By Dylan Main, Cofense Phishing Defense Center
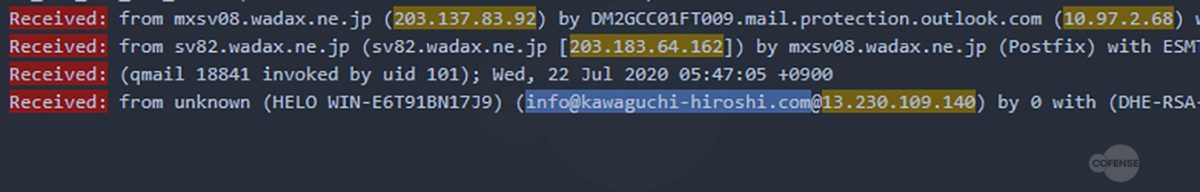
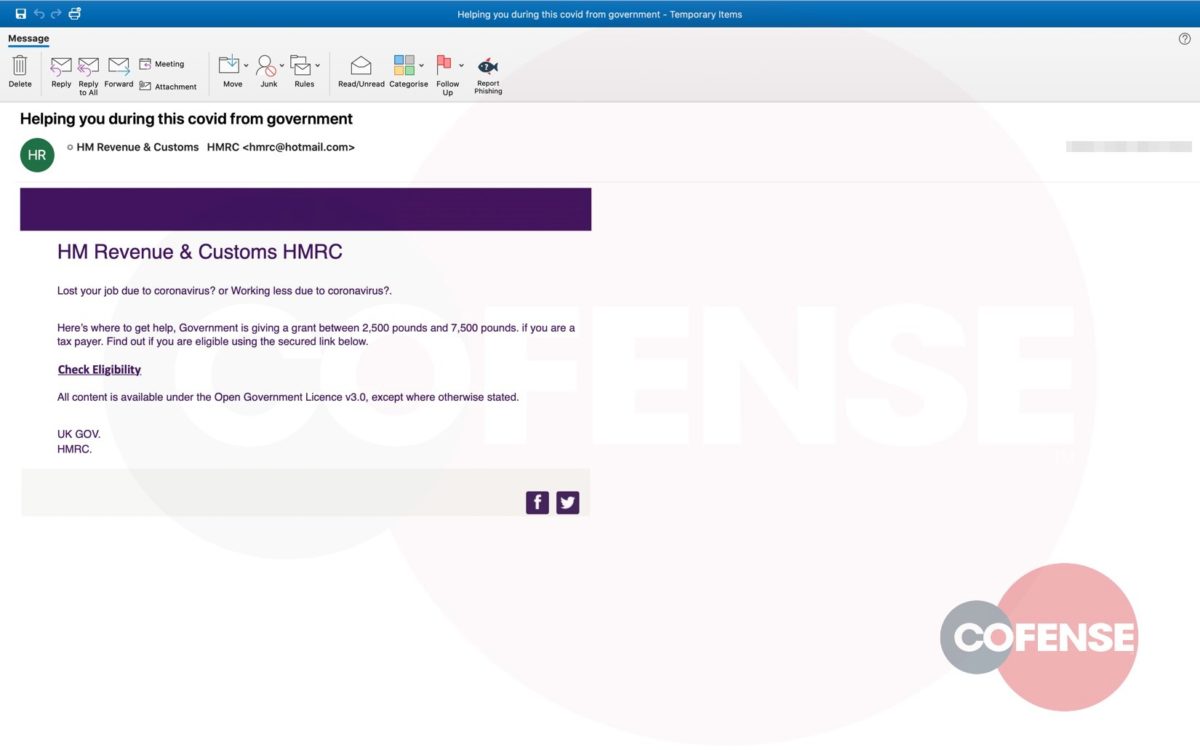
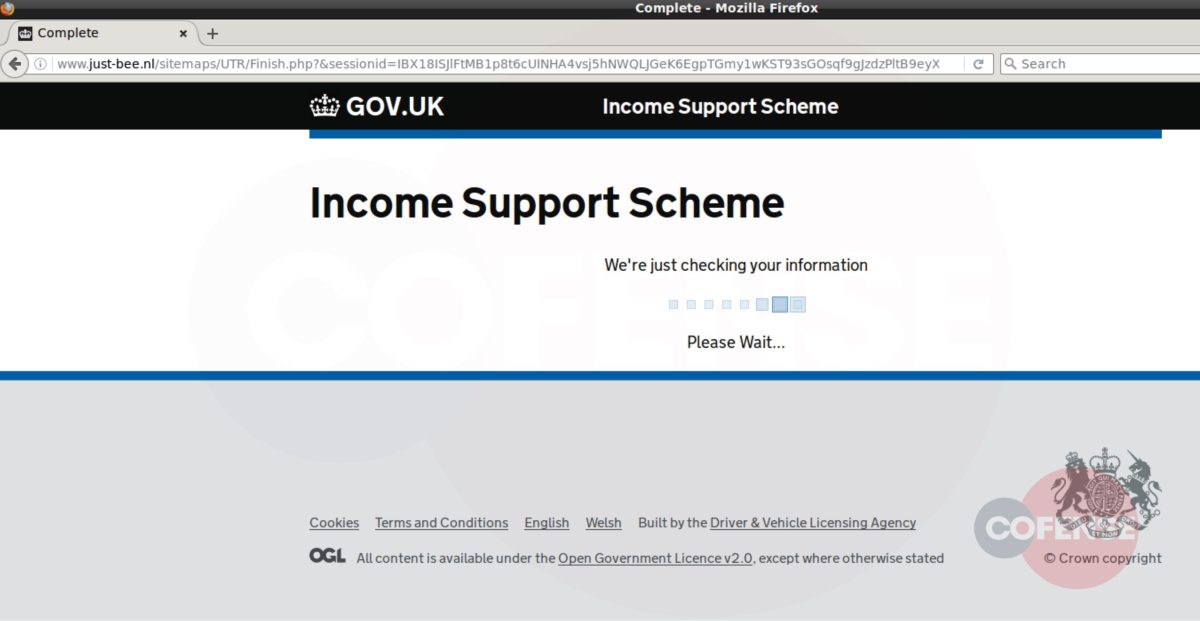
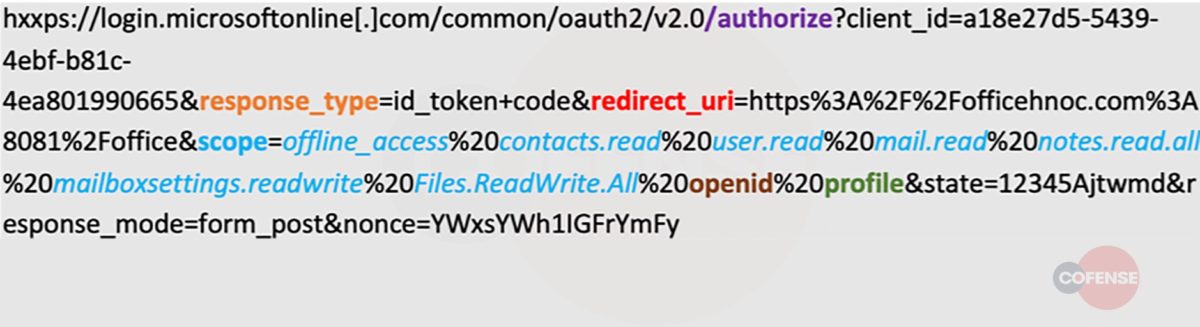
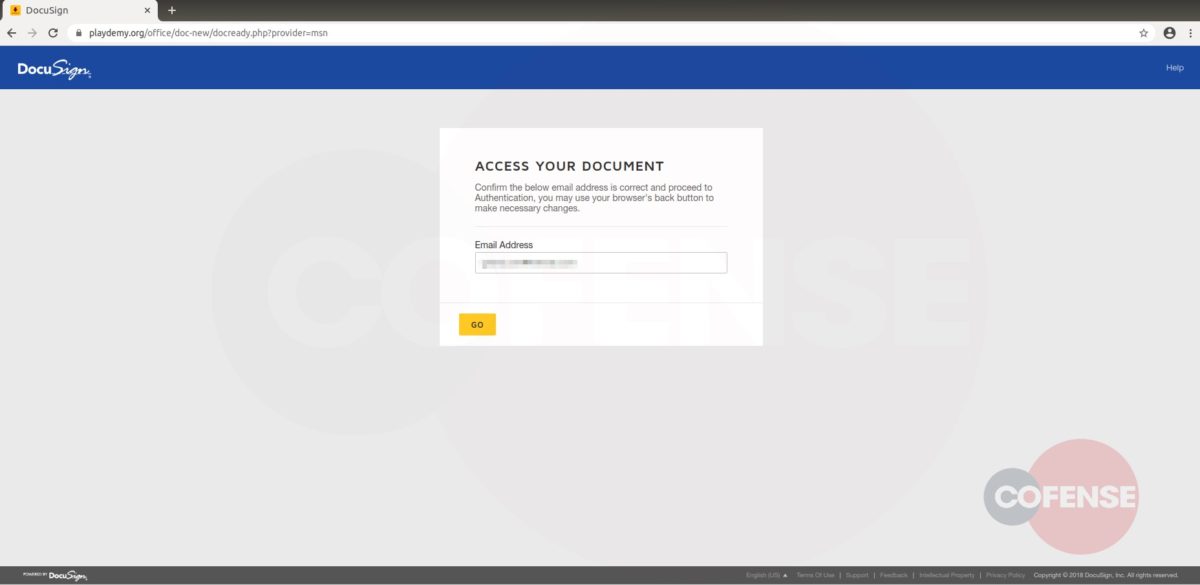
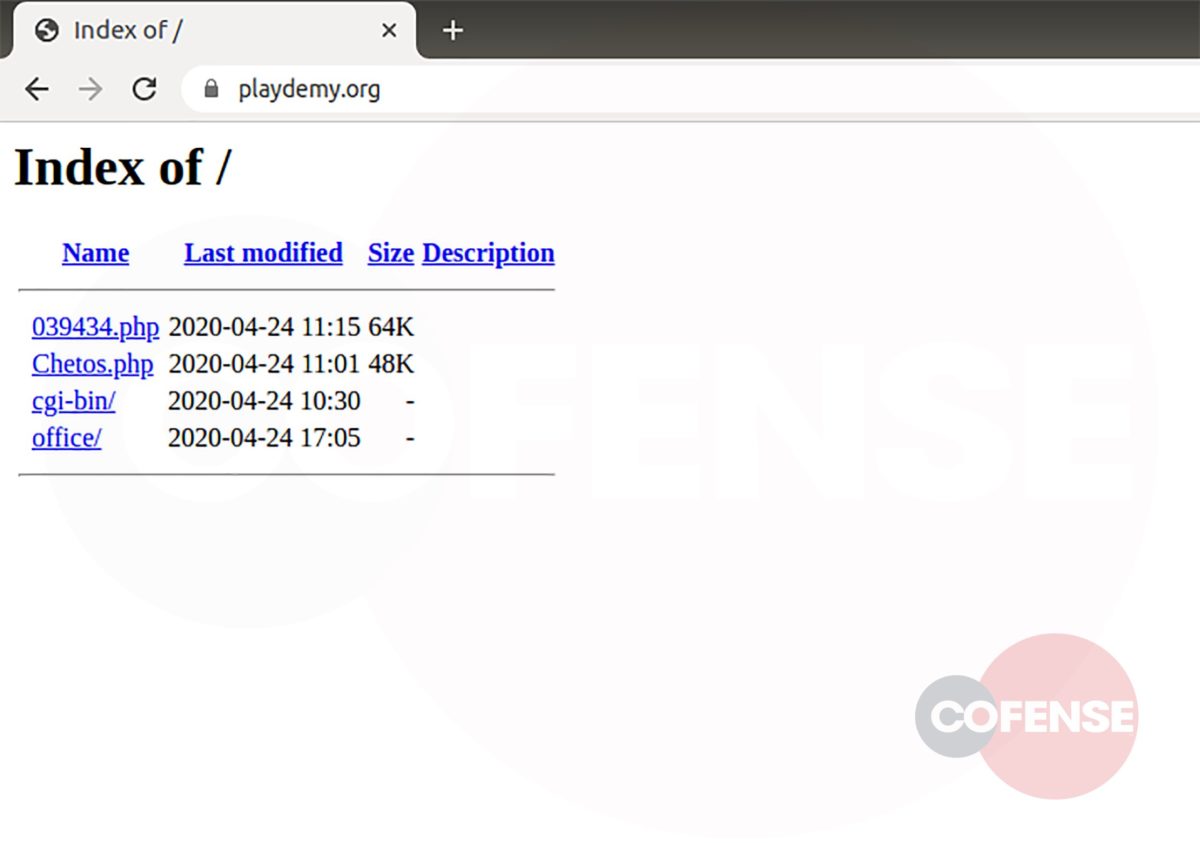
Message quarantine phish are back, this time with a new tactic utilizing the targeted company’s homepage as part of the attack. The Cofense Phishing Defense Center (PDC) has identified this campaign which attempts to steal employee credentials by posing as a message quarantine email. Using an overlay tactic to disguise itself, this attack is an example of how threat actors are using more advanced techniques to make these malicious emails appear as though they are from a trusted source.
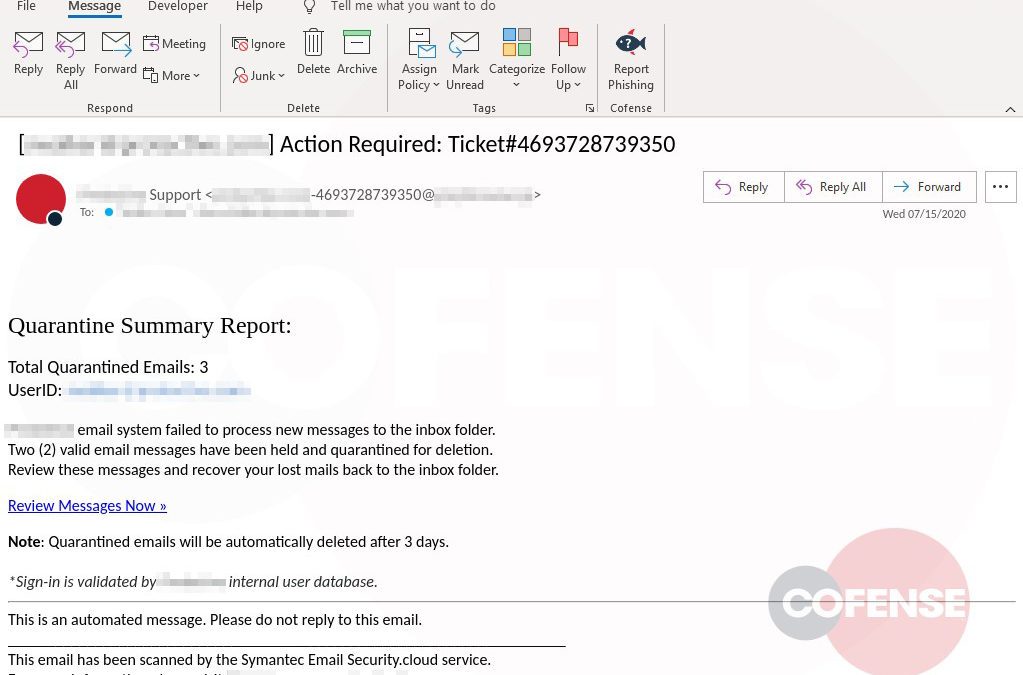
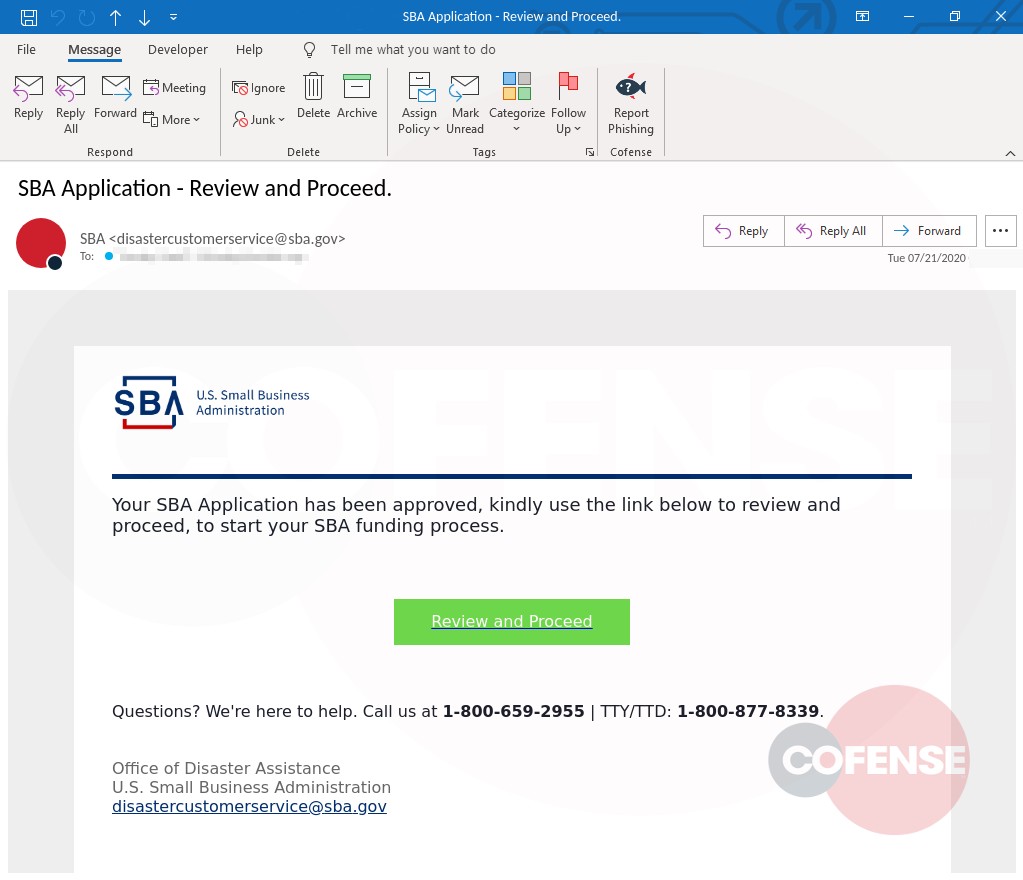
Figure 1: Phishing Email
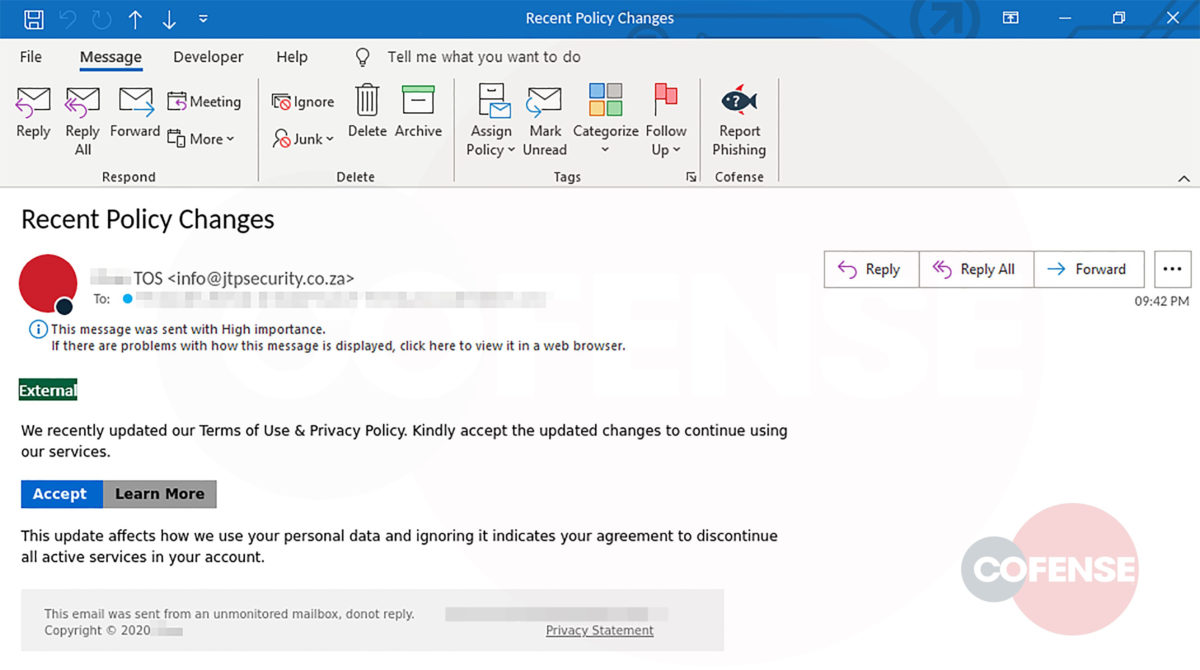
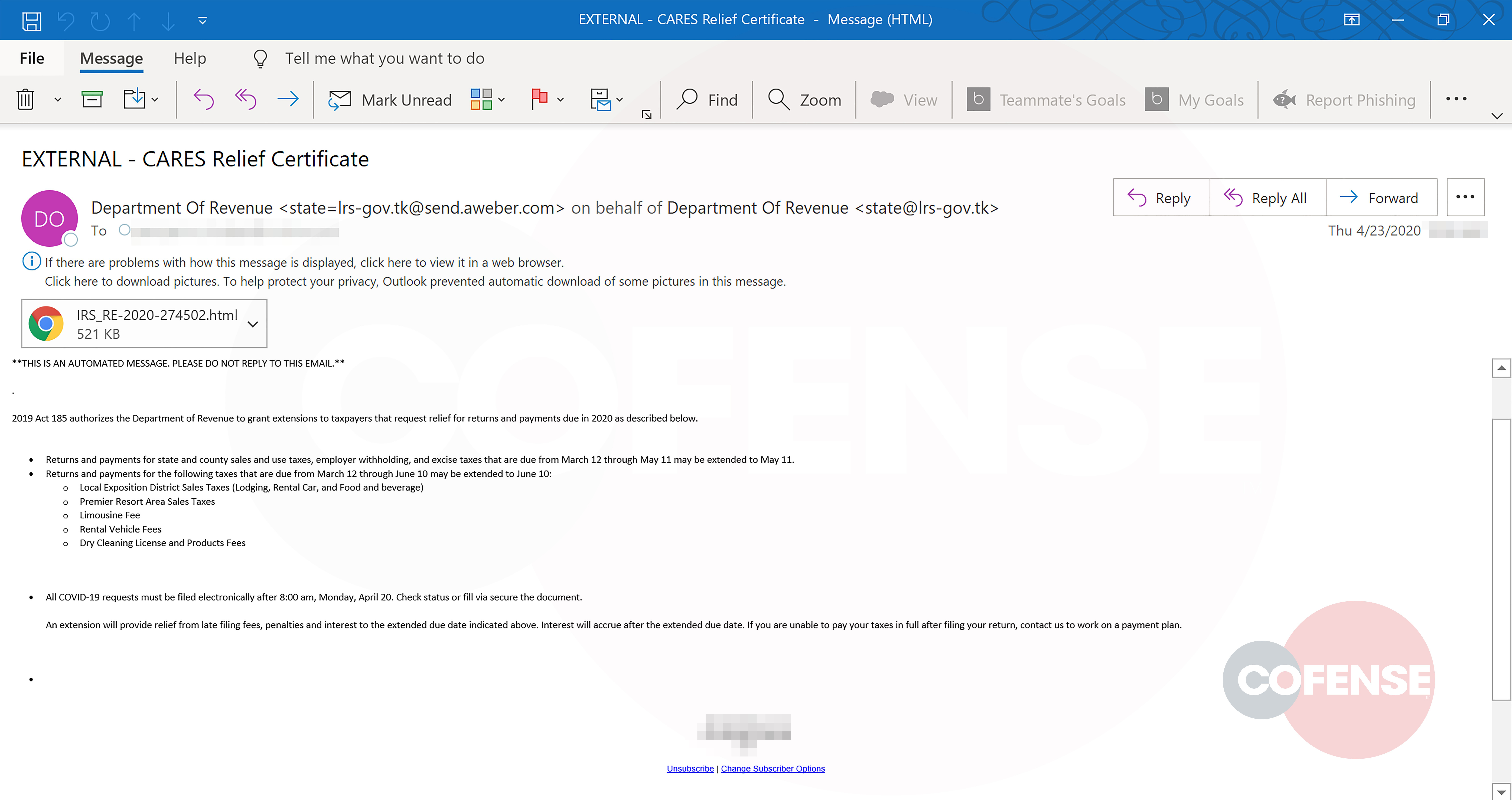
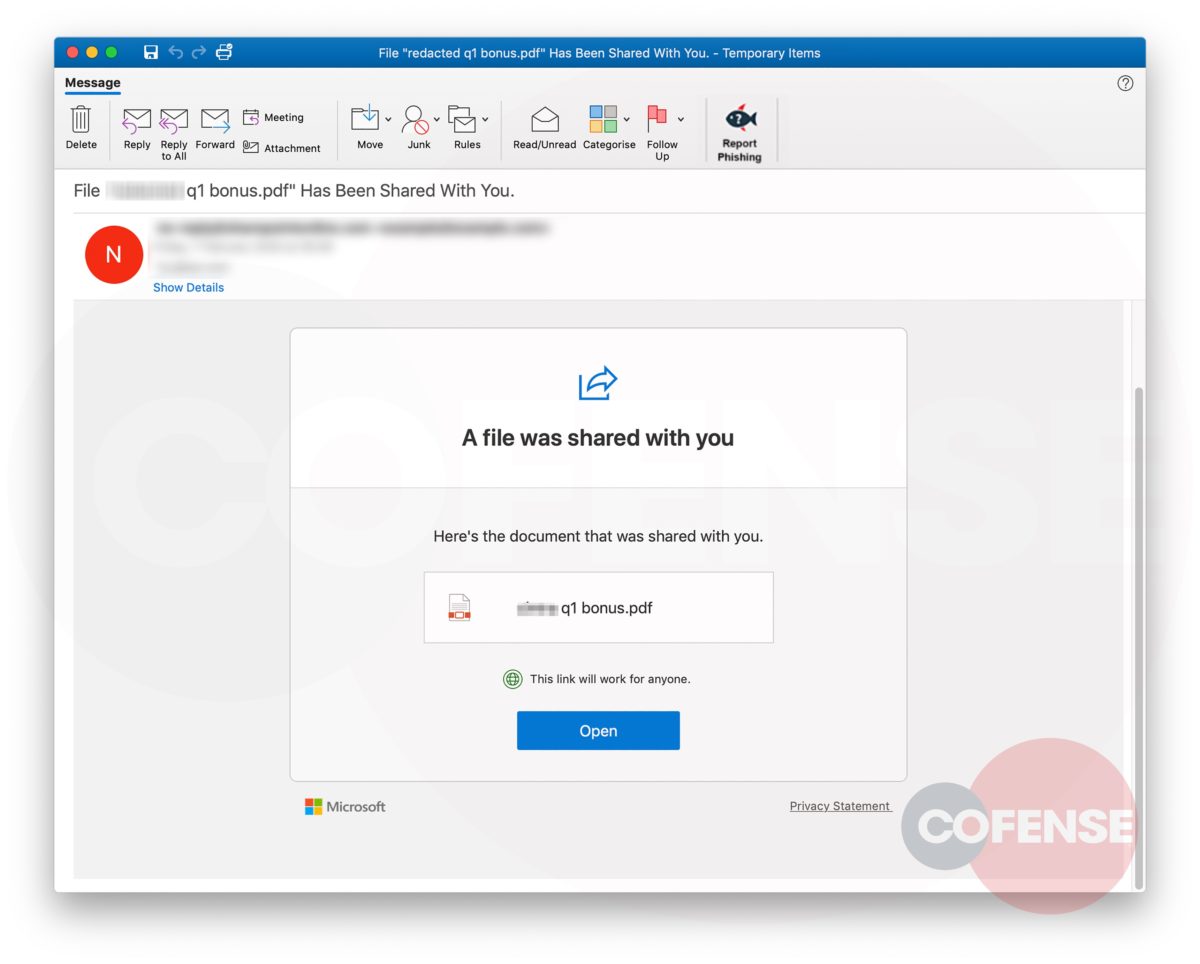
This campaign attempts to imitate the technical support team of the employee’s company and makes it appear as though the company’s email security service has quarantined three messages, blocking them from entering the inbox. It claims these messages failed to process and need to be reviewed in order to confirm validity. It even states that two of these were considered valid and are being held for deletion. This could potentially lead the employee to believe that the messages could be important to the company and entice the employee to review the held emails. Another social engineering technique the threat actor uses to lure the employee into interacting with the email is giving the messages urgency, asking the recipient to review them or they will be deleted after three days. Potential loss of important documents or emails could make the employee more inclined to interact with this email.
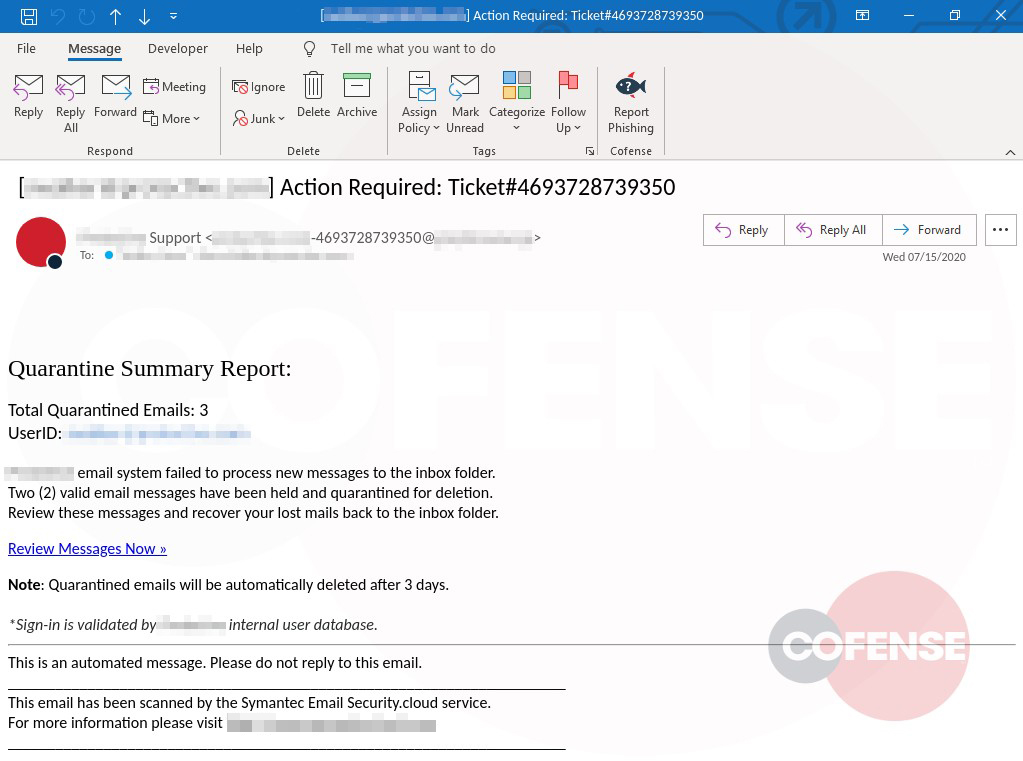
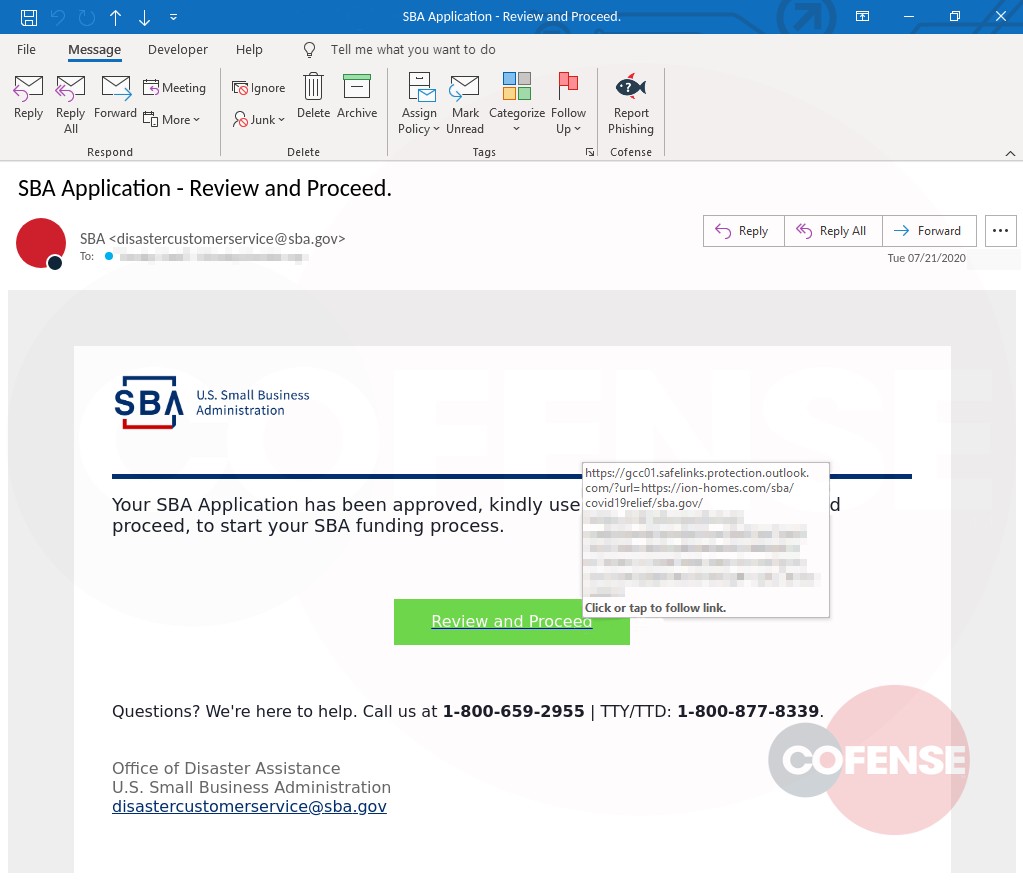
Figure 2: Phishing Email
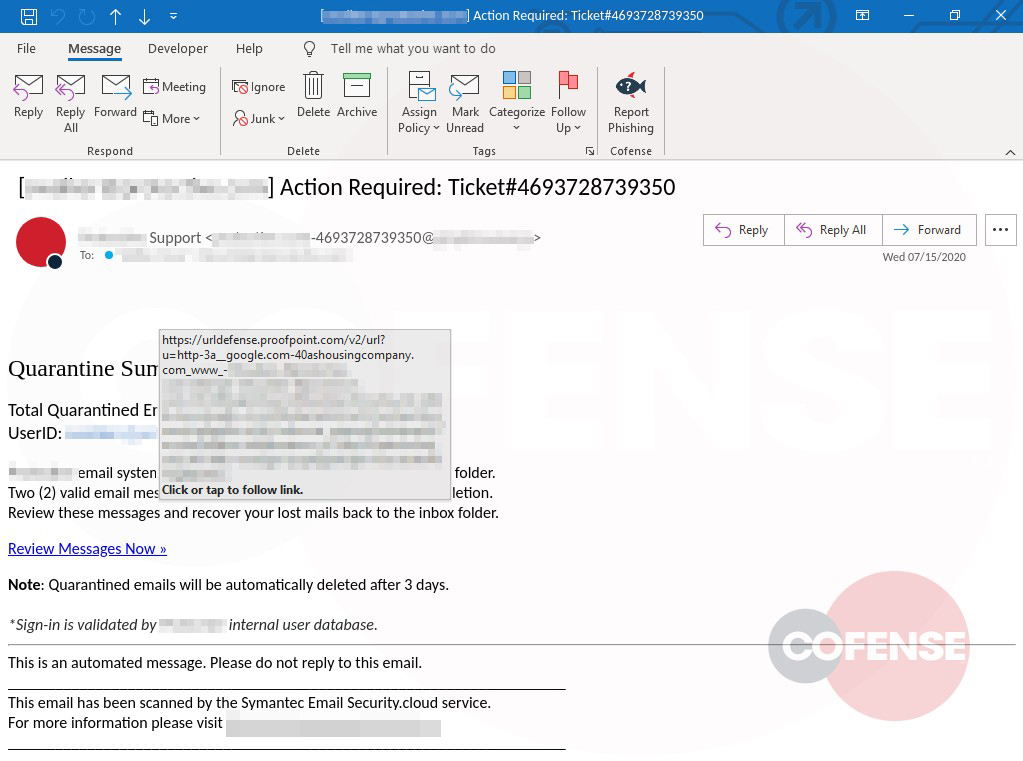
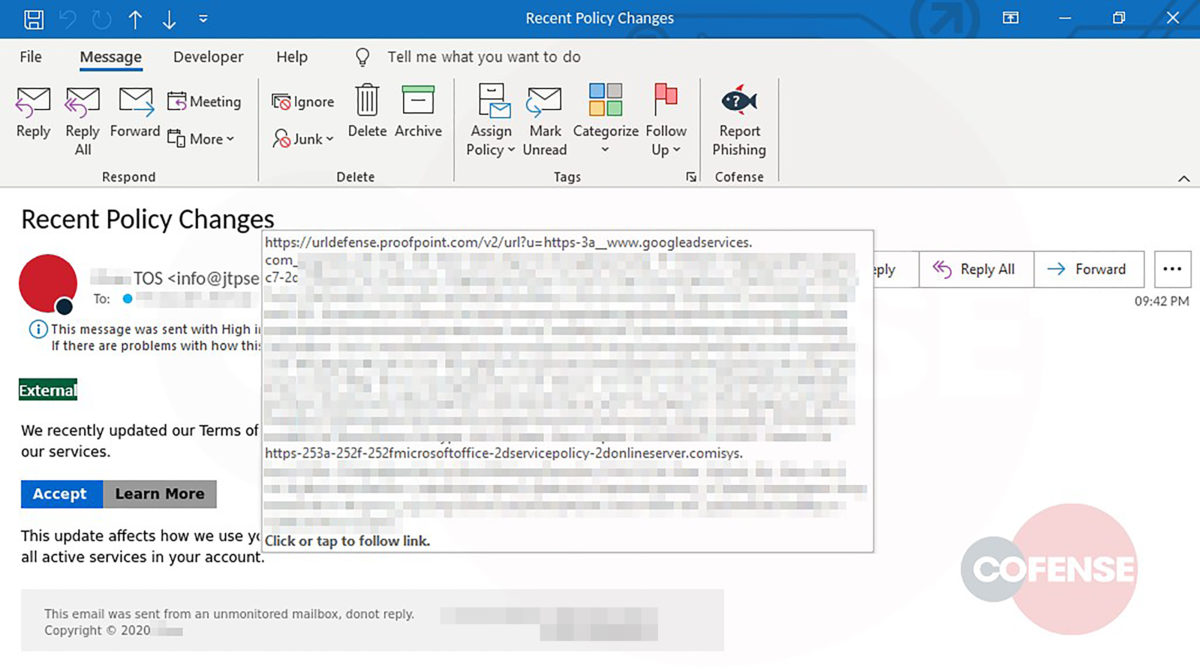
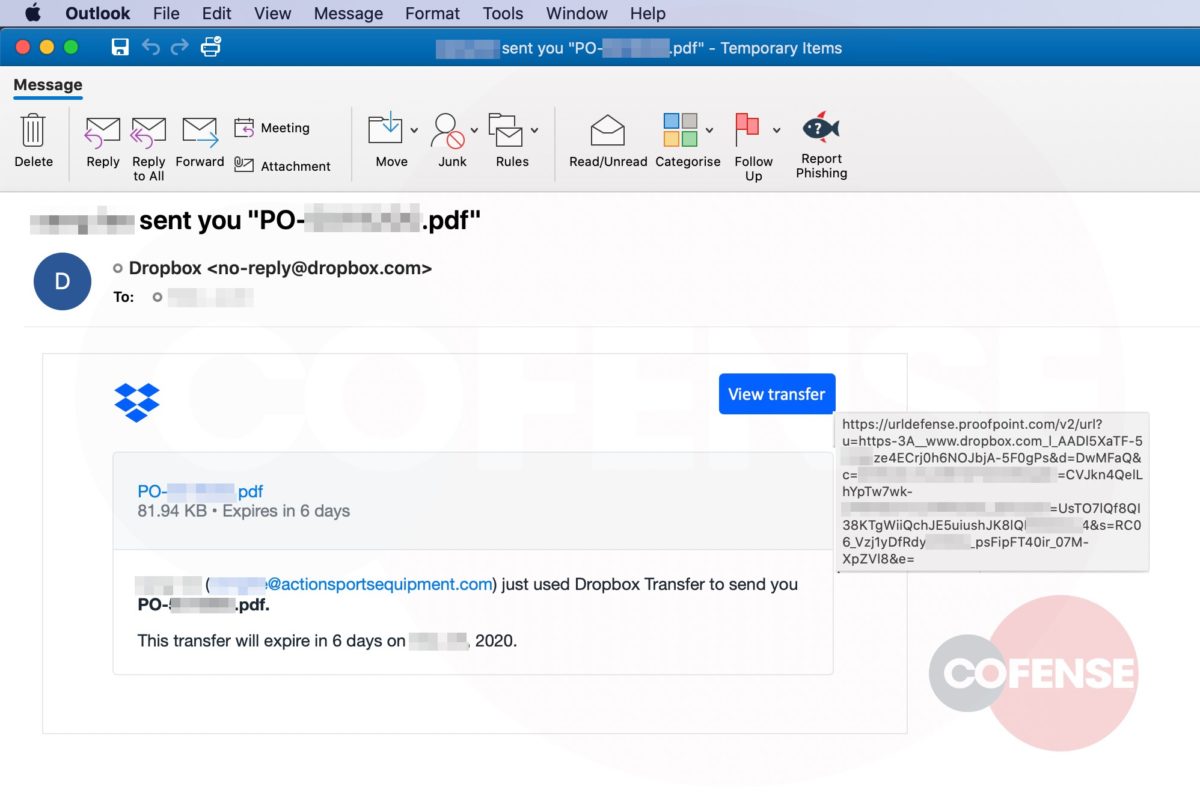
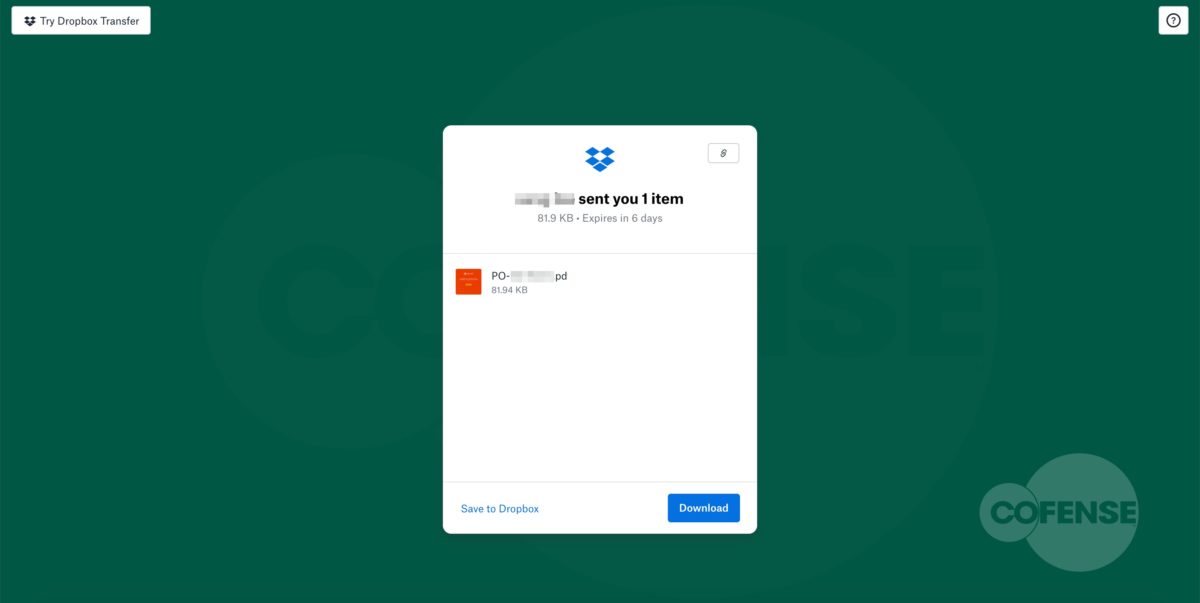
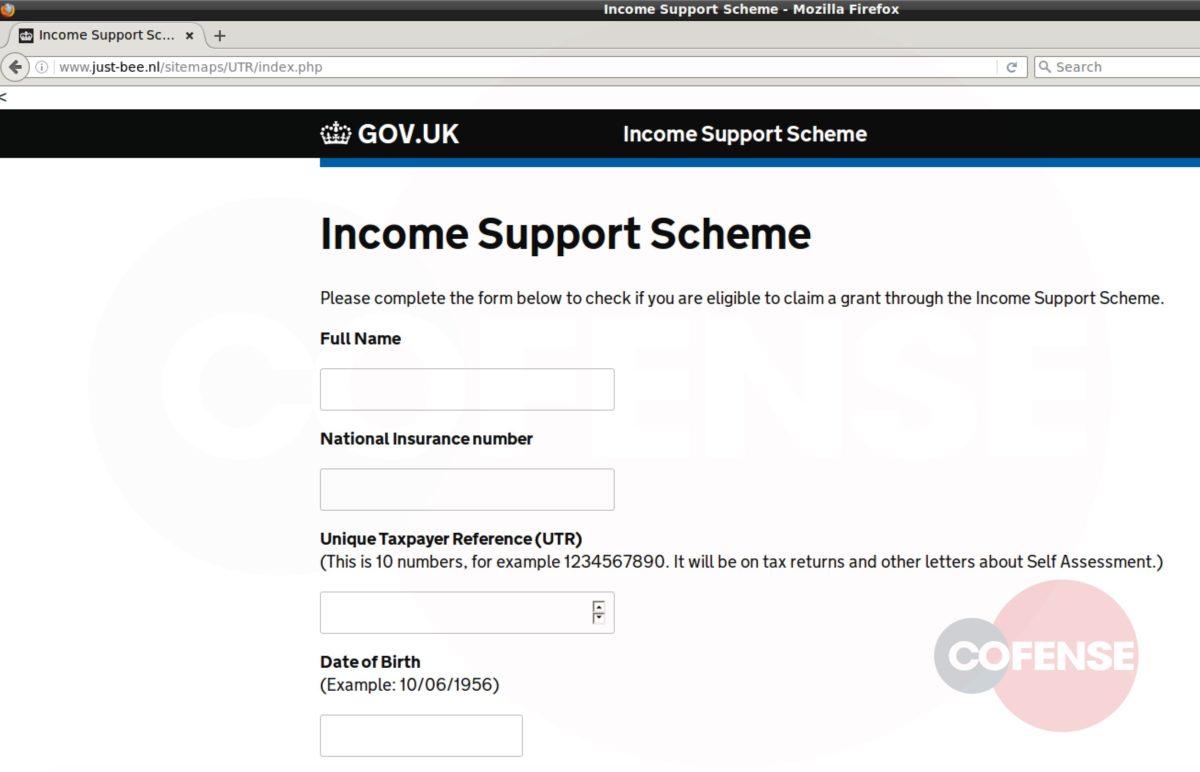
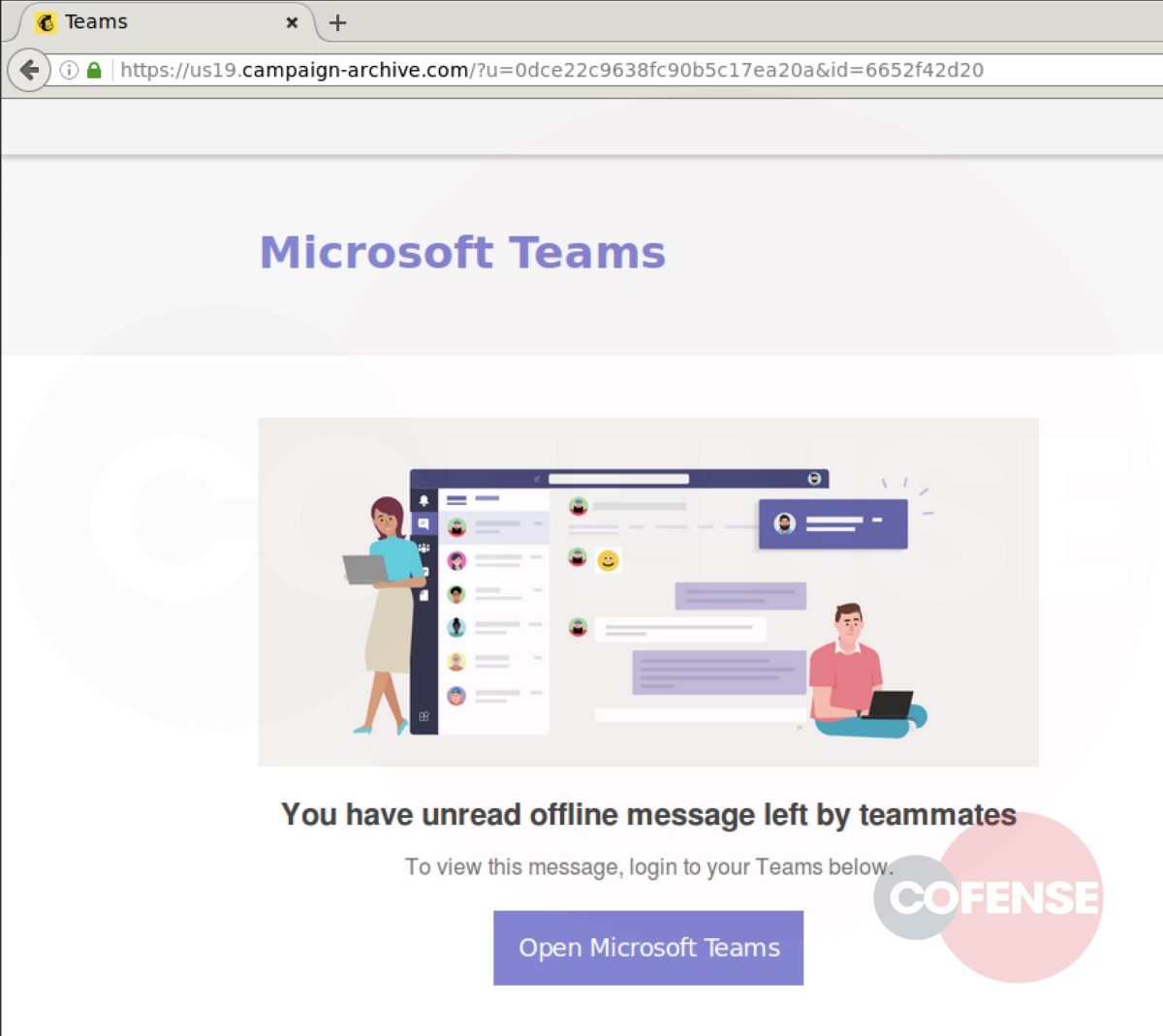
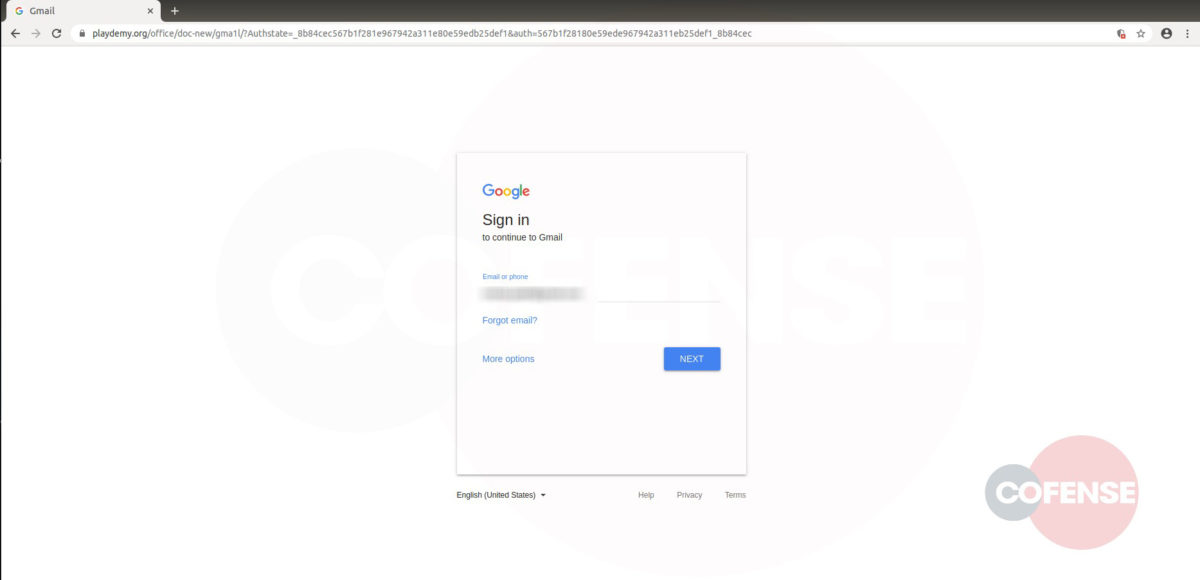
As seen in Figure 2, hovering over “Review Messages Now” shows the malicious URL. However, upon interacting with the link, the user will be directed to a phishing page unique to the employees’ company. Here is where this campaign uses advanced mechanics to make it appear even more legitimate.
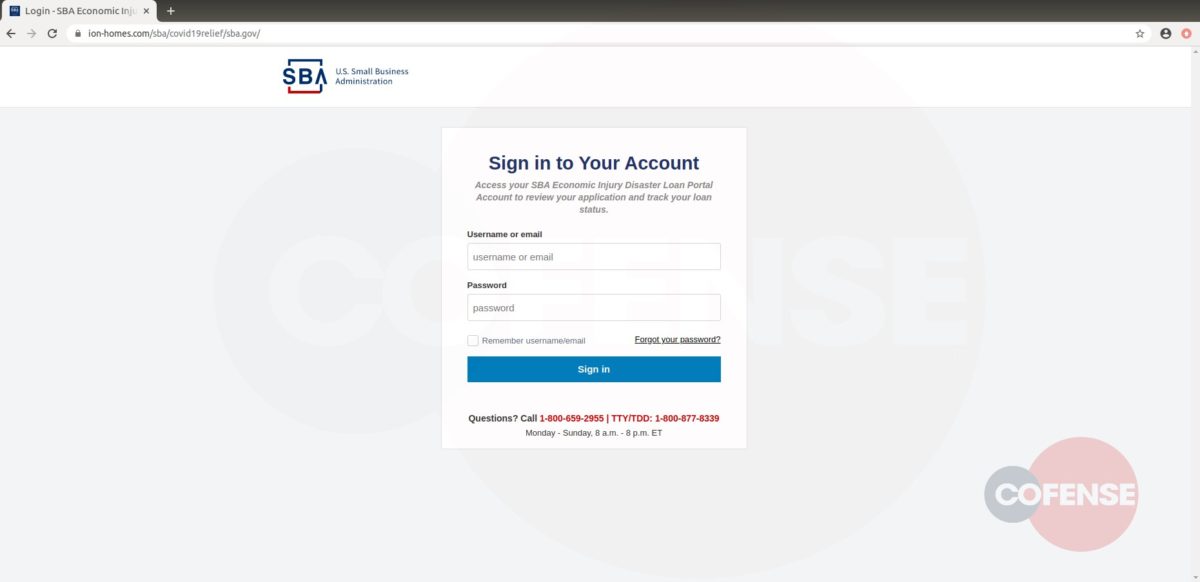
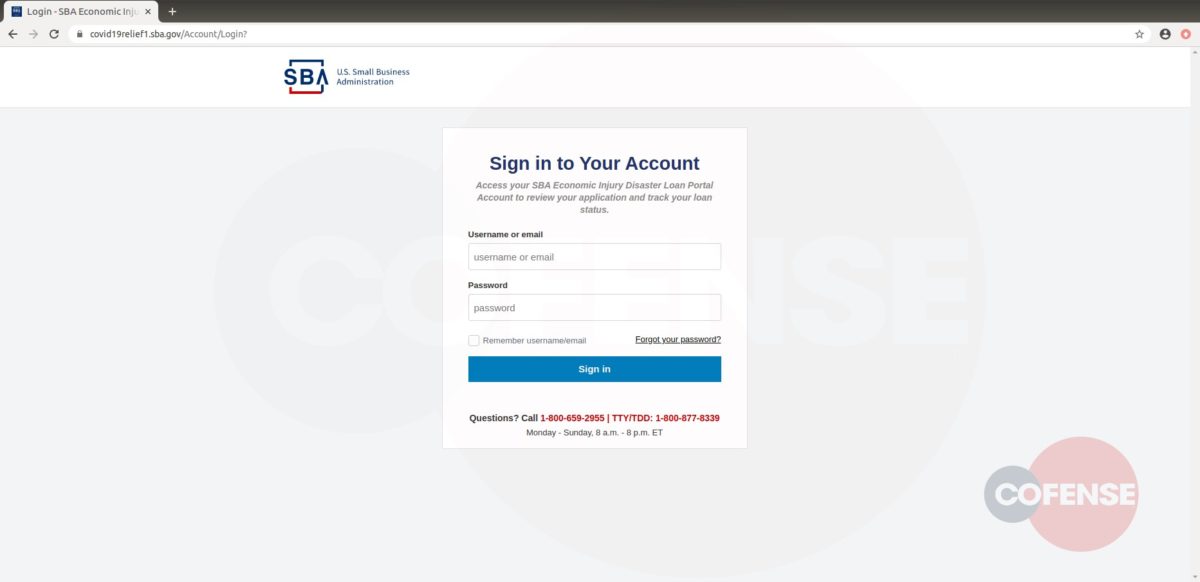
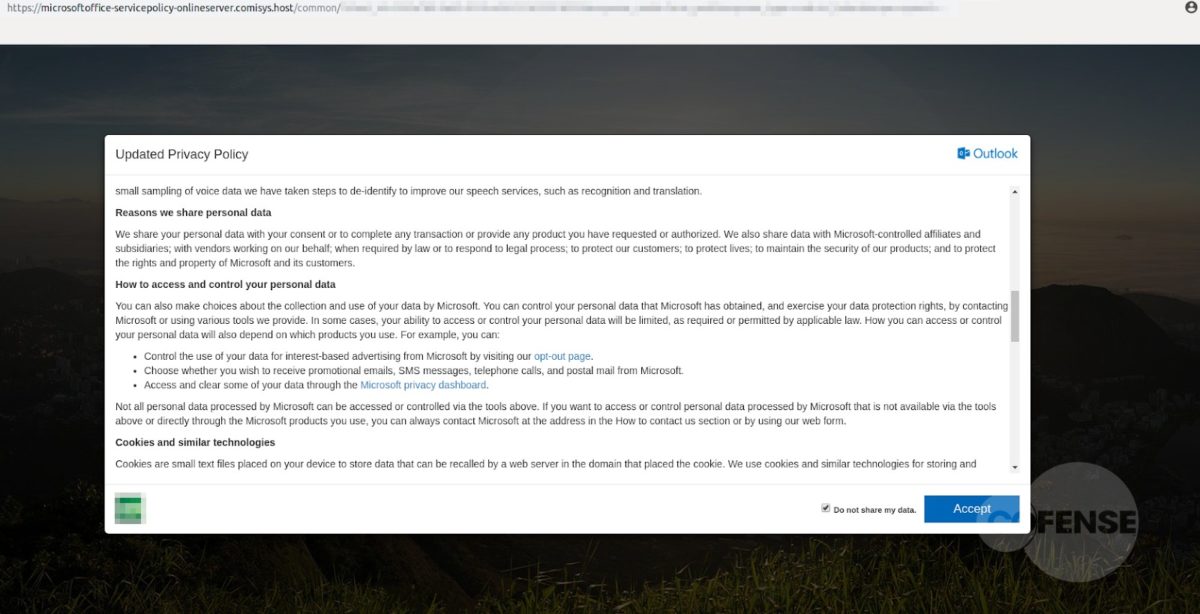
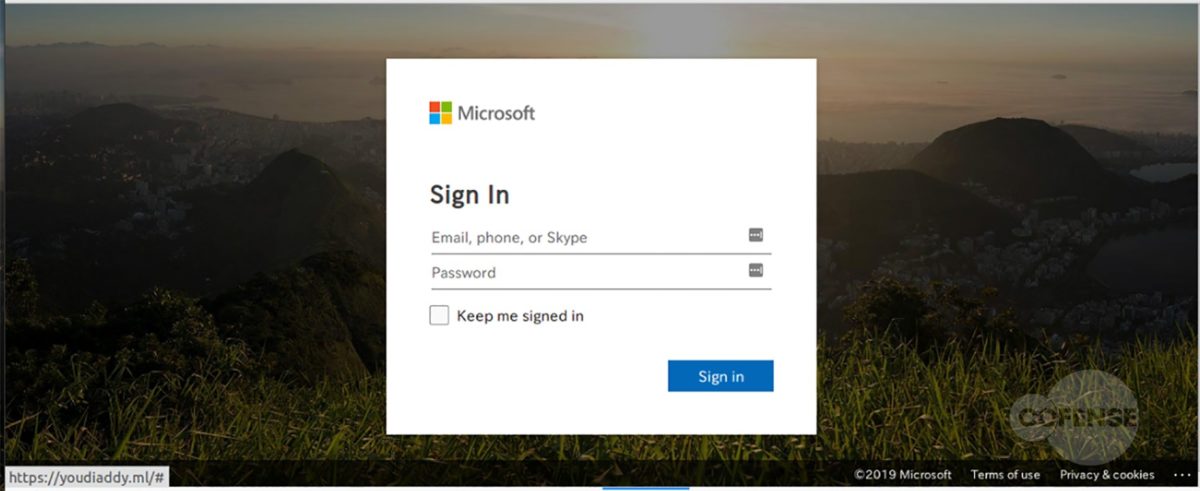
Figure 3: Cofense Phishing Page
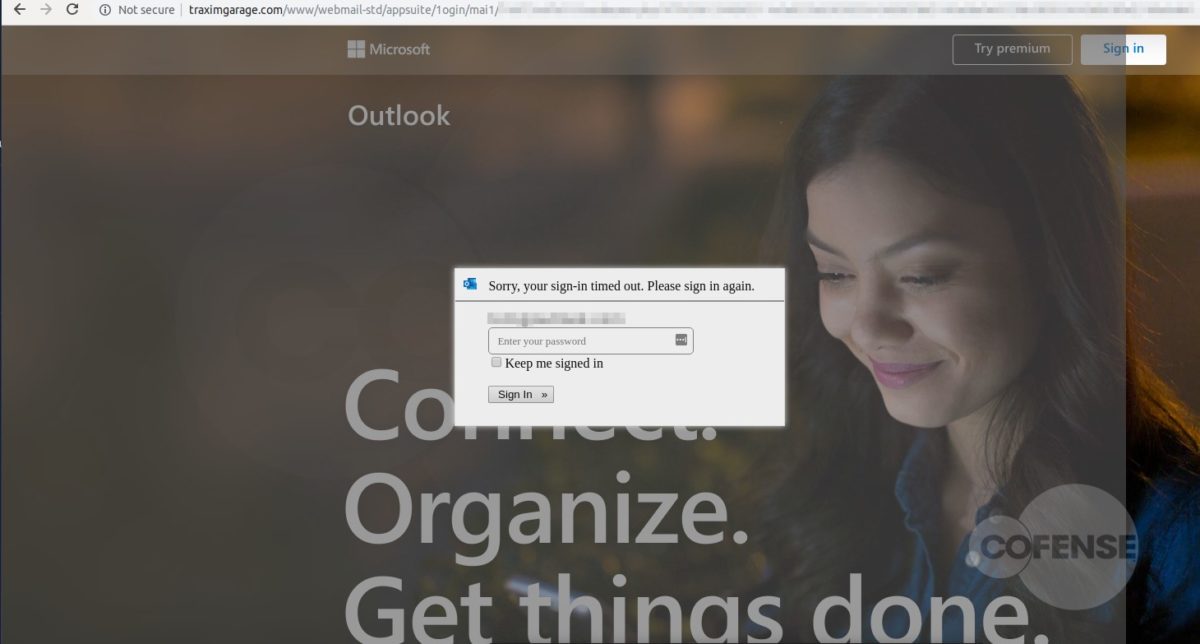
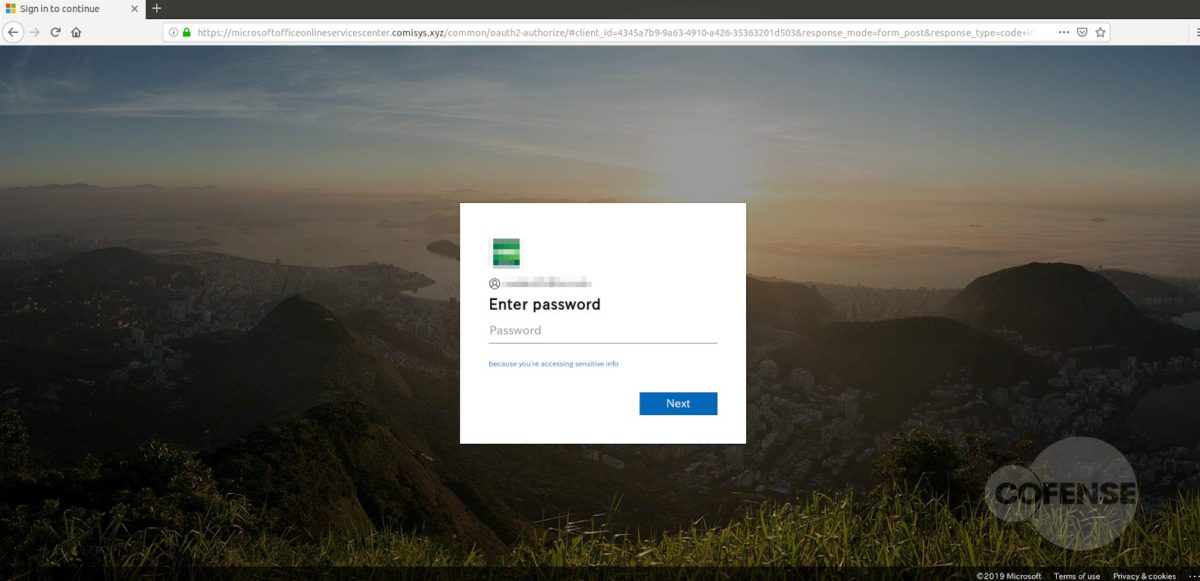
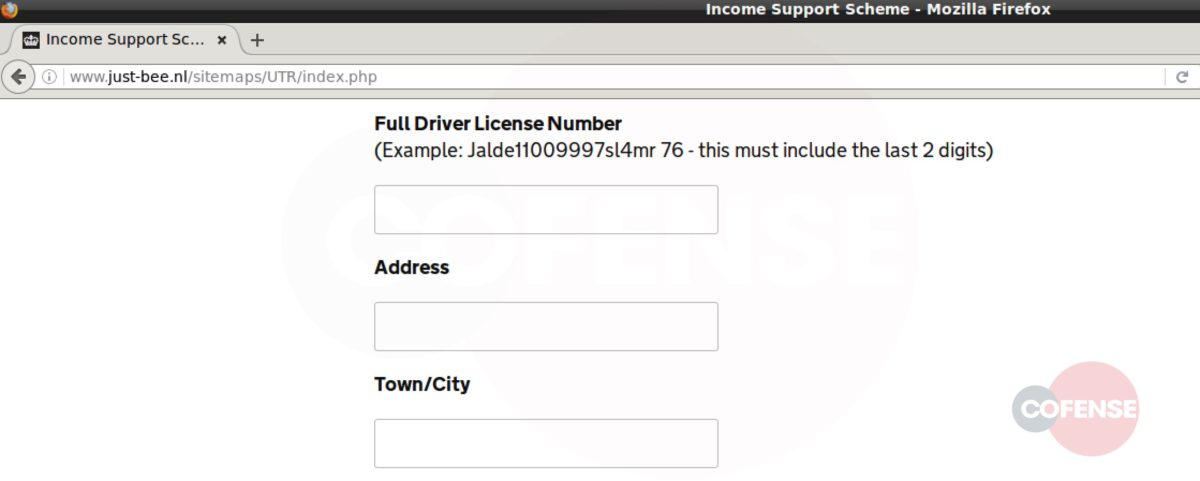
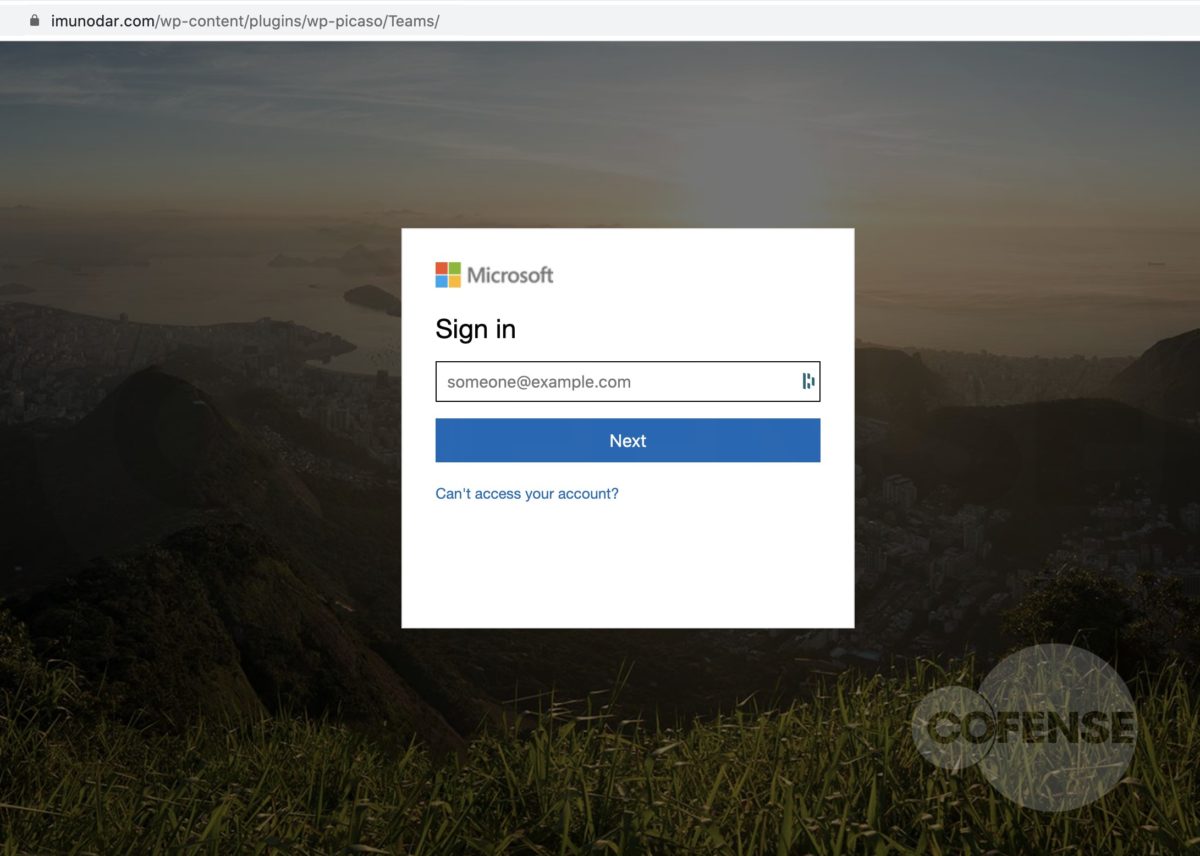
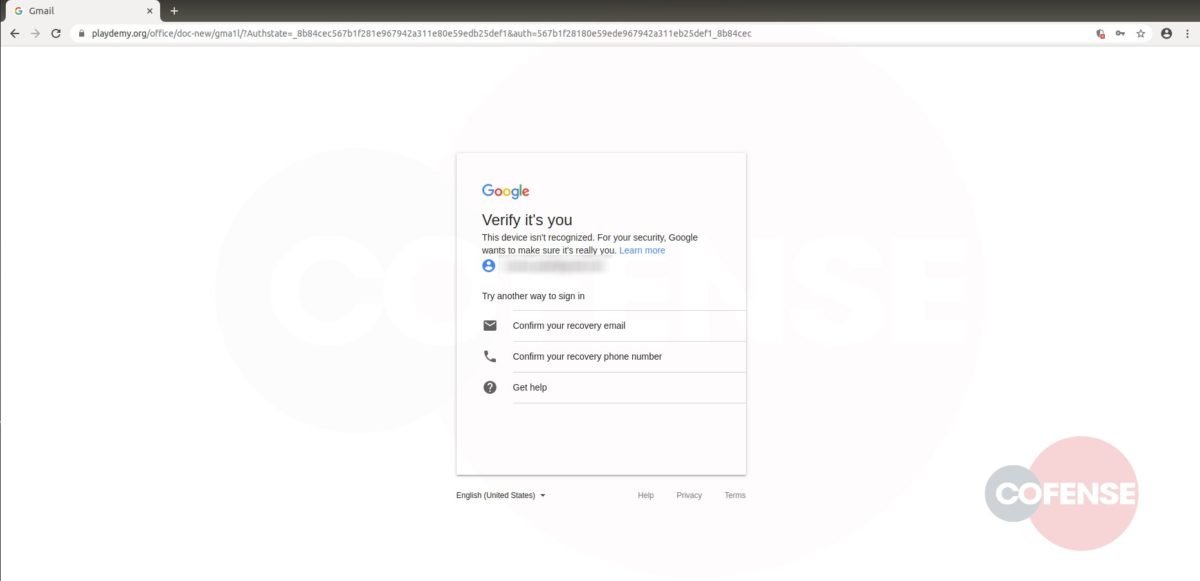
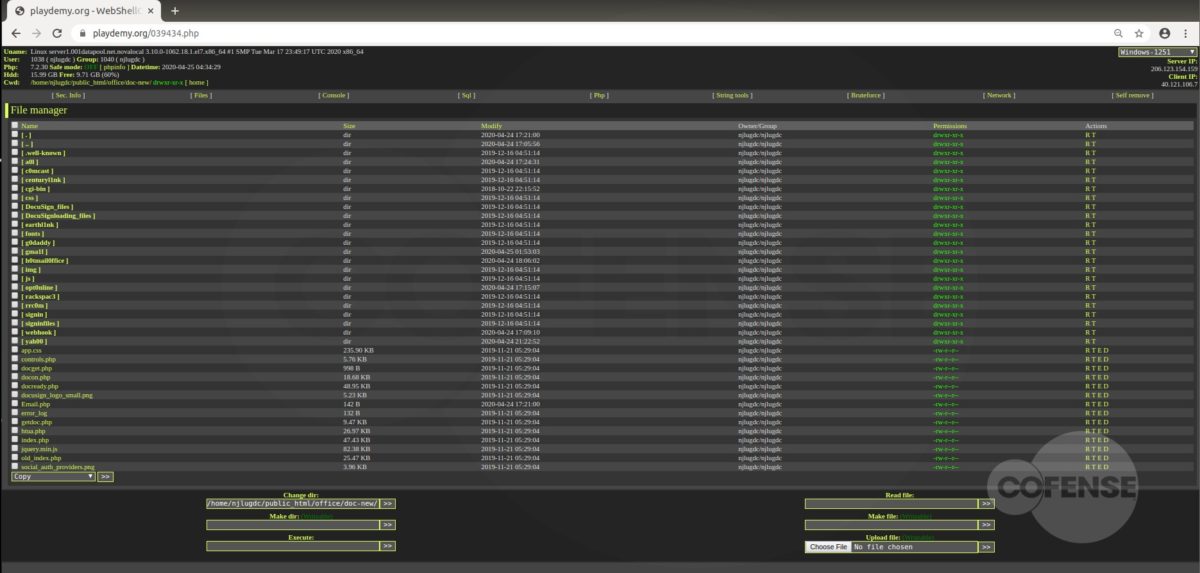
After interacting with the email, the employee will then be redirected to what appears to be a login screen on the company website (Fig 3). However, further analysis has determined that the page shown is actually the company’s website home page with a fake login panel covering it. This gives the employee a greater comfort level, by displaying to a familiar page. It is also possible to interact with this page by moving outside of the overlay, showing that it is the actual page they have seen and used before. The overlay itself is attempting to prompt the user to sign in to access the company account. The entered credentials are then sent to the threat actor, giving them access to the target’s company account.
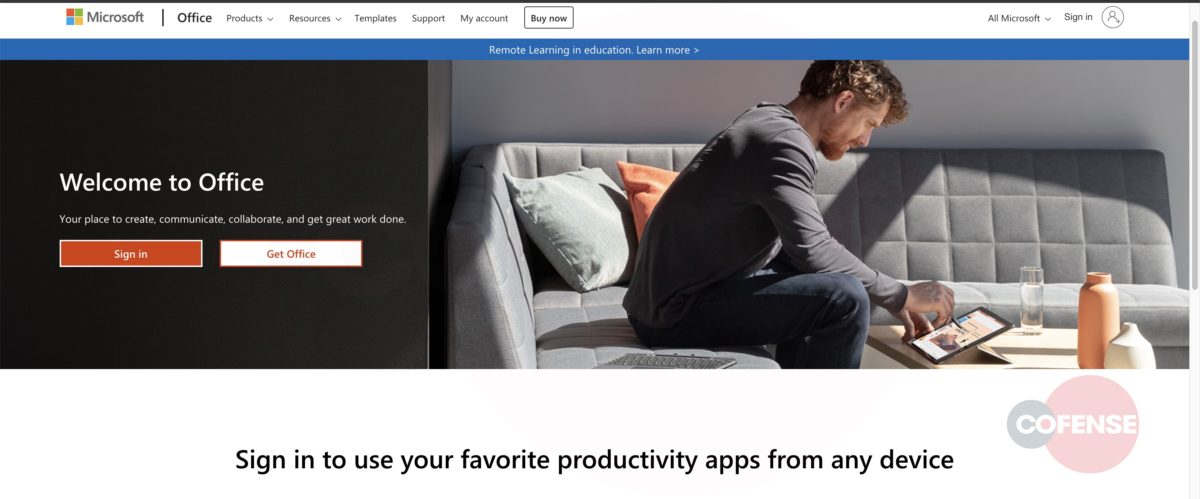
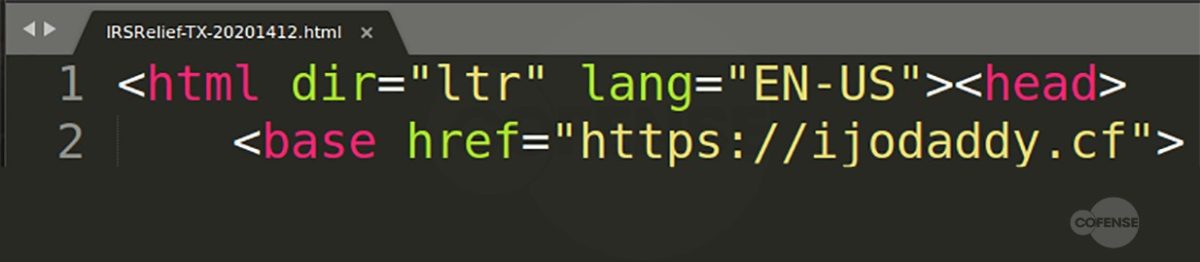
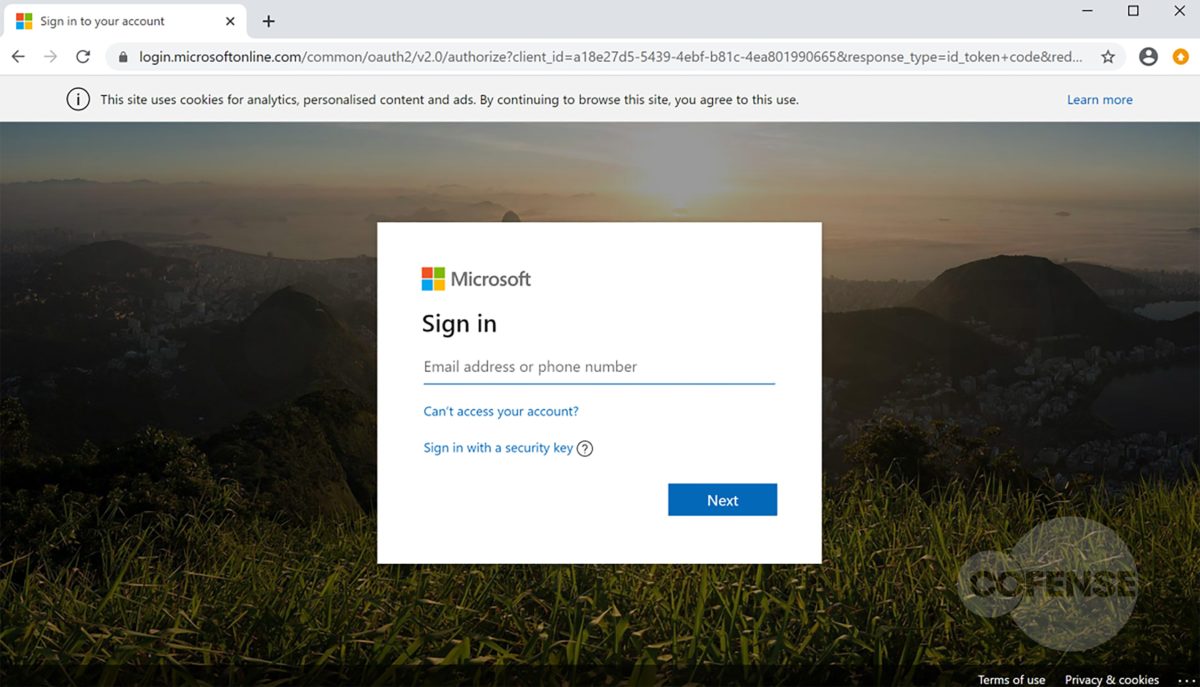
Figure 4: Microsoft Phishing Page
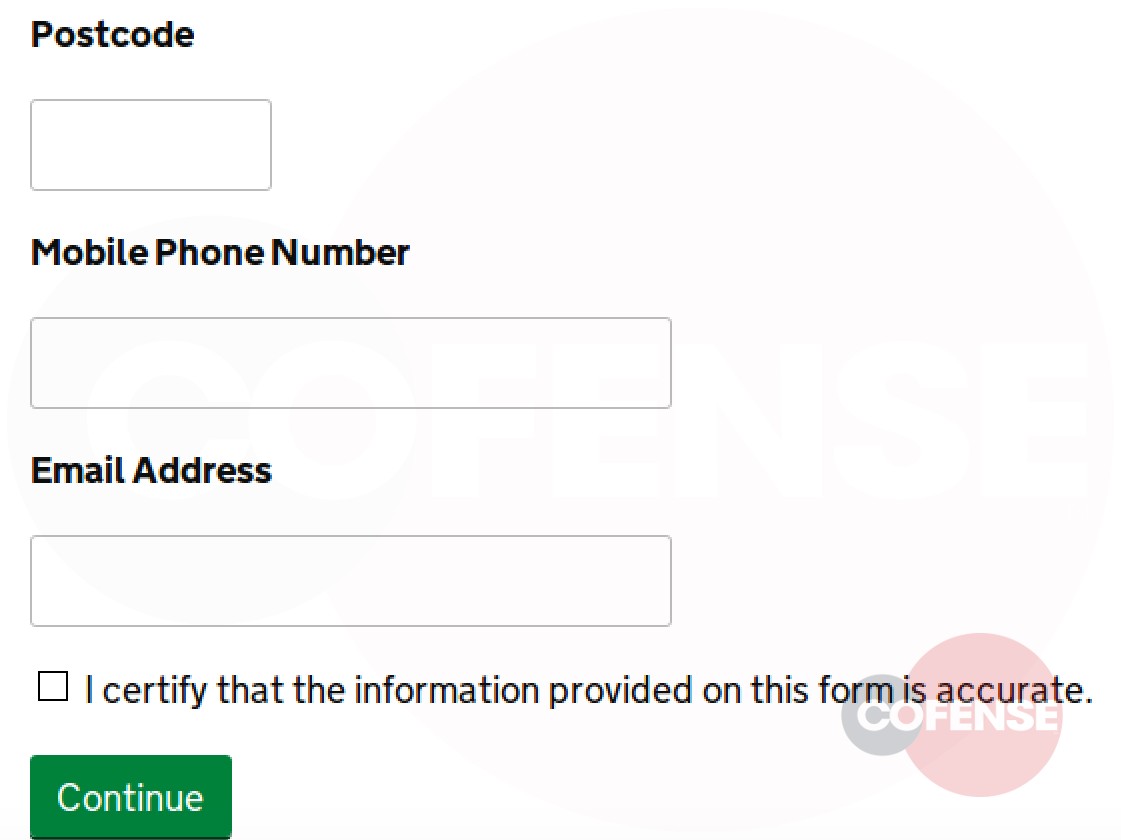
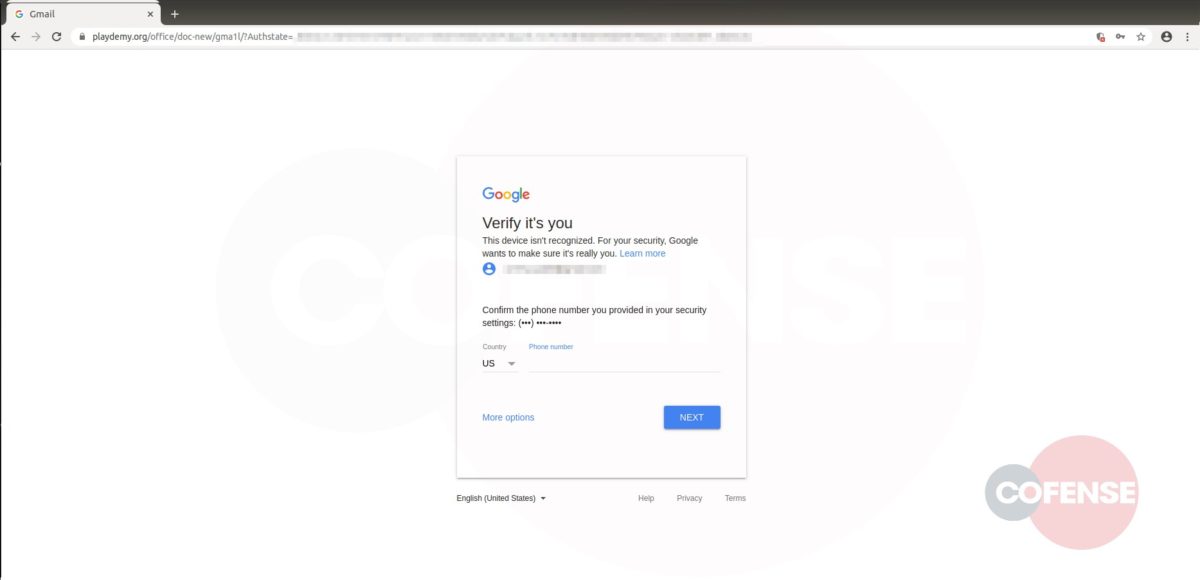
Based on the analysis performed by the PDC, it was determined that each link, while still going to the same base domain, uses specific parameters to determine which web page pull, then overlays the fake login panel on top. Depending on what company the threat actor is targeting, the link will populate the address of the original recipient of the email. Figures 3 and 4 are examples provided by entering an address, in this case Cofense or Microsoft. After the equal sign, the link will look at the domain of that address and pull the homepage. This campaign shows that threat actors can and will use any resource available to compromise business accounts.
HOW COFENSE CAN HELP
Cofense Resources
Cofense PhishMeTM offers a simulation template named Email Quarantine Report – Alternate.
| Network IOC | IP |
| hxxp://google[.]com@ashousingcompany[.]com/www/?email= | 104[.]27[.]158[.]208 |
| hxxp://traximgarage[.]com/www/webmail-std/appsuite/1ogin/mai1/ | 185[.]68[.]16[.]137 |