc0f5cd0c
cc24481d8673278c9ca9a427aebfaf30
a98c28d9666e6050b2c76d0062342078
62ded00158221fd7b3e678b9d9edbd7b
ecf4c248beb954f59901bba955646c19
64574f1a3b4d554322279a238c7943f1
62025fefd240ac80326db825903da90e
2f1ac455d1c6e2a3f3e0d1137b047696
a5a2a55b29d20a684b09e40d4480029d
022e42a2ad49f8428f34435b595c7216
08dd5ee67ee69ddfa11cb55562baef58
e7351df51633435293ddc09de7fdc57c
1179a7989031fc4b6331505b388dcb12
378bbb172ccae5e28549a003e4e84bce
07d718b0b7f2bbe0ea001c76aca82b7d
f221f92d7f8ccb7133f58ae1a3f4257c
501318d315ba07554f92ff13ebb075c2
b57d2c252746baff47e12b4021a75ba4