By Kaleb Kirk, Cofense Phishing Defense Center
Over the last few years, businesses have been getting serious about updating their corporate desktop images. For quite some time, Windows 7 has been the predominant operating system (OS) for many workplaces and environments. Windows 10 was released in 2015, yet many companies are just now making the transition. With that comes the pains of upgrading end users’ machines. Standardizing a corporate desktop image is arduous with complicated edge cases that must be considered for all the hardware variants. The job is further complicated when third–party software has yet to officially support a new OS. This explains why enterprises wait, sometimes for years, before taking the plunge. Unfortunately, these delays give the bad guys time to refine exploitation techniques on older operating systems lacking the latest architecture.
The phishing lure below preys on the victim’s anxiety about losing productivity while their computer is upgraded. Comically, the attacker uses a colorful list of benefits the end user receives to get them to take the bait. Will we see an uptick in this phishing lure? It will depend on the success rate of this theme. Time will tell.
Figure 1-2: Email Body
The subject references a Windows upgrade, but there is also something else manipulative: the inclusion of the “RE:” before the rest of the subject. Internal email about company meetings, news and IT upgrades are common. Prefixing the “RE:” may instill a sense of urgency by leading the user to believe they have missed a prior communication about the upgrade.
We look at phishing emails that bypass commercial gateways all day, every day. Most of them are hastily slapped together. This lure needs improvement, but it’s not completely awful. We give this threat actor two gold stars for the table with made-up laptops, fake serial numbers, building, etc. It applies a good sense-of-urgency ploy using the highlighted “Today,” and the body doesn’t have obvious grammar or spelling errors. Again, not completely awful.
How can this attacker upgrade this lure from a C- to a B+? This email would be more believable if the sender were more generic. “Helpdesk,” for example. We obfuscated the From: line of the compromised account “Genadiy” which was not from the intended victim’s company domain, and certainly not from their IT department. The intended victim unfortunately doesn’t have a clean way to easily know the true underlying URL because it’s annoyingly masked by Proofpoint’s URL Defense (which, ironically, would not have defended the user because, once clicked, the phishing page loaded instantly).
Figure 3: Credential Phishing Page
Figure 3, above, shows the loaded credential phishing page. This page gets a D- for lack of effort. They wasted a valid SSL certificate on a terrible version of an OWA login page.
This phish closes out cleanly by redirecting the intended victim to a Microsoft page about the discontinued support of Windows 7 (but still leaves the target worried about their OS upgrade).
Figure 4: Final Redirect
Attackers have been using the “time to upgrade your out-of-date software” ploy for years. With Windows 7 ending official support, it won’t be surprising if we see a flurry of better versions of this phish in the future. Hopefully your vigilant users know that “Genadiy” (from a company that isn’t yours) doesn’t upgrade an operating system “Today,” and via email. Cheers.
| Network IOC | IP |
| hXXps://app[.]getresponse[.]com/site2/ken23456789765?u=w3DxF&webforms_id=hlvzr | 104[.]160[.]64[.]9 |







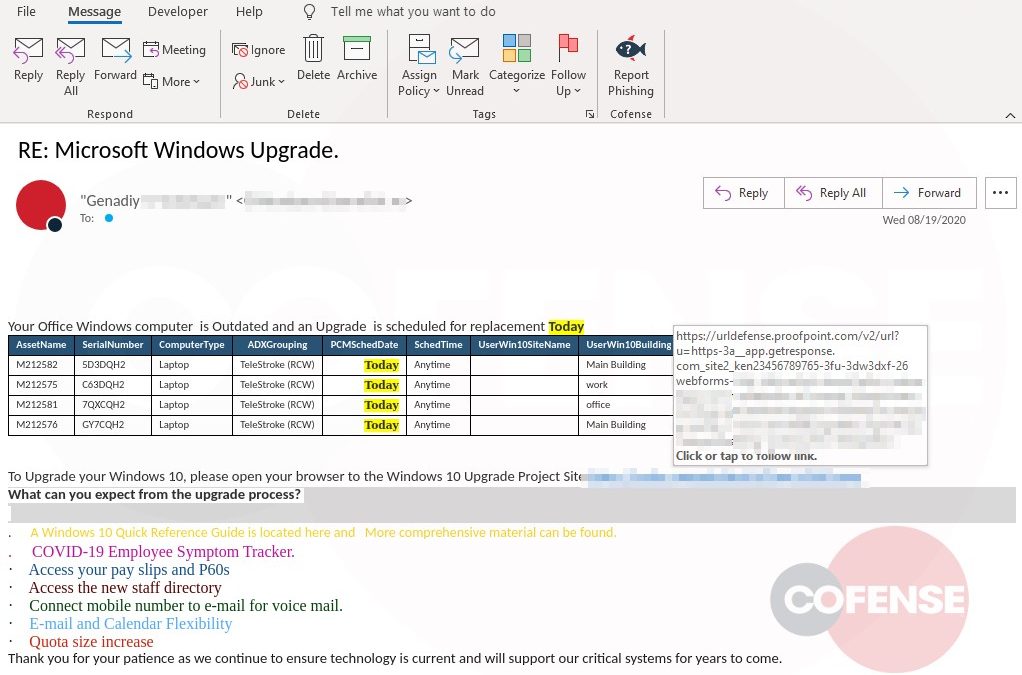
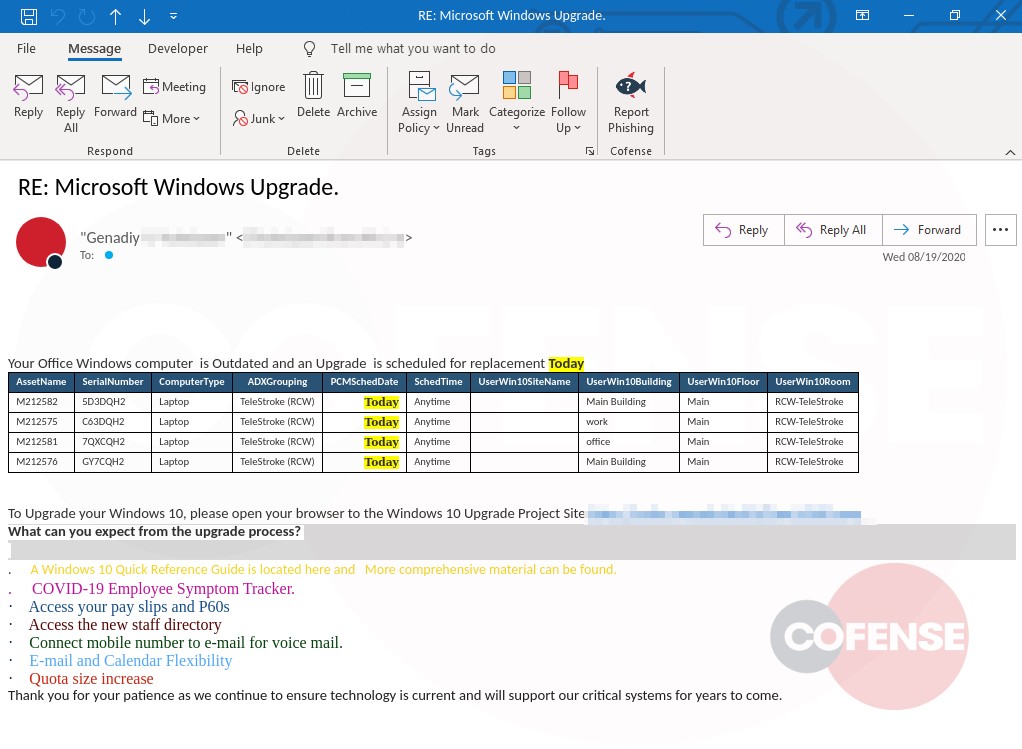
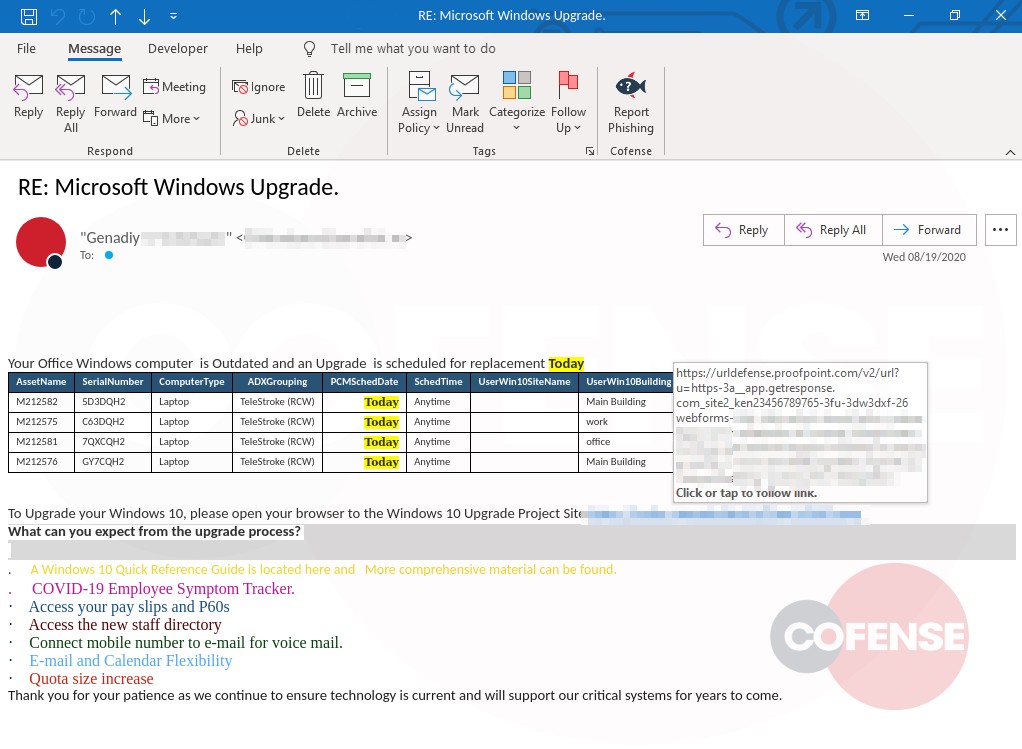
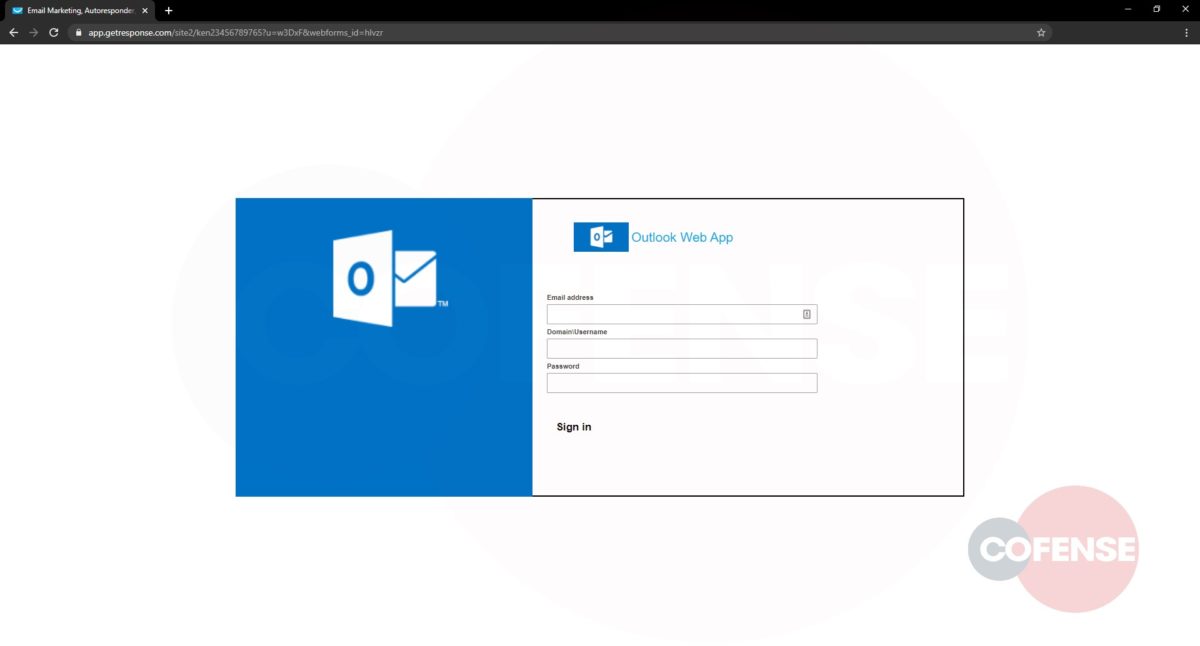
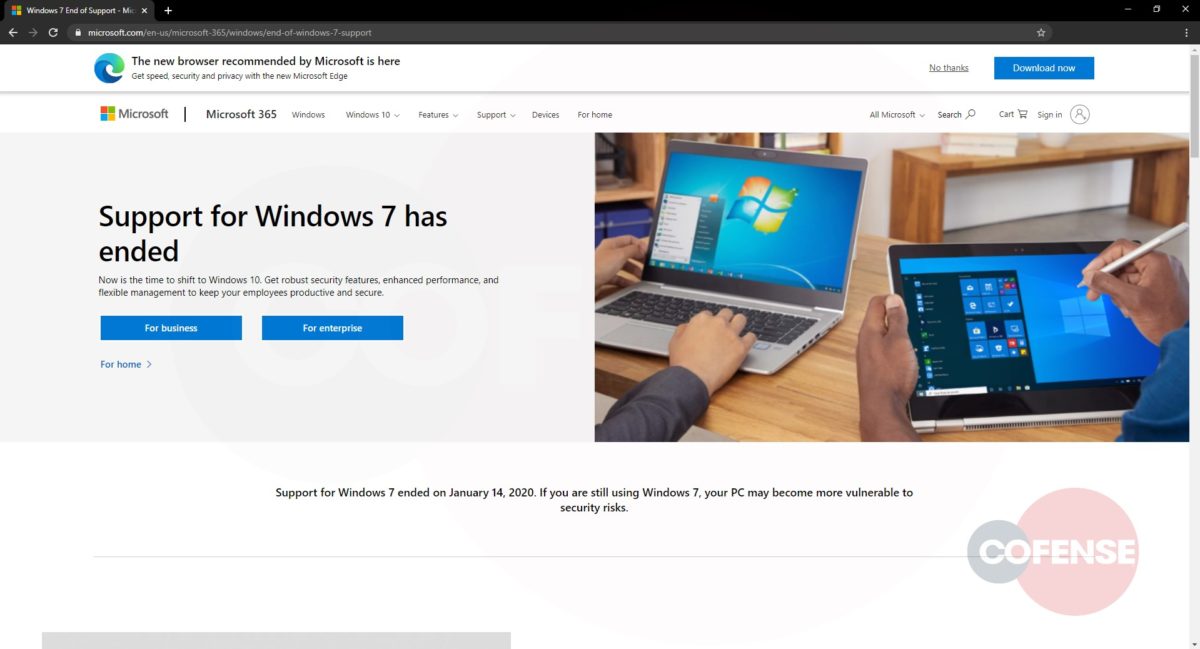




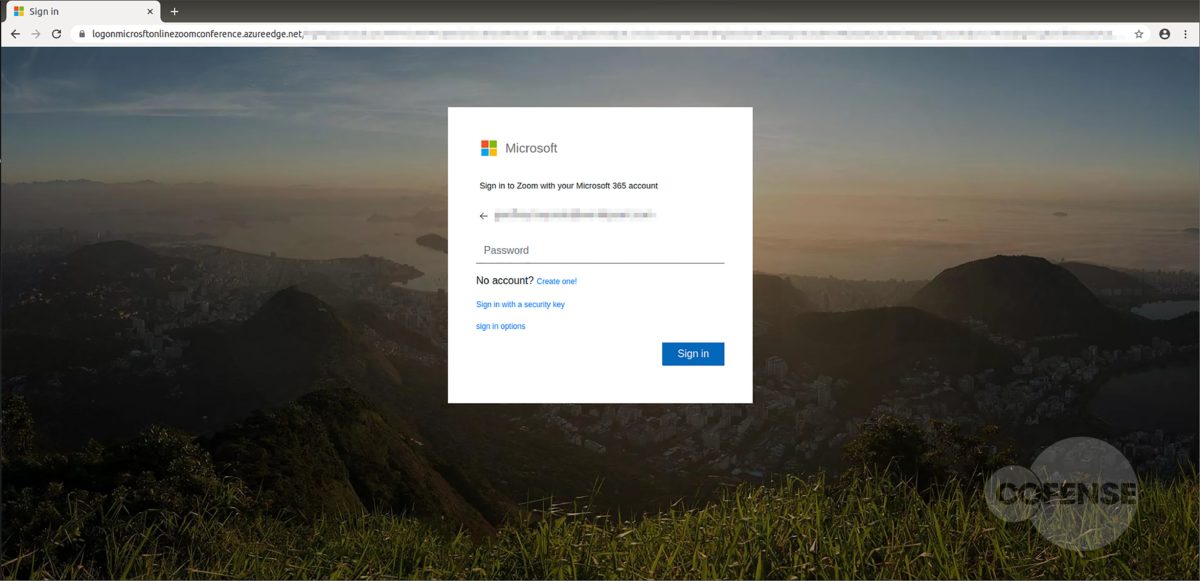
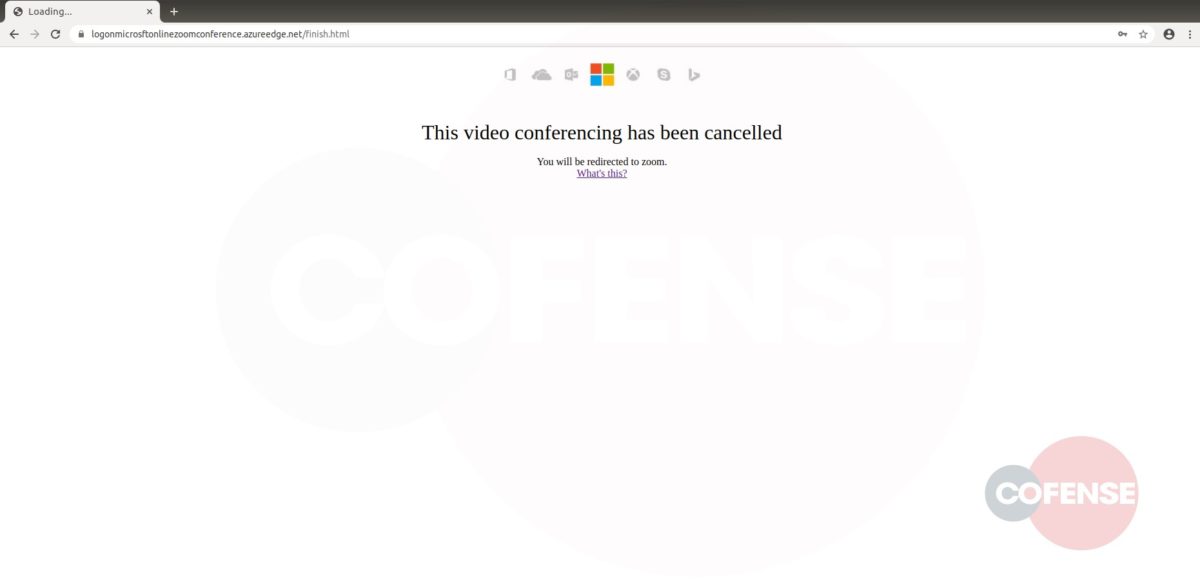
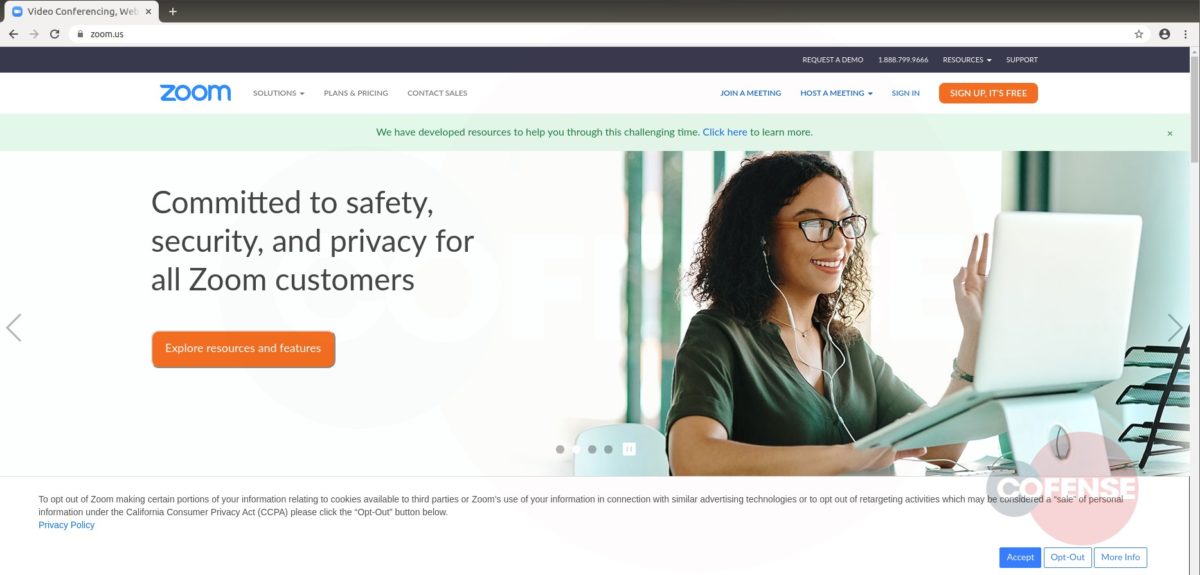

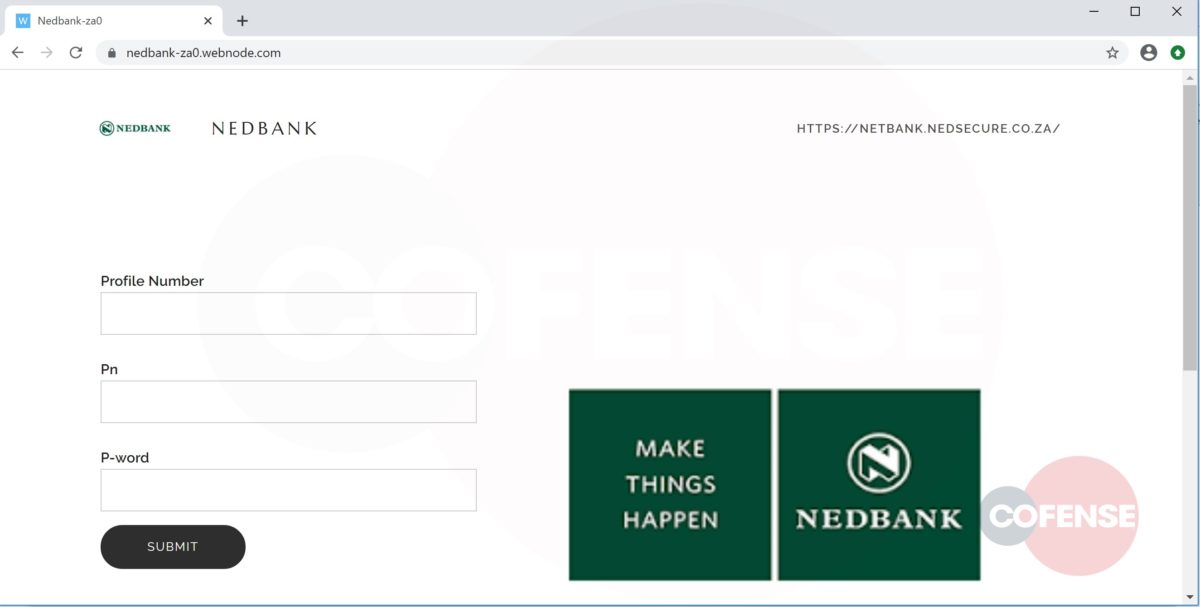
 Fig 5. Legitimate page
Fig 5. Legitimate page 